Are you looking for a secure, efficient, and cost-effective solution to manage your Windows systems? If so, you may have heard of Windows Remote Management (WinRM). WinRM is a Microsoft implementation of the WS-Management protocol, which is an industry-standard Simple Object Access Protocol (SOAP)-based, firewall-friendly protocol that allows interoperation between hardware and operating systems from different vendors.
WinRM provides an excellent way to remotely manage Windows systems in a secure and cost-efficient manner. It allows administrators to access systems remotely using any platform (Windows or other OS), run remote commands on multiple systems simultaneously, or access data from multiple sources at once. The added advantage is that WinRM does not require any additional software to be installed on the system.
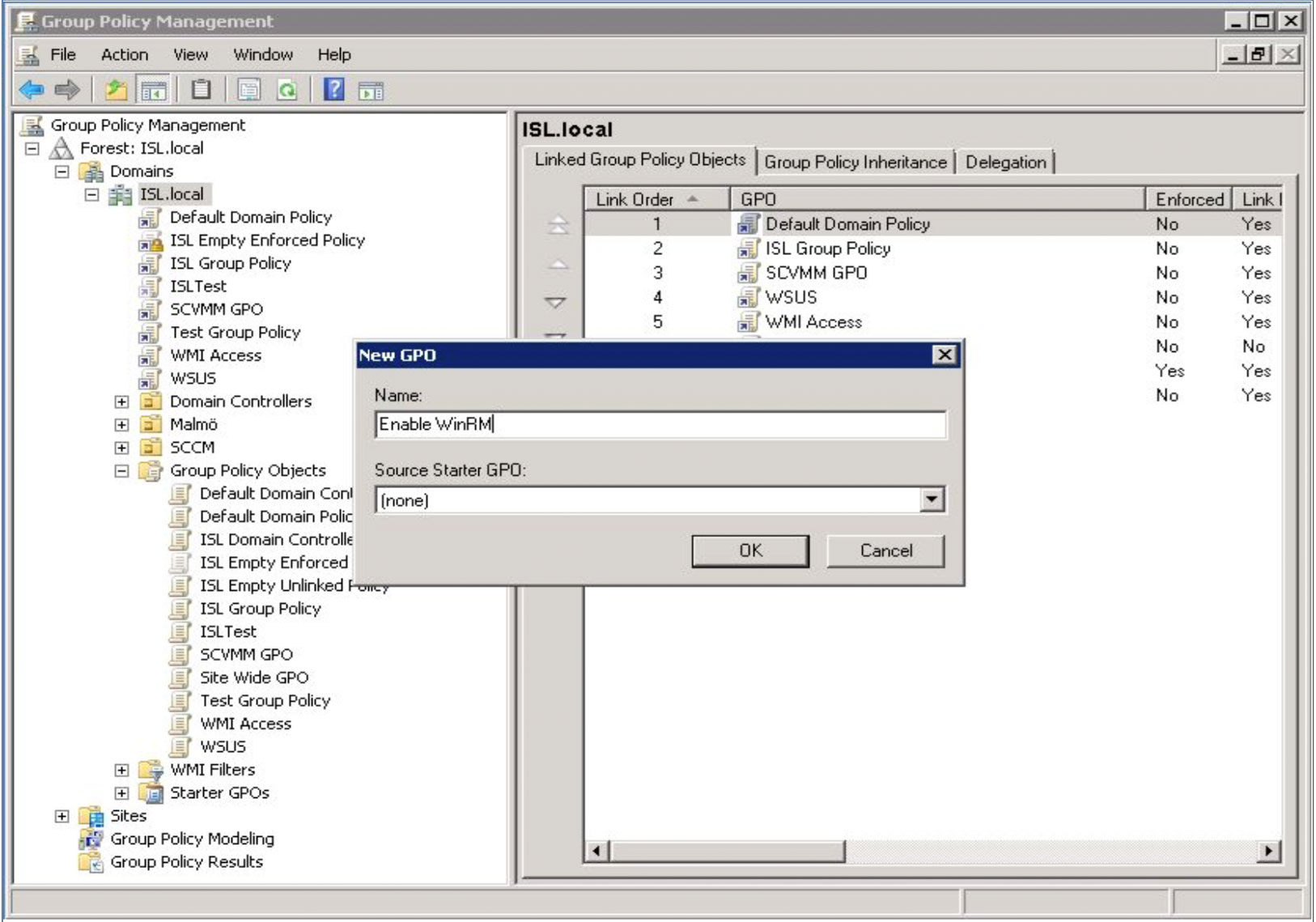
In order to use WinRM, administrators need to first create a Group Policy object for their domain. This includes enabling WinRM in the Group Policy settings and making sure the WinRM service is set up to start automatically. Additionally, they need to trust all hosts in the WinRM environment and open the HTTP port in the Firewall using Netsh advfirewall firewall add rule command.
Once configured correctly, administrators can then begin managing their Windows systems remotely using the PowerShell scripting language. This includes running scripts on multiple computers simultaneously or executing remote tasks such as creating users or assigning permissions. This makes it easier for IT teams to manage their Windows environment without having to physically visit each machine.
Overall, WinRM provides an effective means of managing Windows systems remotely with fewer security risks and lower costs than traditional methods. It also eliminates the need for installing additional software on client machines as well as reducing IT overhead associated with visiting multiple sites for management purposes. With its cost-saving potential and ease of use, it’s no wonder why more organizations are turning towards WinRM for their remote management needs!
The Purpose of WinRM
WinRM is used to enable secure communication between remote computers, allowing administrators to manage them remotely. It is an ideal solution for managing Windows-based servers, workstations, and applications, as well as for automating administrative tasks. WinRM can be used to execute commands on remote machines, transfer files between systems, and configure services. It can also be used to run scripts that perform various system administration tasks, such as creating users or managing services. Additionally, WinRM can be used to deploy applications from a central server to multiple remote computers. WinRM also provides the ability to remotely access the registry of other computers for management purposes.
Running WinRM
WinRM (Windows Remote Management) is a command-line tool that allows you to remotely execute commands on a Windows machine. To run WinRM, first, you need to create a Group Policy Object (GPO) in your domain. To do this, open the Control Panel and select Administrative Tools > Group Policy Management. From the menu tree, click Domains > [your domain’s name] and right-click to create a GPO in this domain, linking it there. Once the GPO is created, you need to enable WinRM by setting the policy setting. You can do this by going to Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Remote Management (WinRM) > WinRM Service. Double-click the Allow Remote Server management through WinRM policy and select Enabled. Then click Apply and OK. After that, you can start using WinRM by running the following command from an elevated command prompt: “winrm quickconfig” which will configure WinRM for remote access on your computer.
Connecting to a Windows Server Using WinRM
In order to connect to a Windows server using WinRM, you must first ensure that the WinRM service is properly set up and configured on the server. To do this, you will need to open PowerShell on the server and execute the command “Enable-PsRemoting -Force”. This will configure all of the necessary components of WinRM, including setting up an HTTP listener on port 5985 (or 5986 for HTTPS).
You should also make sure that the WinRM service is set to start automatically when Windows starts up. You can do this by opening the Services MMC (services.msc) and setting “Windows Remote Management (WS-Management)” to “Automatic”.
Once WinRM is configured on the server, you will then need to trust all of the hosts that you wish to connect from. To do this, execute the command “Set-Item WSMan:\localhost\Client\TrustedHosts *” in PowerShell on the server. This will tell it to trust any host that attempts to connect via WinRM.
Finally, you may need to open port 5985 in your firewall if it is not already open. This can be done by executing “netsh advfirewall firewall add rule name=”WinRM-HTTP” dir=in localport=5985 protocol=TCP action=allow” in a Command Prompt window with elevated privileges.
Once these steps have been completed, you should be able to connect from any host that has been trusted by executing “Enter-PSSession ” in a PowerShell window on that host.
The Advantages of Using WinRM
The main advantage of WinRM is its strong security. WinRM uses the same port for both authenticating and encrypting communication, making it a secure option for network communication. This ensures that confidential data never passes through the network in an unencrypted form, reducing the risk of data breaches. Additionally, WinRM is compatible with many different firewalls, allowing organizations to easily configure their security settings.
Another advantage of WinRM is its flexibility and scalability. It can be used to manage systems from different vendors and operating systems, including Windows and Linux-based servers. It also allows for the remote execution of multiple commands at once, making it much easier to manage large networks with minimal effort. Finally, because WinRM is based on HTTPS protocol, transfer speeds are faster compared to other protocols such as SSH or Telnet.
Comparing WinRM and SSH
No, WinRM and SSH are not the same. While both technologies provide a method of remotely connecting to a system and providing a shell, they have different implementations and capabilities.
SSH (Secure Shell) is an encrypted protocol that allows for secure communication between two computers over an insecure network. It can be used for securely transferring files and executing commands on remote systems, as well as providing secure tunneling for other applications such as FTP or telnet. SSH is commonly used on Linux-based systems and is the de facto standard for system administration on those platforms.
On the other hand, WinRM (Windows Remote Management) is a SOAP-based protocol built on web services that provide remote management capabilities similar to SSH. It was introduced in Windows Vista/Server 2008 and has been improved with each new version of Windows since then. With WinRM, you can connect to a remote system and execute commands with PowerShell remoting, manage Windows services, manage event logs, create scheduled tasks, retrieve performance information, view processes running on the remote computer, and more.
So while both technologies offer similar functionality in terms of connecting to a remote system and providing a shell, they have different implementations and capabilities that make them appropriate for different situations.
Differences Between WinRM and RDP
The difference between WinRM and RDP is significant. WinRM (Windows Remote Management) is a protocol developed by Microsoft that allows for the remote execution of management commands over a variety of networks, including the Internet. It provides a secure way to perform typical administrative tasks like creating users, managing services, and running scripts without having to physically access the server.
On the other hand, RDP (Remote Desktop Protocol) is Microsoft’s proprietary protocol used to provide remote desktop access. It enables users to connect to another computer or server over a network and view the desktop as if they were sitting right in front of it. This gives them full control over the system, allowing them to install applications, configure settings and manage resources just as if they were physically present on the machine.
WinRM provides an efficient method for remotely executing management commands while RDP provides a graphical interface for remote desktop access. Both protocols are important in modern IT infrastructures and can be used together or independently depending on an organization’s requirements.
The Relationship Between WinRM and PowerShell
No, WinRM is not a PowerShell. WinRM is a command-line tool that is built into Windows operating systems and based on .NET, while PowerShell is an automation platform and scripting language built on the .NET framework. While WinRM enables scripts and remote PowerShell commands to be invoked on Windows-based machines or a large set of remote machines without RDP or logging in to the remote machine, it does not contain all of the features of PowerShell.
Does PowerShell Require WinRM?
Yes, PowerShell requires WinRM (Windows Remote Management) in order to enable remoting. PowerShell Remoting is a feature that enables users to create and manage sessions on remote computers. WinRM is a service that allows for remote management of Windows machines and provides the underlying functionality for PowerShell Remoting. It is required on both the client machine (the machine from which the commands are being sent) and the target machine (the machine where the commands will be executed). Without WinRM, PowerShell Remoting is not possible.
Installing WinRM on Windows
Installing WinRM on Windows is a simple process that can be completed in just a few steps.
First, open the Command Prompt window by searching for “cmd” in the Start Menu and then pressing Enter. Once inside the Command Prompt window, type in “powershell” and hit Enter. This will launch the Windows PowerShell utility.
Once inside Windows PowerShell, type “Install-WindowsFeature Win-RM-Ext” and press Enter to install WinRM IIS Extension, which is necessary for running WinRM on Windows. After you have entered this command, the installation process should begin automatically.
After the installation process has been completed successfully, you can verify that WinRM has been installed correctly by typing “winrm get winrm/config/listener” into the Command Prompt window and press Enter. If this command returns information about a port on which WinRM is listening, then it has been successfully installed.
If you have any issues with installing or configuring WinRM on your system, please consult Microsoft’s documentation or contact their support team for assistance.
What Is the Port Used for WinRM?
WinRM (Windows Remote Management) is a Microsoft technology for securely executing commands on remote systems. It uses the HTTP and HTTPS protocols for communication, and by default, WinRM HTTP uses port 5985 and WinRM HTTPS uses port 5986 on Windows 7 and later versions. On earlier versions of Windows, WinRM HTTP uses port 80 and WinRM HTTPS uses port 443.
Checking if WinRM is Enabled on Windows
To know if WinRM is enabled on Windows, you can use the Test-WSMan PowerShell command. This command will allow you to check the connection and authentication information for a remote computer running Windows. To run this command, simply open a PowerShell prompt and type:
Test-WSMan
If the connection is successful, you will get an output like this:
wsmid : http://schemas.dmtf.org/wbem/wsman/identity/1/wsmanidentity.xsd
ProtocolVersion : http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd
ProductVendor : Microsoft Corporation
ProductVersion : OS: 0.0.0 SP: 0.0 Stack: 3.0
This means that WinRM is enabled and working on the remote computer specified in the command.
The Relationship Between Active Directory and WinRM
Yes, Active Directory does use WinRM. WinRM (Windows Remote Management) is a Microsoft implementation of the WS-Management protocol that enables the secure, remote management of Windows-based computers. It enables IT administrators to manage Windows machines remotely using commands, scripts, and other remote management tools. Active Directory uses WinRM to allow for remote administration of domain controllers and member servers. This is especially useful for managing large numbers of machines across multiple sites or in distributed environments. With WinRM, IT admins can securely execute commands and PowerShell scripts on Windows machines from a central location. Additionally, it allows for the centralized deployment of software and other resources to networked machines.
Is WinRM Installed by Default?
Yes, Windows Remote Management (WinRM) is installed by default on all currently-supported versions of the Windows operating system. WinRM is a service that enables remote management of Windows systems, allowing users to remotely execute commands, receive output, and establish secure connections with other computers. It also provides a secure platform for remote scripting, allowing users to automate tasks across multiple systems. WinRM is an essential component of the Windows platform and its installation is required for proper system performance and security.
Communication Through WinRM
WinRM (Windows Remote Management) is a Microsoft implementation of the WS-Management protocol which enables administrators to securely remote into computers and servers for management purposes. WinRM uses SOAP (Simple Object Access Protocol) to communicate over HTTP/HTTPS. It uses an XML message format that allows for data to be exchanged between computers, enabling remote tasks such as running scripts, transferring files, and executing commands. WinRM can also be used to manage multiple hosts on a network using a single command line interface or PowerShell script. This makes it possible to quickly and securely manage large numbers of systems in an efficient manner. With WinRM, communication is secure thanks to its built-in authentication and encryption capabilities, making it easy to securely manage applications and systems both locally and remotely.
Conclusion
In conclusion, WinRM is a powerful and secure protocol that enables interoperation between hardware and operating systems from different vendors. With its firewall-friendly port, WinRM allows for secure communication across networks without compromising security. The process of setting up WinRM requires the creation of a Group Policy Object for your domain, enabling WinRM and making sure the service is set up to start automatically. Additionally, you’ll need to trust all hosts in WinRM and open the WinRM HTTP port in the firewall. With these steps completed, you can take advantage of the many benefits that come with using WinRM.