Format string vulnerabilities are a type of security bug that can lead to serious security issues if not identified and fixed. They occur when user input is passed to the printf, scarf, or other similar functions as the format argument without proper validation. If an attacker is able to control the format argument, they could potentially leak data or cause other malicious activities.
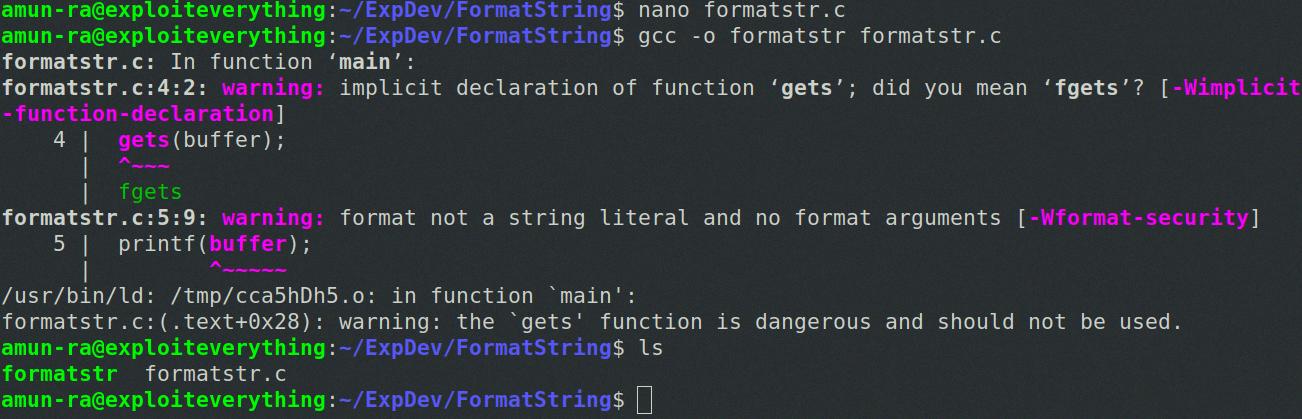
In order to understand how these vulnerabilities work, let’s look at an example. Imagine a program that takes user input and prints it out using the printf function. If the programmer mistakenly writes print (buffer) instead of print (“%s”, buffer), the user input could be interpreted as a command instead of just a string of text. This means that any malicious code supplied by an attacker can be executed by the program.
As you can see, format string vulnerabilities can cause serious security issues for your application if not identified and fixed in time. But how do you prevent them from occurring in the first place? Here are some best practices that you should follow:
• Validate all user input before passing it to functions such as printf, scanf, etc. This will ensure that no malicious code is executed by the program.
• Avoid using user input as part of the format string argument for functions like printf and scanf. Instead, use constants or pre-defined variables for this purpose.
• If possible, avoid using C-style formatted printing (print-style) altogether and use safer alternatives such as snprintf or fprintf with explicit length limits instead.
• Check your code regularly for potential format string vulnerabilities using static analysis tools such as Coverity Scan or static code analyzers like Clang Static Analyzer.
Following these best practices will help you protect your application from this type of vulnerability and ensure its security over time.
Understanding Format String Vulnerability
A format string vulnerability is a security vulnerability that occurs when the user-supplied input is passed as the format argument to printf(), scanf(), or another function in the same family. This could allow an attacker to read, write, or modify memory addresses and leak sensitive data if they control the format argument. The format argument can contain special specifiers that specify how to interpret the supplied input and which memory addresses to access. Without proper validation of user-supplied data, an attacker can craft a malicious string that causes unintended behavior.
Source: infosecwriteups.com
The Causes of Format String Vulnerability
A format string vulnerability arises when an application fails to properly handle user-supplied input in the form of a format string specifier. When user input is not adequately sanitized, an attacker can manipulate the format string to inject malicious code into the program’s memory space, which can lead to arbitrary code execution or denial of service. In some cases, an attacker can even gain access to sensitive information such as passwords and privileged user accounts. This vulnerability is most commonly seen in C/C++ programs that use the printf() function and its variants, which allow users to specify a formatting string argument that controls how the output of their data is displayed. If the formatting string argument contains malicious code, it may be executed by the vulnerable application.
Understanding Format String Bugs
Format string bugs are a type of software security vulnerability that can occur when a programmer incorrectly uses the C library function printf() when handling user-supplied data. This bug occurs when the programmer does not include a format specifier such as “%s” in the printf() statement. Without this format specifier, the program will treat the user-supplied data as if it were a part of the printf() statement and output it directly to the screen, or worse, write it to an output buffer, leading to potential security risks for the program.
Differences Between Buffer Overflow and Format String Vulnerabilities
Buffer overflow vulnerabilities occur when a program is written in such a way that it allows more user input data to be stored in a memory buffer than the capacity of the buffer can handle. This can result in overwriting adjacent memory locations, which can lead to arbitrary code execution or a denial of service attack.
Format string vulnerabilities occur when a programmer doesn’t properly validate user input before including it as part of the format string argument being passed to a function such as printf(). If an attacker passes maliciously crafted inputs, they could control how data is printed, access and alter memory contents, and even execute arbitrary code.
Types of Format String Attacks
Format string attacks are a type of vulnerability in which user-provided input is insufficiently sanitized and then used in a call to a formatted output function such as printf(). In this type of attack, an attacker can use the format string specifiers to read or write memory, control program execution flow, and even execute malicious code.
The most common types of format string attacks include:
1. Reading Memory: An attacker can use the %s (string) and %n (size) format specifiers to read data from memory addresses specified by the attacker. For example, an attacker could use %s to read sensitive information from the stack or heap.
2. Writing Memory: An attacker can also use %d (signed integer), %u (unsigned integer), and %x (hexadecimal) format specifiers to write data to memory locations specified by the attacker. This can be used to overwrite important program variables such as addresses of functions or return addresses, resulting in code execution.
3. Changing Control Flow: An attacker can also use %n (size) format specifier to write the number of characters written so far into a specific memory address that is specified by the attacker. This can be used to manipulate the program’s flow of execution by changing control flow instructions such as return addresses on the stack.
These types of attacks pose serious security risks since they allow an attacker to gain access to sensitive information, modify program variables, and execute malicious code on vulnerable systems. It is important for software developers and system administrators to be aware of these risks and take steps to mitigate them through secure coding practices and proper system hardening.
The Role of String in Cybersecurity
A SecureString is a type of string that helps provide an extra layer of security when dealing with potentially sensitive data. It allows developers to store and transmit sensitive information securely, as it is encrypted while in memory and not stored as plain text. This added level of security reduces the risk of malicious actors extracting sensitive information from applications, such as passwords and credit card numbers. Additionally, SecureString objects can be locked so that they cannot be read or modified once created, further protecting the data from unauthorized access.
Common Causes of Buffer Overflow and Format String Attacks
The common case of buffer overflow and format string attacks is the lack of proper bounds checking when manipulating user-supplied data. Buffer overflows occur when a program attempts to write more data into a fixed-length memory buffer than the buffer can hold, thereby writing into adjacent memory locations, which could potentially lead to code execution. Format string attacks occur when an attacker is able to manipulate the formatting string used by a program in order to gain control of execution flow or access sensitive information. Both types of attacks can be mitigated by performing proper input validation and bounds checking on user-supplied data.
Conclusion
In conclusion, format string vulnerability is a type of security vulnerability that occurs when user input is passed as an argument to printf , scanf , or another function in the same family. When this happens, attackers can exploit the format argument to leak data or even write malicious code into the application. Format string bugs are often caused by programming mistakes such as forgetting to add the “%s” format specifier when writing printf(buffer) instead of printf(“%s”, buffer). To protect against this type of attack, programmers should always be sure to validate user input and use functions and libraries that have built-in safeguards against these types of attacks.