Security Operations Centers (SOCs) are an essential part of any organization’s security strategy. With the constantly changing nature of cyber threats and their ever-increasing sophistication, SOCs provide organizations with the ability to quickly detect, investigate, and respond to security incidents. To successfully fulfill this role, organizations need to deploy appropriate software solutions that can help them stay ahead of the game.
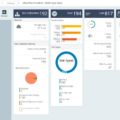
At the heart of any SOC is Security Information and Event Management (SIEM) software that acts as a central hub for all security-related activity. This software collects data from multiple sources such as network devices, applications, and endpoints, and stores it in a centralized repository. This repository is then analyzed by SOC analysts to identify suspicious activity or security incidents that may warrant further investigation.
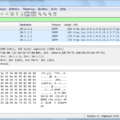
In addition to SIEM software, SOCs also use other types of software such as Network Intrusion Detection Systems (NIDS), Endpoint Protection Platforms (EPP), User Behavior Analytics (UBA), Data Loss Prevention (DLP) systems, and more. These tools play important roles in helping organizations monitor their networks for malicious activities, detect system vulnerabilities, identify unauthorized access attempts, protect sensitive data from loss or theft, and much more.
Another key component of any successful SOC is automation tools that can help streamline processes and reduce manual labor. Automation tools can be used for a variety of tasks including log correlation analysis, incident response workflows, rule-based alerting systems, real-time dashboard creation/monitoring functions, etc., allowing analysts to focus on more critical tasks such as threat hunting or data analysis.
Finally, SOC teams may also consider deploying additional third-party solutions such as managed detection and response (MDR) services or threat intelligence feeds that can provide them with better visibility into threats originating from outside their networks or offer additional context about potential malicious activities within their networks.
Overall, deploying the right mix of software solutions is essential for any organization looking to build an effective Security Operations Center capable of keeping up with today’s increasingly sophisticated cyber threats. It is important to remember that no two SOCs are alike; each organization will have its own unique set of needs when it comes to building its own SOC architecture and selecting the appropriate tools for its particular environment.
Understanding the Role of a SOC in Software
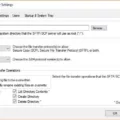
A SOC (Security Operations Center) in software is a cyber-security system that helps protect IT infrastructure and applications from malicious threats. It is designed to monitor, detect, investigate, prevent, and respond to security threats in real time. The SOC can be used to identify suspicious activity on the network and take preventative measures before any data breach occurs. It can also be used to analyze logs and identify potential vulnerabilities or malicious activities. Furthermore, a SOC can help organizations implement the necessary security policies and procedures to ensure the safety of their data.
Common Software Used by SOC Analysts
Security Information and Event Management (SIEM) systems are the primary software used by analysts in a Security Operations Center (SOC). SIEM systems allow analysts to collect, store, analyze, and report security-related events from multiple sources. They also enable real-time monitoring of data from sources such as firewalls, intrusion detection systems, antivirus software, and other network devices. SIEMs can be used for threat detection and incident response as well as for auditing and compliance reporting. Additionally, some SIEMs provide tools for the automated correlation of events across multiple sources to detect patterns of malicious behavior. This can be especially useful in identifying sophisticated attack techniques such as zero-day threats.
Comparing SOC and SIEM Solutions
A Security Operations Center (SOC) is a secure facility that provides centralized management of an organization’s security processes, resources, and tools. It includes a team of experts who are dedicated to monitoring and responding to cyber threats. A SOC is also responsible for the implementation and enforcement of security policies, procedures, standards, and guidelines.
Security Information and Event Management (SIEM) is a type of software solution that is designed to collect, analyze, and store event data from multiple sources in order to provide an organization with better visibility into its IT infrastructure. SIEM solutions are capable of collecting log files from network devices, server applications, web servers, databases, firewalls, and other sources in order to detect anomalies or suspicious activity. The collected data can then be used by security analysts for further investigation or response.
Is Splunk Used as a Security Operations Center (SOC)?
No, Splunk is not a Security Operations Center (SOC). It is a software platform that enables the collection, analysis, and visualization of data from multiple sources. The goal of Splunk is to help organizations manage, monitor and analyze their IT infrastructure in order to gain better visibility into the security posture of their organization. Splunk can be used as part of a SOC, but it cannot provide the full suite of services that an actual SOC does. A SOC provides monitoring and response capabilities for threats and incidents, including threat intelligence gathering and analysis, incident response planning and execution, forensics investigations, malware analysis, and remediation. Splunk is just one tool used within a comprehensive SOC solution to provide visibility into what’s happening on the network.
Conclusion
In conclusion, Security Operations Center (SOC) software is an essential tool for organizations looking to protect their networks and data from cyber threats. By combining the strengths of a SOC and a Security Information and Event Management (SIEM) system, organizations can benefit from the constant monitoring, detection, analysis, and investigation of cyber threats. This ensures that any suspicious activity is identified quickly and dealt with efficiently. With the help of a SOC, organizations can remain better protected from malicious actors and their attacks.