Installing Nmap on Mac OS X is a straightforward process that can be done in a few simple steps. Nmap is an open-source network security scanner and is one of the most widely used security tools in the world. It can be used to detect open ports, services, operating systems, and vulnerabilities on a system or network.
If you’re a Mac user and want to use Nmap on your system, here’s how to get started:
First, download the latest version of Nmap from the official website. After downloading the installer file, double-click it to start the installation process. The installer will then ask you to confirm that you want to make changes to your system. Once you click “yes”, the installation will begin automatically.
Once the installation is complete, launch Nmap from your Applications folder and you’re all set! If you’d like a graphical user interface (GUI) for using Nmap, Zenmap is an official GUI that comes with every installation of Nmap so it should already be availble on your Mac.
When using either Nmap or Zenmap, there are some precautions you should take in order to ensure that you are using them properly and not accidentally breaking any laws or policies. Make sure that all networks or systems scanned have given permission for such scans, and never carry out any scans without permission from the owner of the network or system – this coud land you in legal trouble if done without authorization!
That’s it – installing Nmap on your Mac OS X machine is easy and alows for quick network scans and service discovery. Enjoy!
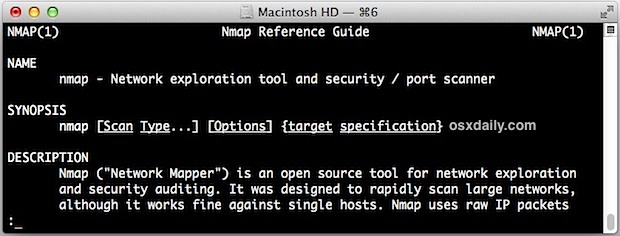
Installing Nmap on Mac
Installing Nmap and Zenmap on Mac OS X is a simple process! First, head to the Nmap download page and look for the file named nmap-. Once you’ve downloaded it, open it and you’ll be presented with the contents of the disk image. To install, simply follow the instructions in the installer. If there are any additional steps required during installation, make sure to read all onscreen instructions carefully beore continuing. Once installed, you can use Nmap to scan your network for vulnerabilities or to monitor server performance. Enjoy!
Installing Nmap
Installing Nmap on Windows is a straightforward process. First, visit the official website usng the URL https://nmap.org/download.html on any web browser and click on nmap-7.92-setup.exe. This will download the executable file to your Downloads folder. Once it has downloaded, locate the file in your Downloads folder and run it. When prompted, confirm the changes to your system and Nmap will begin installing automatically. After installation completes, you can launch Nmap directly from its desktop icon or by going to All Programs > Nmap > Nmap in the Start menu.
Where to Download Nmap
Nmap is a free and open-source network exploration and security auditing tool. It can be obtained from the official Nmap website at https://nmap.org/download.html. Here, you will find the latest version of Nmap for Windows, macOS, and Linux systems. You can download either the binary installer or the zip package for each system. Once you have downloaded your desired version, follow the instructions provided to begin uing Nmap.
Checking If Nmap Is Installed
To determine if Nmap is installed on your system, you can open a terminal window and try executing the command ‘nmap –version’. If Nmap exists and is in your PATH, you should see output similar to that in Example 2.1. If you get an error message or no output at all, this would indicate that Nmap is not installed on the system. You can then proceed to install it by following the instructions povided on the official website.
Launching Nmap
To launch Nmap, you’ll need to download and install the program from the nmap.org website. Once it’s installed, open a command prompt window and type “nmap [hostname] or nmap [ip_address]” to initiate a default scan. This will perform a check to see if the host is online using 1000 common TCP ports and Host Discovery. If you want to customize your scan, you can specify flags such as -sV (for version detection) or -A (for OS and version detection) after typing “nmap”.
Is Nmap a Free Tool?
Yes, Nmap is free and open source. It can be downloaded from the official website (https://nmap.org/download.html) for free and used for multiple purposes such as vulnerability checking, port scanning and network mapping.
Nmap is released uder a custom license which allows anyone to use, modify and distribute the software without any restrictions. Additionally, the source code is freely available online so that people can modify it to fit their specific needs.
Source: kodyaz.com
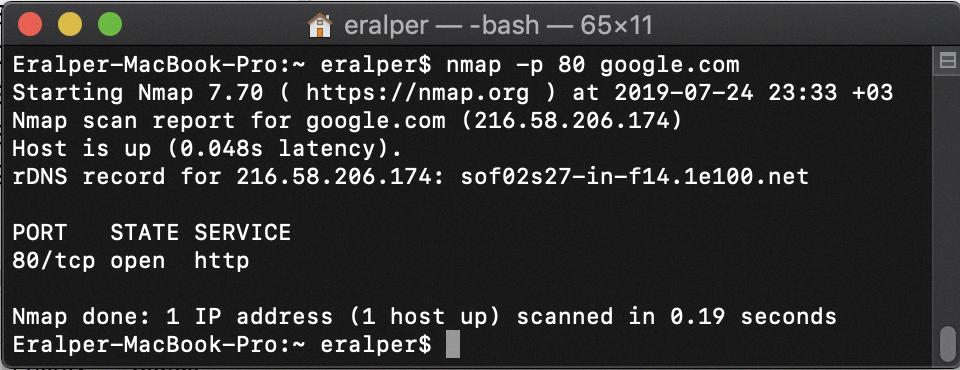
Is Nmaping Google Acceptable?
No, it is not OK to Nmap Google. Nmap is a network mapping tool and port scanner commonly used by cybersecurity professionals for network security audits. While this tool can be used to collect data about a network and its services, it should never be used to scan or probe Google’s networks or services without explicit permission. Doing so could violate terms of service, result in legal action, or cause other problems. As a general rule, it is best to avoid scanning any networks or services that you do not own or are not authorized to use.
The Consequences of Nmap Scanning Google
If you Nmap Google, you will find that most of the ports are either closed or filtered. This means that Google has implemented a strong firewall to protect their network from malicious traffic. You will also be able to identify any intrusion detection systems that have been implemented by the company. Additionally, Nmap can detect the type of system Google is running and provide a unique fingerprint to track the host. Finally, Nmap can also show what type of remote services are running on Google’s network. However, it shuld be noted that some of these features may not be available due to fallback automation.
Are Nmap and Zenmap the Same?
No, Nmap and Zenmap are not the same. Nmap is a powerful open-source tool used for port scanning and network mapping, while Zenmap is a graphical user interface (GUI) for the Nmap Security Scanner. While both tools can be used to scan networks and ports, they do so in different ways. With Nmap, users must type commands into a command line interface to perform tasks such as port scanning and network mapping. On the other hand, Zenmap provides a graphical interface that allows users to easily configure scans using drop-down menus and checkboxes. As such, Zenmap simplifies many of the tasks that would oherwise require users to manually type commands in order to complete them with Nmap. Additionally, Zenmap also includes features such as automatic host discovery and OS detection which are not available in Nmap.
Source: peakpx.com
Is There a Graphical User Interface for Nmap?
Yes, there is a GUI for Nmap: Zenmap. Zenmap is the official graphical user interface for the Nmap Security Scanner. It is a free and open-source application available for Windows, Mac OS X, Linux, and other Unix-like operating systems. Zenmap provides an easy-to-use graphical interface that makes it simple for beginners to use Nmap while at the same time giving experienced users access to all of the features and capabilities of Nmap. It also allows users to save their scan results in several different file formats and supports a wide range of command line options and custom scripts.
What Replaces Zenmap?
Nessus is a popular replacement for Zenmap, as it offers a wide range of features and capabilities for security professionals loking to scan their networks for vulnerabilities. Nessus can be used to detect any weaknesses in computers, networks, databases, applications, and other devices connected to the network. It can also detect if any malicious software is present on the system and even identify misconfigurations that could be exploited by attackers. Additionally, Nessus can be used to test for compliance with industry standards such as PCI DSS or HIPAA.
OpenVAS is another alternative to Zenmap whch offers an open source vulnerability scanner which is highly configurable and extensible. With OpenVAS you have access to an extensive library of vulnerability checks that covers a wide range of technologies and platforms. The reports generated by OpenVAS are comprehensive, allowing you to quickly identify potential vulnerabilities and take corrective action before they can be exploited by attackers.
BurpSuite is yet another powerful tool which provides users with a suite of tools including a web application scanner, proxy server, and manual testing tools. BurpSuite’s web application scanner allows users to uncover security issues in web applications such as SQL injections and cross-site scripting attacks. The proxy server can also help you intercept requests between your computer and the internet so that you can analyze traffic more closely.
Acunetix by Invicti is another great option for those looking to replace Zenmap. Acunetix provides automated scanning technology that quickly identifies potential vulnerabilities in web applications so that they can be fixed before they are exploited by attackers. Additionally, Acunetix has an intuitive user interface that makes it easy for non-technical users to use the tool effectively without needing technical knowledge about security scanning procedures.
AlienVault USM (from AT&T Cybersecurity) is a great choice if you need an all-in-one security monitoring solution in addition to vulnerability scanning capabilities like those provided by Zenmap. AlienVault USM integrates multiple security products into one unified platform so that users have access to real-time threat visibility across their entire IT environment along with vulnerability assessment features such as dynamic asset discovery and automated patching management capabilities.
Intruder is a cloud based vulnerability scanner offering both free and paid versions depending on your needs. Intruder’s cloud based platform allws you to quickly scan your entire network infrastructure from anywhere in the world with just one click of a button while producing detailed reports on any discovered vulnerabilities so that they can be addressed efficiently without delay.
Trend Micro Hybrid Cloud Security provides organizations with advanced hybrid cloud protection from threats targeting public clouds such as Amazon Web Services (AWS) or Microsoft Azure along with on-premise systems using its patented XGen™ security engine which uses machine learning techniques for detecting threats across all layers of the IT infrastructure stack from application layer down through physical hardware layer components such as switches and routers .
Qualys Cloud Platform is an end-to-end cloud security platform offering Network Discovery & Mapping along with Vulnerability Management & Patching capabilities alongside Malware Detection & Protection options all within one unified platform allowing organizations of all sizes access to comprehensive enterprise level security solutions without having large investments in time or money into setting up their own on premises solutions like those found in Zenmap .
Conclusion
In conclusion, installing Nmap and Zenmap on a Macbook is relatively straightforward. The easiest way to do it is to download the Nmap executable installer from the official website and then follow the instructions provided in the installer. Once installed, Nmap can help protect your network from invaders by scanning for potential vulnerabilities, while Zenmap provides an easy-to-use graphical interface for experienced and new users alike. Ultimately, taking the time to install Nmap and Zenmap on your Macbook will help keep your system secure.