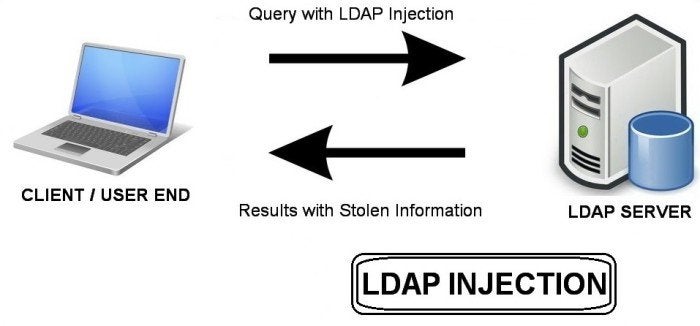
LDAP Injection is a type of cyber attack that targets web applications by exploiting security loopholes caused by unsanitized user input. LDAP, or Lightweight Directory Access Protocol, is used to search and modify data stored in a directory. This directory may contain sensitive information such as usernames and passwords, making it a prime target for malicious actors.
In an LDAP injection attack, the attacker crafts malicious queries using special characters such as brackets, asterisks, ampersands, and quotes. These attacks are difficult to detect since they appear to be valid requests from legitimate users. If successful, the attacker can gain access to the directory and potentially change its contents.
The best way to protect against LDAP injection attacks is through proper input validation and sanitization. All user inputs should be thoroughly checked before being sent to the server for processing. This means removing any dangerous characters or limiting user input to predefined values. Additionally, authentication methods such as multi-factor authentication should be employed where possible in order to reduce the risk of unauthorized access to the directory.
It’s also important for organizations to monitor their network traffic for signs of suspicious activity. If an attack is detected early enough, it can often be stopped before any damage is done. By staying vigilant and following best practices for security, organizations can help protect themselves from costly LDAP injection attacks.
Understanding LDAP Injection with an Example
LDAP injection is a type of attack that exploits weaknesses in an application’s input validation routines to inject malicious commands into a Lightweight Directory Access Protocol (LDAP) query. The attacker crafts malicious queries, which is then sent to the LDAP server for execution. As a result, the attacker may gain access to sensitive information such as usernames, passwords, and other data stored within the directory.
For example, an attacker may craft a query such as “(&(name=*)(password=*))” which will return all usernames and passwords stored in the directory. Such an attack could be used to gain access to resources or to modify data that is stored in the directory. To protect against this type of attack, applications should always perform input validation and sanitization before constructing LDAP queries. Additionally, input validation and sanitization should also be performed on any user input that is used in constructing SQL statements or other types of queries.
The Effects of a LDAP Attack
A LDAP attack is a type of injection attack that takes advantage of security vulnerabilities caused by unsanitized user input. This type of cyber-attack is executed by constructing malicious LDAP queries that contain special characters such as asterisks, brackets, ampersands, and quotes. By doing this, an attacker can gain access to the directory server and potentially modify or delete data.
LDAP injections can be used to bypass authentication processes, gain access to sensitive information, steal credentials and even add new users with higher privileges. Additionally, attackers may use LDAP injection attacks to gain access to other systems on the network or launch denial-of-service attacks. It is important for organizations to take measures to protect against LDAP injection attacks by sanitizing user input data and implementing strict security protocols for administrators.
Impact of LDAP Injection
The impact of LDAP injection can be catastrophic for an organization. It can allow malicious actors to gain access to sensitive information such as users’ emails, usernames, passwords, and other confidential data. This type of attack also enables attackers to modify or delete user accounts, which could lead to major security breaches and data loss. Furthermore, the attacker could use the stolen information to commit corporate espionage or identity theft. In addition, LDAP injection attacks may result in denial-of-service conditions that can cause a lot of disruption if left unchecked. Lastly, these attacks can provide attackers with the ability to bypass authentication protocols and gain unauthorized access to a system’s resources.
Exploring the Vulnerability of LDAP
Yes, LDAP can be exploited. LDAP injection is a type of attack that takes advantage of vulnerable web applications that construct LDAP statements based on user input. If the application does not properly sanitize the user input, malicious users can modify the LDAP statement to gain access to unauthorized resources. This kind of attack can be used to view, modify, or delete data from an LDAP server or even escalate privileges and gain administrative access. It is important for developers and administrators to ensure their applications are properly sanitizing user inputs in order to prevent these kinds of attacks.
What is LDAP and How Does it Function?
LDAP (Lightweight Directory Access Protocol) is an open, vendor-neutral protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. It provides a platform for accessing, storing, and managing user data such as email addresses, phone numbers, physical addresses, and more. LDAP is the foundation of many identity management solutions like single sign-on (SSO) and two-factor authentication (2FA).
LDAP uses a client/server model to access the directory. A client application connects to an LDAP server to query or update information. The server stores the data in a hierarchical tree structure which can be searched through by clients using well-defined attributes called queries. These queries are used to filter out irrelevant results and return only what was requested by the client application.
LDAP also supports secure connections with Transport Layer Security (TLS) encryption or Secure Sockets Layer (SSL) encryption. This keeps user information secure when sending requests over public networks or when connecting from a remote location.
The primary purpose of LDAP is to provide unified access control over distributed directories within an organization’s network infrastructure. By leveraging LDAP, organizations can easily manage users across multiple business applications in one central place. This reduces administrative overhead and increases efficiency when dealing with large amounts of users and data.
Is LDAP a Security Risk?
LDAP (Lightweight Directory Access Protocol) is a popular protocol used to manage user access to online resources. It is an important component of many authentication and authorization systems, and as such, it is essential for maintaining the security of online networks. However, LDAP can be a security risk if it is not properly secured.
The primary security risk associated with LDAP is the potential for an attacker to exploit the protocol through an LDAP injection attack. In this type of attack, an attacker crafts malicious queries that are sent to the server in an attempt to gain unauthorized access or extract sensitive information from the directory service. To prevent this type of attack from occurring, administrators should ensure that all LDAP requests are thoroughly validated before they are processed. Additionally, they should enable proper authentication and authorization protocols so that only legitimate users can access the system.
Overall, while LDAP can be a security risk if it is not properly configured, there are steps administrators can take to mitigate these risks and ensure their network remains secure.
Understanding LDAP Authentication
LDAP authentication is the process of verifying a user’s credentials against user identity information stored in an LDAP (Lightweight Directory Access Protocol) database. The authentication process begins when a client sends a request for information stored within the LDAP database, along with the user’s credentials, to an LDAP server.
The server then authenticates the credentials submitted by the user against their core user identity information that is stored in the LDAP database. This can include things such as usernames and passwords, but may also include other factors such as access rights or location-based restrictions.
Once authenticated, the server will then send back a response to the client confirming that their credentials have been successfully verified. It will also provide additional information that may be relevant to the request, such as group membership or access privileges. This way, an organization can ensure that users are only able to access resources they are authorized to view or use.
LDAP authentication is an important part of many network security systems and is used by large organizations to verify user identities and control access to sensitive information. By providing reliable authentication and authorization services, LDAP helps ensure secure communication between different systems within a network while also helping protect against potential threats from outside sources.
Causes of LDAP Errors
LDAP (Lightweight Directory Access Protocol) errors occur when a client (such as an email or web application) attempts to connect to an LDAP server. The most common causes of LDAP errors include a request sent before the server is ready, an invalid port number, or a secure socket connection that cannot be established. In order for the request to be successful, the LDAP server must allow the connection to pass authentication and authorization checks. If these checks fail, then an error will be returned. Other causes may include problems with network infrastructure, configuration issues on either the client or server-side, or incorrect authentication credentials.
LDAP Injection and Its Associated Operation
LDAP injection is a type of attack that takes advantage of improperly filtered or unvalidated user input. It allows attackers to execute arbitrary LDAP queries on an LDAP server and steal sensitive information, such as usernames and passwords, from the database. The attack works by exploiting special characters in LDAP search filters, such as the asterisk (*) symbol. An attacker can insert these special characters into user input boxes and then craft a malicious query that will return all users from the LDAP server. This type of attack can be used to gain access to confidential data or even modify existing data stored in the directory.
Do Passwords Get Stored in LDAP?
Yes, passwords are stored in LDAP. The userPassword attribute is used to store passwords and it is in plaintext form according to RFC4519. This means that a wide range of password-based authentication mechanisms, such as DIGEST-MD5, can be used to authenticate users. It is important to note that passwords are not stored in encrypted or hashed form, which may leave them vulnerable to attack if strong authentication practices are not followed.
Conclusion
In conclusion, LDAP injection attacks are a type of cyber attack that involve the manipulation of unsanitized input data to construct queries and gain unauthorized access to a directory, potentially changing the data stored within. These attacks can be very dangerous as they can lead to the exposure of sensitive information such as usernames, passwords, and emails. To protect against these attacks, developers must ensure that all user input is properly sanitized before being used in an LDAP query. Additionally, organizations should consider implementing additional security measures such as authentication and authorization protocols to mitigate against these types of attacks.