Clickjacking is a type of cyber attack that occurs when hackers use HTML frames and invisible iframes to trick users into clicking on malicious links without their knowledge. By using this technique, attackers can gain access to user accounts, transfer funds, or steal private data.
Imagine you’re browsing the internet and come across a page with an attractive offer: “Book My Free Trip”. You click the button, only to find out later you’ve been tricked into clicking an invisible iframe that has transferred funds to the attacker. This is clickjacking in action.
Clickjacking takes advantage of HTML frames or iframes – i.e., the ability to display web pages within other web pages through frames. Essentially, an iframe is a frame within a frame and enables content from other sources to be embedded onto your web pages. Attackers can use this technique to place malicious links within the frame that appear as part of the normal page content, allowing them to trick unsuspecting users into clicking them without their knowledge or consent.
Fortunately, there are steps you can take to protect yourself from clickjacking attacks. It’s important to keep your software up-to-date so that any security patches released by developers are installed immediately. Additionally, you should be aware of suspicious websites and never click on links from unknown sources as they may contain hidden malicious code. Finally, ensure that your browser is set up with appropriate security settings in order to protect yourself from potential threats like clickjacking.
By staying vigilant and taking the necessary precautions, you can help protect yourself from falling victim to clickjacking attacks and other forms of cybercrime.

Example of Clickjacking
Clickjacking is a type of cyber attack where an attacker uses deceptive techniques to trick a user into clicking on a website element that they did not intend to click. In a typical example, the attacker will place an invisible “iframe” onto their own website and embed a link to another website within it. When the user clicks on the link, they are actually clicking on the invisible iframe, which in turn causes them to perform an action that they did not intend. For example, if the attacker embeds a “Book My Free Trip” button from a travel site onto their own page when the unsuspecting user clicks on it they are unknowingly clicking on the invisible iframe and have actually clicked on the “Confirm Transfer” button, resulting in funds being transferred to the attacker.
The Causes of Clickjacking
Clickjacking is a malicious technique of tricking a user into clicking on something different from what the user perceives they are clicking on. This can be done by using transparent or opaque layers to deceive the user about which web page element they are actually clicking. Clickjacking works by loading a page within an iframe, and then overlaying it with another page that contains an element the attackers want the victim to click. When the victim clicks on this element, they are actually performing some action on the underlying page that is loaded in the iframe.
In many cases, clickjacking can be used to steal sensitive information from users or gain access to their accounts without their knowledge. Attackers can also use clickjacking techniques to promote malicious content without users’ awareness or to manipulate users into making purchases. Additionally, clickjacking can be used as part of phishing campaigns, where attackers trick users into providing personal information such as passwords and credit card numbers.
The Difference Between Clickjacking and Phishing
Clickjacking is a type of attack that involves tricking a user into clicking on a malicious link or button, usually without them knowing it. It typically involves an attacker loading a webpage within an iframe and overlaying it with another webpage, which then prompts the user to click. The malicious webpage can be programmed to carry out certain actions, such as downloading malware or redirecting the user to a different website.
Phishing, on the other hand, is a type of social engineering attack where attackers send emails pretending to be from a legitimate organization in order to steal personal information or passwords. The email typically contains links that direct victims to fake websites where they can enter their credentials or other sensitive information. These websites often look identical to genuine ones and are designed to fool victims into thinking that they are providing their data to a legitimate company. Unlike clickjacking, phishing relies on fooling victims into trusting the attacker rather than tricking them into clicking malicious links.
What is Clickjacking in Javascript?
Clickjacking is a type of malicious attack that occurs when an attacker uses hidden frames or other techniques to manipulate users into performing actions on a website without them being aware of it. This is typically done by embedding an invisible layer over a legitimate button or link and tricking the user into clicking on it. In Javascript, clickjacking occurs when the attacker injects malicious code onto the website and tricks users into clicking on elements they didn’t intend to click. This can be done by hiding malicious code inside a frame or iframe, manipulating HTML elements with CSS, using transparent overlays, or using scripts to move elements around the page. Clickjacking can lead to serious security breaches such as stolen data, malware installation, and account hijacking. To protect against this type of attack it’s important to use secure coding practices such as sanitizing user input and using appropriate security measures like cross-site request forgery (CSRF) tokens.
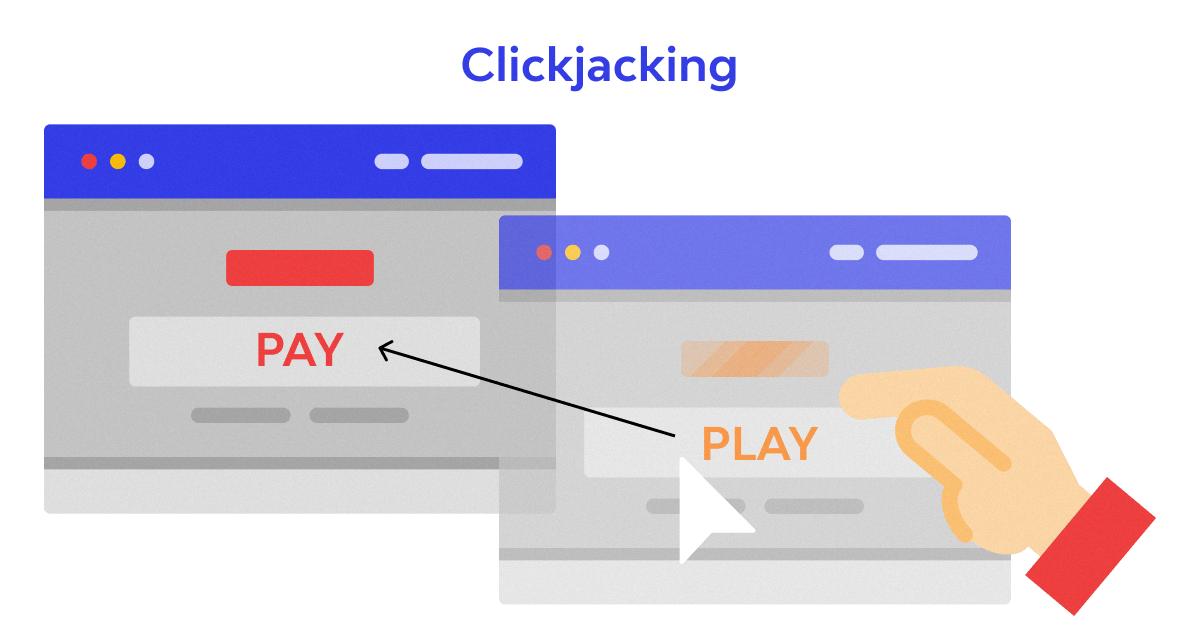
Source: wallarm.com
Preventing Clickjacking
The solution to clickjacking is to set up a defense against it. This defense can be implemented by setting certain HTTP headers that will direct the browser to not allow the target website to be embedded in an iframe. Additionally, browsers can also have an X-Frame-Options header set which will prevent a page from being loaded into an iframe unless it is from the same origin as the page. This header can also be used to restrict pages from loading into other origins. Finally, CSP (Content Security Policy) can also be used to mitigate clickjacking attacks by controlling when and where content can appear on websites.
The Severity of ClickJacking
Clickjacking can be a very serious security threat, as it allows malicious actors to access confidential information or take control of computers without the user’s knowledge. By exploiting weaknesses in web applications, attackers can create clickjack attacks that can perform a variety of malicious activities, such as stealing personal data or using your computer to send spam. In some cases, these attacks can even be used to install malware on your system. It is important to protect yourself from clickjacking by keeping your web browsers and other software up-to-date and installing security patches as soon as they become available. Additionally, you should use caution when clicking on links from unknown sources, as these could contain malicious code that could lead to a clickjacking attack.
The Risk of Clickjacking Vulnerability
Clickjacking is a type of attack that utilizes malicious code embedded in a webpage to trick users into clicking on elements they don’t intend to. This vulnerability can be used to access sensitive information, perform actions on behalf of the user, or redirect them to malicious websites. Although it is considered medium risk since it requires direct user interaction, the level of impact for a successful attack can be significant depending on the application environment and the types of data that can be exposed. A successful clickjacking attack could lead to stolen credentials, unauthorized access to accounts, data manipulation, and more. Therefore, organizations should take proactive measures to protect their systems from this type of attack.
Is Clickjacking Still a Viable Threat?
Yes, clickjacking is still possible as long as websites can be framed. Framing of websites can be prevented through the use of frame-busting or frame-breaking scripts. These scripts are typically implemented on the client side by the web browser, and they help to prevent framing attempts. However, there are methods that can be used to circumvent these protections, so it is important for website owners to remain vigilant.
Conclusion
In conclusion, clickjacking is an attack method that uses HTML frames or iframes to create a misleading user interface, making it possible for a hacker to intercept clicks and take action without the user’s knowledge. This type of attack is especially dangerous because it can lead to financial losses, identity theft, and other malicious activities. While it is similar to phishing scams in that they both involve tricking users into providing information or taking action, clickjacking does not require direct communication with the victim. Therefore, users must be aware of this attack vector and take extra precautions when clicking links online.