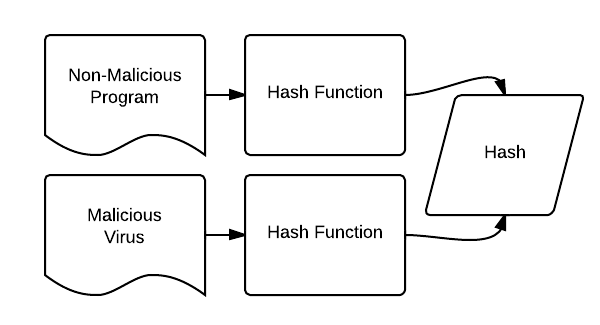
A hash collision is a phenomenon that occurs when two different pieces of data generate the same hash digest. A hash digest is an alphanumeric string that’s generated from a given piece of data, usually after being processed by a cryptographic hashing algorithm. The reason this is so important is that it helps us verify the integrity and authenticity of data since it should be impossible to find two different pieces of data with the same hash digest.
Unfortunately, it turns out that collisions can still happen in certain cases. This happens when two different pieces of data are similar enough (or have been processed in such a way) to generate the same hash digest. This poses a real security risk since an attacker could potentially create fake data that would pass the verification process due to having the same hash digest as the original data.
The best way to avoid this kind of attack is to use stronger cryptographic hashing algorithms like SHA-2 or SHA-3 which are both considered secure and resistant to collision attacks. It’s also important to remember that no cryptographic algorithm is completely secure and collisions can still occur even if you’re using one of these algorithms, so it’s important to implement other security measures such as digital signatures or certificates as well.
while it’s possible for two different pieces of data to generate the same hash digest (known as a “hash collision”), there are ways to avoid this problem by using strong cryptographic hashing algorithms and by implementing additional security measures such as digital signatures or certificates.
Example of a Hash Collision
A hash collision example is when two different pieces of data have the same hash value. This can happen when a hash function produces the same output for two different pieces of data, which is known as a “collision”. For example, assume a hash function h(text) sums all character codes in a text. It will produce the same hash value (collision) for texts holding the same letters in a different order, i.e. h(‘abc’) == h(‘cab’) == h(‘bca’). This means that if you have two strings of text with the same characters but in a different order, they will generate the same hashed output even though they are technically different pieces of data.
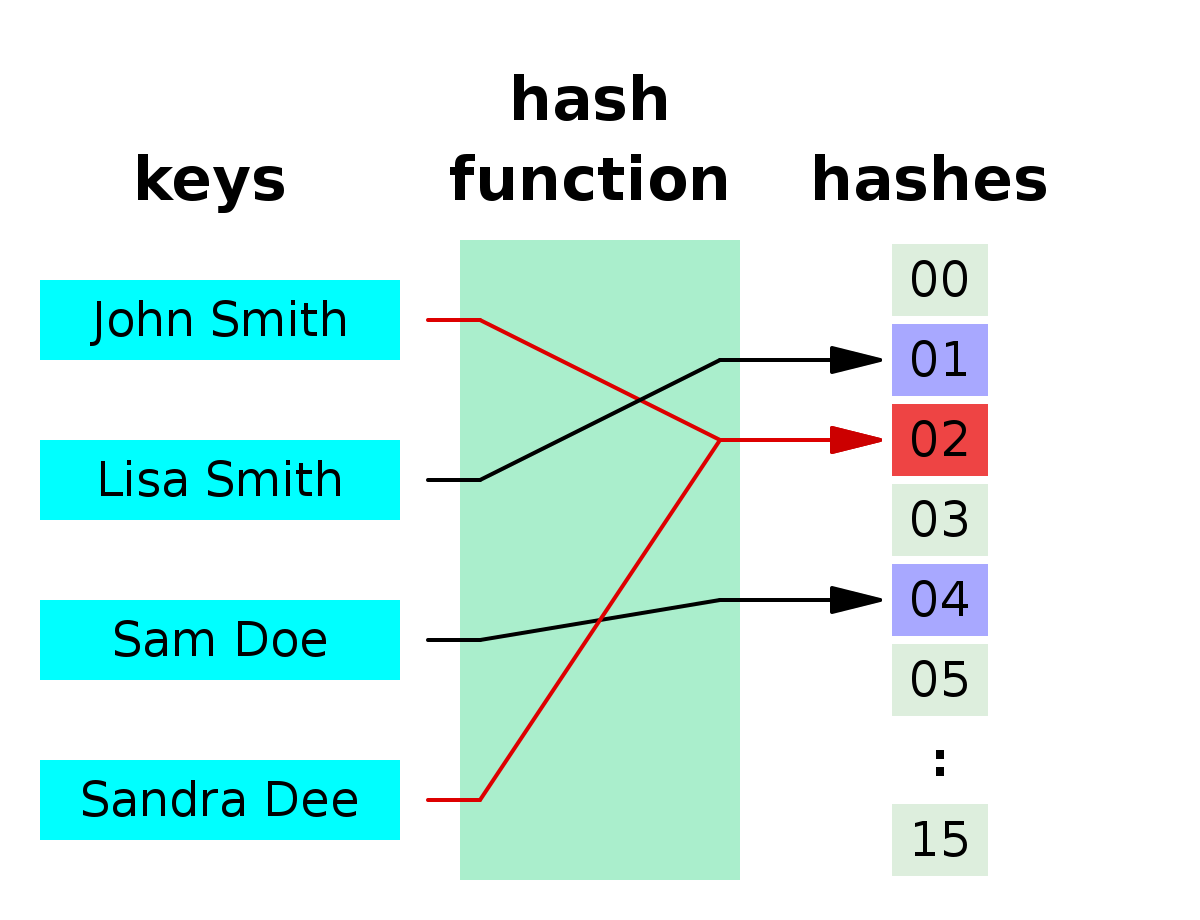
Understanding How Hash Collisions Occur
A hash collision occurs when two different values are mapped to the same slot in a hash table by a hash function. This happens because the output of a hash function is usually of fixed length, so it can only map a limited number of values. When two different inputs are mapped to the same slot, then a collision occurs.
There are two main types of collisions: chaining and open addressing. With chaining, each slot in the table contains a pointer to a linked list of records that have been hashed to that slot. With open addressing, each slot in the table contains an actual record that has been hashed to that slot. In either case, if two different values are mapped to the same slot then this leads to a collision.
To reduce the likelihood of collisions, it is important to use good hashing functions which take into account as much information as possible about the input data and generate outputs with few collisions. It may also be useful to increase the size of the hash table so that there is more room for potential mappings and thus reduce collisions.
Understanding Hash Collisions
A hash collision is when two distinct pieces of data produce the same hash value. This is an undesirable situation because it can allow attackers to create fake files that would pass a hash verification check, which could have serious security implications. Hash collisions can occur for various reasons, such as using weak hashing algorithms or having insufficient entropy in the data used to generate the hashes. To help reduce the risk of hash collisions, strong cryptographic hashing algorithms should be used and sufficient entropy should be included in the data used to generate the hashes.
Preventing Hashing Collisions
Hashing collisions can be prevented through the use of a technique called chaining. Chaining is the process of linking together multiple elements that may have been hashed to the same index in a hash table. This is done by creating a linked list at each slot in the hash table, and then adding all of the elements that were hashed to that index into the list. The benefit of chaining is that it allows for efficient retrieval of data from a hash table, as each element can be quickly accessed by traversing its linked list. Additionally, chaining also reduces the chances of collisions occurring, as it ensures that all elements stored in a single slot are linked together and can easily be found.
Likelihood of a Hash Collision
The likelihood of a hash collision depends largely on the size of the output space. If the output of the hash is an n-bit value, then the likelihood of a collision is relatively low (2-n). However, as more and more hashes are generated, it becomes more likely that there will be a collision. This is known as the birthday paradox and states that once you’ve seen roughly √(2k) items, there’s a 50% chance of a collision, where k is the number of distinct possible outputs. The larger the output space (i.e. higher n), the less likely it is that two different inputs will produce the same output.
Frequency of Hash Collisions
Hash collisions occur when two different inputs produce the same output hash. The likelihood of a collision depends on the size of the range of values that the hash function can produce. A hash function with a range of size N will typically encounter collisions after hashing √N values, or about 40% of its total range. For example, with a 64-bit hash function, there is about a 40% chance of collisions when hashing 232 or about 4 billion items.
It’s important to note that as the number of values hashed increases, so does the likelihood of collisions. This is because the chances of two different inputs producing the same output increase as more items are hashed. Therefore, it is important to use a large enough range for your hash function so that collisions are minimized.
Resolving Object Collision in Hashing
Object collision occurs when two different objects are hashed to the same index in a hash table. Collisions can be resolved by a variety of methods, such as open addressing, linear probing, and separate chaining. Open addressing uses an algorithm to determine the next available slot in the hash table if the initial slot is full. Linear probing is a technique where successive elements are placed in the next available slot until an empty spot is found. Separate chaining stores multiple items at each slot in a linked list structure. Each item stored in the same slot is referred to as a “chain”, hence the name separate chaining. Each item in the chain has its own unique key value, so no collisions occur.
Understanding Hash Collision Vulnerability
Hash collision vulnerability refers to the potential for two different inputs to generate the same hash value. This can be a problem for cryptographic systems, as it means that a malicious actor could potentially spoof messages or documents by changing the content without changing the hash, making it appear as if the message was legitimate. This vulnerability can be exploited to bypass authentication protocols, inject malicious code into programs, and more. As such, it is important to use cryptographic hashing algorithms that are resistant to collision attacks in order to protect against these types of attacks.
Resolving Hash Collision
The most common technique used to resolve hash collisions is called linear probing. This technique uses a simple approach to store and retrieves data in a hash table, by finding the next available slot in the table for each item that needs to be stored.
Linear probing works by first calculating the hash value of an item to determine its position in a hash table. If the desired slot is already occupied, it will look for the next available slot and store the item there. This process continues until an empty slot is found or until all slots have been filled. The idea behind linear probing is that if two items have different hash values, they should still be able to fit into the same table without conflict.
When searching for an item in a hash table using linear probing, it will look for it at its original position (as determined by its hash value). If not found, it will move on to each successive slot until it finds the item or reaches an empty slot.
In general, linear probing is considered to be one of the simplest methods for resolving collisions in a hash table due to its ease of implementation and use. However, due to its sequential nature, linear probing can suffer from clustering which can reduce performance over time as more items are added to the hash table.
The Difference Between Hashing and Encryption
Hashing and encryption are both ways to protect data, but they go about it in different ways. Encryption is a two-way process that uses an algorithm — like AES or RSA — to scramble plaintext into ciphertext. The ciphertext can then be decrypted back into plaintext using the same algorithm and key. Hashing, on the other hand, is a one-way process that scrambles plaintext into a unique fixed-length digest, also known as a hash value. This digest can’t be decrypted back to the original plaintext — it’s only used for verifying whether the data has been altered. Hashing also uses salts to make it harder for attackers to crack hashes through brute force attacks. In summary, while encryption scrambles data so that it can be decrypted later, hashing scrambles data so that it can’t be decrypted.
Conclusion
In conclusion, hash collisions occur when two different files generate the same hash digest. This can have serious implications for security as it allows an attacker to create a fake file that would pass hash verification. While collisions are rare, they can still pose a serious risk as it shows someone has found a mathematical technique that can reverse engineer a hash or generate data with a specific hash. It is therefore important to use secure hashing algorithms and other techniques to protect against hash collisions.