The Tor network is a powerful tool for online privacy and anonymity, allowing users to browse the web without being tracked or monitored. But did you know that Tor also offers a service called “hidden services”?
Hidden services are websites that are hosted on the Tor network, but not indexed by search engines like Google or Bing. This means that anyone can access these websites, as long as they have the correct URL. These websites can be used to host services such as anonymous file storage, private messaging, and even darknet markets.
In this blog post, we’ll take a look at how to set up and use Tor’s hidden services. We’ll also discuss how to protect yourself when using hidden services and some of the potential risks associated with them.
First things first, in order to use hidden services you will need to download and install the Tor Browser. The Tor Browser is available for Windows, MacOS, and Linux operating systems; simply visit the official website to get started (https://www.torproject.org/download/). Once installed you should be able to launch the browser from your computer’s applications menu or desktop shortcut.
Once you have launched the Tor Browser you will then need to configure your settings in order to enable hidden services. To do this go into the “Preferences” menu located in the top right corner of your browser window and click on “Advanced Settings” at the bottom of the page. From here you will see an option labeled “Enable Hidden Services” which should be checked off by default – if it isn’t then check it now! Once this is done close out of your settings menu and you should be ready to go!
Now that your settings are configured all you need is a URL address for a hidden service website – these addresses typically end in “onion” such as “http://exampleonionaddress.onion/examplepage/” so make sure not to forget that part! You can find these addresses by searching online or asking around on forums dedicated to Tor users – just make sure that any sites you visit don’t contain any illegal content before visiting them!
Finally, it’s important to keep in mind that while using Tor’s hidden services can provide great anonymity there are still some risks associated with them such as malicious actors trying to phish for personal information or infecting your computer with malware. It’s always best practice when browsing any website (hidden service or not) is making sure that you have reliable antivirus software installed on your system and exercise caution when clicking on links from unknown sources.
We hope this guide has been useful in helping understand what Tor’s hidden services are and how they work! If you have any other questions feel free to leave us a comment below or reach out via our contact page!
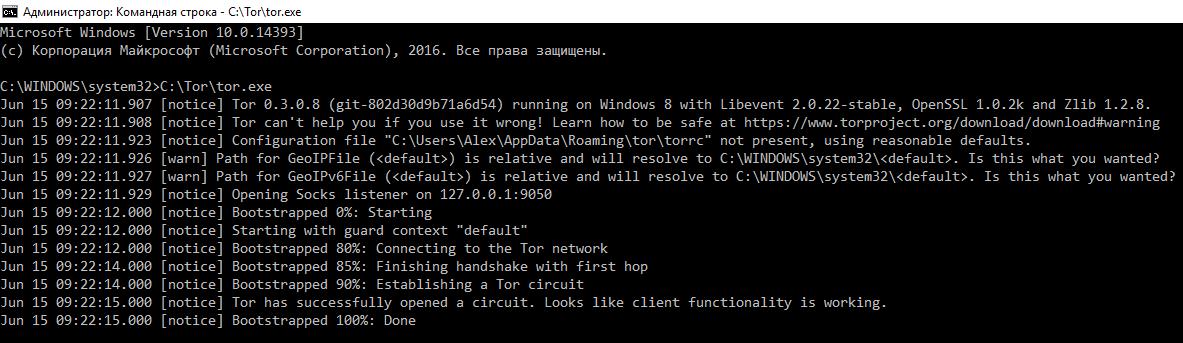
Installing the Tor Service
Installing the Tor service is a simple process that can be completed in just a few steps.
1. First, navigate to the Tor Browser download page and download the Windows .exe file (this is the recommended option).
2. Once the download is complete, you should verify the file’s signature to ensure that it has not been tampered with or corrupted during the transfer.
3. After verifying the signature, double-click on the .exe file to initiate the installation wizard process. This will guide you through a series of steps to properly install and configure Tor on your device.
4. You should now be ready to use Tor safely and securely!
Understanding How Tor Hidden Services Work
Tor hidden services work by allowing users to access and publish websites and other services without revealing their IP addresses. When a user requests a hidden service, the request is routed through a series of randomly selected Tor relays before it reaches the hidden service. The website or service is then accessed through the rendezvous point, which acts as an intermediary between the user and the hidden service provider. The rendezvous point helps keep both parties anonymous by not revealing their IP addresses to each other. This way, neither party can be identified or tracked by any third party.
The process of creating a Tor hidden service begins with an individual selecting a unique .onion address for their site or service. This address is generated using a cryptographic algorithm based on the identity key of the hidden service provider, so it can only be used for that particular website or service. Once this address is generated, it must be published in order for users to access it. After this step is complete, users can connect to the website or service using its .onion address and access it without revealing their own IP address.
The use of Tor hidden services provides a secure and anonymous way for individuals to access websites and services without having to reveal their identity or location.
Installing Tor from the Command Line
Installing Tor from the command line is a relatively straightforward process. First, you will need to open a terminal window and use the command “sudo apt install tor”. This command will install the necessary components of Tor on your system. Once the installation is complete, you will need to edit the configuration file located at /etc/tor/torrc. To do this, use the command “sudo vi /etc/tor/torrc”. Then, add any additional settings or configurations you would like to have for your Tor setup.
Next, restart the Tor service with the command “sudo /etc/init.d/tor restart”. This will enable your new configuration settings and start up all of the required services associated with Tor. To confirm that everything is working correctly, try running the command “curl ifconfig.me” which should show you your IP address (which should be different than your normal IP address). If it is different than your normal IP address then you have successfully set up and connected to the Tor network! Finally, to further verify that everything is working as intended try running “torify curl ifconfig. me 2>/dev/null” which should return an IP address different from both your normal IP address and the one returned by “curl ifconfig.me” earlier in this process.
If you find that you are still having trouble connecting to the Tor network after completing these steps, try using the command “echo -e ‘AUTHENTICATE “”\r\nsignal NEWNYM\r\nQUIT’ | nc 127.0.0.1 9051” which should force a new connection request to be sent through Tor’s control port (9051).
By following these steps and commands, you should now have a fully functioning installation of Tor on your system!
Setting Up a Torrc File
Setting up your Torrc file can be done easily from the Tor Browser Data directory. First, open Finder and select “Go to Folder…” in the “Go” menu. Then type ~/Library/Application Support/ in the window and click Go. This will open the Library folder which is hidden on newer versions of macOS. In this folder, you’ll find the TorBrowser-Data folder which contains the Torrc file. Open it with a text editor of your choice, such as TextEdit or Notepad.
Once you have opened the Torrc file, you can make any changes that you need to customize your connection settings. Be sure to save your changes and close the file before continuing. Once you have saved your changes, restart your browser for them to take effect.
Make sure that when making any changes to your Torrc file, you understand what each setting does and why you are changing it so that you don’t inadvertently break anything or leave yourself vulnerable to security risks.
Installing Tor Service on Windows
Installing Tor service on Windows is a relatively straightforward process. First, download the Windows Expert Bundle from the official website. Then, unzip the contents on your desktop. Once you have done this, run the .exe file for the Tor Browser (the version of which will depend on your computer). During installation, accept all of the default settings. When complete, click “Finish” to launch the browser and you’re all set!
If you ever need to change any of the configuration settings, you can do so by launching the Tor browser and navigating to Options > Advanced > Network Settings. There you will be able to customize your proxy settings and other privacy-related features.
With that said, please keep in mind that using Tor service comes with certain risks and should only be used if absolutely necessary. As such, always make sure to use strong passwords and enable two-factor authentication when available.
The Benefits of Using Tor Service
Tor is a free, open-source software that allows users to browse the internet anonymously. It works by routing your internet traffic through a network of volunteer relays spread across the world. This means that when you use Tor, your IP address, location, and browsing habits are hidden from anyone monitoring your connection. Tor also encrypts all of your data so that it can’t be intercepted or read by third parties. In addition to providing privacy, Tor can also be used to access websites and services that may not be available in certain countries due to censorship or other restrictions. By using Tor, you can gain access to those sites without being tracked or monitored by anyone.
Accessing Tor Configuration
To access the Tor configuration menu, open the menu under Services and select “Tor”. This will bring up the main Tor configuration page, which allows you to configure various settings related to Tor. You can also access this page by clicking on the “Configuration” button located at the top right of the page.
On this page, you will be able to configure settings such as your Onion Service Domain Name, hidden service port, and more. You can also enable or disable certain features such as anonymity (which will add an extra layer of security) or bridge relaying (which helps keep your IP address private). Once you have made any desired changes to the settings, click “Save” to apply them.
You can also access more advanced configuration options from this page by clicking on “Advanced Settings” at the bottom of the page. This will allow you to make more specific changes to how Tor operates, but should only be done by those who are familiar with this type of configuration.
Conclusion
In conclusion, Tor Hidden Service provides a secure and anonymous way to share and access services online. It allows users to create and access services without revealing the identity of the service provider or the users themselves. Tor Hidden Service uses a rendezvous point that connects users to the service provider without revealing their identities, making it one of the most secure methods of communication available. Additionally, it is highly configurable and can be customized to meet specific needs.