Have you ever wondered how websites keep your passwords safe and secure? How do they ensure that no one can access your account without permission? The answer lies in hashing and salting, two powerful security measures often used to protect passwords.
Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. The most popular use for hashing is the implementation of hash tables. In essence, the goal of hashing is to make sure that a set of data can be stored securely. Hashing algorithms take an input string and turn it into a “hash”, which looks like random characters but can only be generated with the same input string every time.
Salting adds an additional layer of protection to password security by adding a random string to each password before it’s hashed. This random string is known as a “salt” and it makes sure that two different users with the same password will have different hashes in the database. This makes it much more difficult for attackers to crack passwords because they would need to know both the salt and the hash in order to access someone’s account.
Both hashing and salting are essential tools for keeping passwords secure, but there are some important things to keep in mind when using them:
1) Make sure your salt is unique for each user – this prevents attackers from being able to use the same salt for multiple accounts.
2) Use strong hashing algorithms – weaker algorithms are easier for attackers to crack, so make sure you’re using something like SHA-256 or bcrypt.
3) Don’t store plaintext passwords – always hash them before storing them in your database!
Hashing and salting are powerful security measures that should be employed whenever possible when building applications that handle sensitive data such as passwords. By following best practices, developers can help ensure that their users’ data remains safe and secure at all times!
The Purpose of Salting Hashes
The purpose of salting hashes is to add an extra layer of security to passwords stored in databases. By adding a random string of characters, or “salt”, to the password before hashing it, the resulting hash will be unique and much harder to crack. This makes it more difficult for hackers to use pre-computed dictionaries or rainbow tables to crack passwords. In addition, if two users have the same password, they will still have different salted hashes making it more difficult for attackers to guess multiple passwords at once. Salting can also make a brute-force attack much less effective by preventing an attacker from using the same hash against multiple targets.
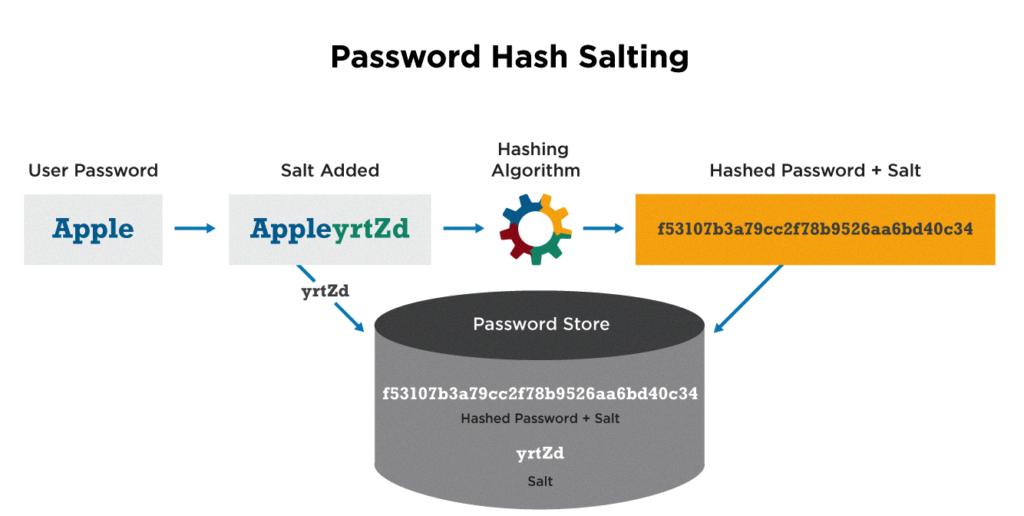
Source: cyberhoot.com
What is Hashing?
Hashing is a process of transforming an input, such as a text string or an entire file, into a fixed-length string of characters known as a hash value or hash code. Hashing is typically used to speed up data retrieval by creating an index based on the hash values of the data. This index can then be used to quickly locate and access specific pieces of data from the larger dataset. Hashing algorithms are designed to generate unique hash values for each piece of data so that if any part of the data changes (even by one bit), the hash value will be completely different. This allows for quick and accurate identification and verification of the data, ensuring accuracy and integrity.
The Benefits of Hashing and Salting for Password Storage
Hashing and salting are important security measures used to protect passwords stored in databases. Hashing is the process of encrypting a password by using a mathematical algorithm so that it can be transformed into a unique string of characters. Hashing makes it impossible for anyone to gain access to the original password. Salting adds an additional layer of security by adding a randomly-generated string of characters (known as salt) to each password before it is hashed. This makes it virtually impossible for anyone to reverse engineer the passwords from the database, even if they have gained access to the system. By combining hashing and salting, we can ensure that passwords remain secure and protected even if they’re stolen or compromised.
The Difference Between Hashing, Salting, and Encryption
The primary difference between hashing, salting, and encryption is that hashing is a one-way process that cannot be reversed, while encryption is two-way and can be decrypted. Hashing uses hash algorithms to convert passwords into ciphertext, while encryption uses cryptographic algorithms to turn plaintext into ciphertext. Salting is the process of adding random characters before or after a password prior to hashing in order to obfuscate the actual password. Encryption does not require salting as it creates an entirely new string of characters when encrypting a password.
Understanding How Hashing Works
Hashing works by taking a digital input (e.g. a password) and running it through a mathematical algorithm, which produces an output of fixed length (called a hash). The algorithm is designed so that the same input will always produce the same output, while a different input will produce a different output. This output is usually much shorter than the original input, and it is difficult to guess what the original input was just by looking at the output.
The most common type of hashing algorithm is called SHA-2 (Secure Hash Algorithm 2). This algorithm takes an input of any length and produces an output of 256 bits. It does this by breaking up the input into blocks and then running those blocks through several rounds of manipulation. These rounds are designed to make it difficult to guess what the input was just by looking at the final output. The result is a unique, fixed-length string, which can then be used as an identifier for that particular piece of data (e.g. a password).
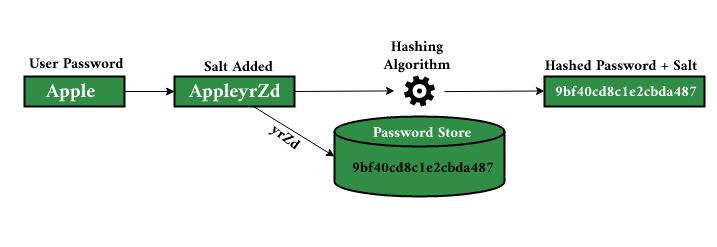
The Use of Hashing as an Example
Hashing is a technique used to quickly locate specific data within a large dataset. One example of hashing is using a hash table, which is an array-based data structure that stores items in key/value pairs. To search for an item, you use the hash function to calculate its key, then access that specific location in the array for the value associated with that key. This way, you can quickly find a value without having to search through an entire list or database. In addition to searching for values, hash tables are also useful for inserting and deleting data as they provide constant time complexity regardless of the size of the dataset.
Using Hashing in Real Life
A real-world example of hashing is seen in the use of passwords. When a user attempts to log into their account, the system will generate a hash of the password that the user has entered. This hash is compared with a stored hash of the correct password, and if they match, then the user is authorized to access their account. This process helps protect user accounts from unauthorized access by ensuring that even if hackers gain access to the stored passwords, they will still be unable to access any accounts without knowing the exact password used.
Source: supertokens.com
Can Hashed Passwords Be Reversed?
No, hashed passwords cannot be decrypted. Hashing is a one-way process, meaning that the original password cannot be recovered from the result of the hash function. When a user enters their password, it is transformed using a cryptographic hashing algorithm, such as SHA-256 or MD5. The result of this transformation is called a hash value, which is unique for each password and cannot be reversed. Even if an attacker were to gain access to the database containing all of the hashed passwords, they would not be able to decrypt them since there is no way to obtain the original plaintext passwords from their hashes.
Conclusion
In conclusion, hashing and salting are two important techniques that help protect stored passwords in databases from being stolen by hackers. Hashing is a process of transforming any given key or string of characters into a shorter, fixed-length value or key that represents the original string. Salting is the process of adding random data, known as a salt, to the hash function that hashes a password. This helps defend against dictionary attacks or rainbow table attacks and prevents the passwords from being reverse-engineered. Both hashing and salting are essential for protecting confidential data and should be used whenever possible in order to ensure maximum security.