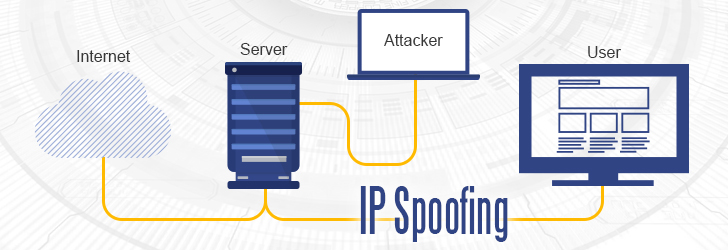
IP spoofing is a malicious practice used by hackers to gain access to sensitive data or networks. It involves disguising a computer’s true IP address with that of another system, so attackers can infiltrate networks and steal information without being detected. To protect your network from these types of attacks, it’s important to be familiar with the techniques used in IP spoofing and to understand how to prevent them.
The first step in preventing an IP spoofing attack is packet filtering. This process filters out incoming packets that contain conflicting source address information, thereby blocking any suspicious packets from questionable sources. Additionally, you should use cryptographic network protocols such as HTTP Secure (HTTPS) and Secure Shell (SSH) for added security.
You can also hide your IP address from hackers trying to disguise themselves as you. By masking your real IP address with a virtual private network (VPN), you can help protect yourself from malicious actors who want to impersonate you online.
Other tools designed specifically for anti-spoofing include ARP AntiSpoofer and shARP, which are two popular anti-spoofing tools available on the market today. These tools detect spoofed ARP requests and block them before they can cause any harm to your environment.
Finally, it’s important to stay informed about updates and security patches released by software manufacturers in order to keep your systems up-to-date with the latest security measures available. Regularly checking for updates and applying patches promptly is essential for protecting your systems against any type of cyberattack, including IP spoofing.
By understanding the techniques used in IP spoofing and taking steps to protect yourself against them, you can help keep your network secure from malicious actors looking to target you online. Packet filtering, using cryptographic protocols such as HTTPS and SSH, hiding your IP address with a VPN, installing anti-spoofing tools like ARP AntiSpoofer and shARP, as well as staying aware of security updates are all key steps towards preventing an IP spoofing attack on your system or network.
Preventing Spoofing
Spoofing can be prevented through a combination of packet filtering, cryptographic network protocols, and authentication. Packet filtering can prevent an IP spoofing attack by filtering out and blocking packets that contain conflicting source address information. Cryptographic network protocols, such as HTTP Secure (HTTPS) and Secure Shell (SSH), add another layer of protection to your environment. Additionally, authentication can be used to verify the identity of a user or device before allowing them access to the system or network. Strong authentication methods such as biometrics or two-factor authentication are recommended for added security.
Preventing Spoofing with Tools
Tools that prevent spoofing include packet filtering, ARP AntiSpoofer, shARP, and IPsec. Packet filtering is used to filter incoming packets and block any packets from questionable sources. ARP AntiSpoofer is a tool used to detect and prevent ARP spoofing attacks. shARP is an anti-spoofing tool that helps protect against IP address spoofing. Lastly, IPsec is a protocol suite used to authenticate and encrypt data transferred over a network. It can be used to protect against a variety of spoofing attacks including IP address spoofing.
Protecting Against Spoofing Attacks
Spoofing protection is a security measure designed to protect networks from unauthorized access. It works by ensuring that only devices with valid IP addresses can access the network, preventing unknown or malicious devices from gaining access. To accomplish this, spoofing protection can perform several functions, such as using firewalls to filter out illegitimate IP addresses, deploying anti-spoofing software to detect and block attempts to disguise an IP address, and tracking the source of incoming traffic. Additionally, it is important to note that while spoofing protection can be incredibly effective at keeping malicious actors out of your network, it is also possible for hackers to use IP spoofing attacks to change the IP address of their device and still gain access. To best protect against these threats, it is recommended that you hide your IP address as well as use spoofing protection.
Preventing IP Spoofing
IP spoofing is a type of cyberattack that involves creating Internet Protocol (IP) packets with an altered source IP address to impersonate another computer system. By spoofing an IP address, attackers can carry out malicious activities such as sending spam emails or launching distributed denial of service (DDoS) attacks without detection. In order to prevent IP spoofing, organizations should use security tools such as firewalls and Virtual Private Networks (VPNs). Additionally, they should employ anti-spoofing measures such as reverse path forwarding and packet filtering. These measures help to ensure that incoming traffic can be identified and blocked if necessary. Organizations should also regularly monitor their network traffic for suspicious activity.
The Causes of Spoofing
Spoofing is when someone falsifies their identity, either by pretending to be someone else or by creating a false domain, in order to gain access to confidential information or resources. This can be done through email, telephone calls, or texts. It often involves tricking the victim into believing that the message is coming from a trusted source. Spoofing can lead to serious security risks, such as data theft, malicious software attacks, and financial fraud.
Can a VPN Prevent IP Spoofing?
No, a VPN does not directly prevent IP spoofing. However, using a VPN to hide your IP address can make it much more difficult for an attacker to carry out an IP spoofing attack. By tunneling your internet traffic through a secure and encrypted connection, you will be better protected against IP spoofing and other malicious attacks. Additionally, monitoring your network with a firewall and only visiting secure sites that use HTTPS protocol can help to further protect yourself from such attacks.
Conclusion
In conclusion, IP spoofing is a serious threat to the security of any network. To help protect against this type of attack, organizations should implement tools such as packet filtering, cryptographic network protocols (e.g. HTTPS and SSH), and anti-spoofing tools (e.g. ARP AntiSpoofer and shARP). Additionally, hiding your IP address can also reduce the risk of becoming a victim of IP spoofing attacks. By taking these steps, you can better secure your network against malicious actors and help prevent unauthorized access to sensitive data.