Welcome to the world of ping sweeps! Ping sweeps are an invaluable tool for network administrators and security professionals. In this blog, we will discuss what a ping sweep is, how it works, and why you should use it.
A ping sweep is a network scanning technique used to identify which IP addresses map to live hosts on a network. It does this by sending ICMP Echo Request packets to multiple hosts at once. If any of the target hosts reply, the reply reveals their IP address to the attacker. This allows them to quickly identify active hosts on the network, as well as identify any potential threats that may exist.
A ping sweep can be used for many different purposes. One of the most common uses is to inventory all of the devices connected to a particular network. By using a ping sweep, you can identify all of the active devices on a network in just seconds, allowing you to quickly determine if there are any unknown or unexpected devices connected. This can be especially helpful if you’re responsible for ensuring that only authorized personnel have access to certain networks or if you need to know exactly what types of devices are connected at any given time.
Ping sweeps can also be used for security purposes, such as identifying potential threats or vulnerabilities on a network. By sending out ICMP Echo Requests, an attacker can try and gain access to vulnerable systems or services that may exist on your network. By using a ping sweep, you can detect anomalous behavior and take appropriate steps before more serious damage is done.
Finally, ping sweeps can also be used as part of an overall performance monitoring strategy. By pinging multiple hosts at once, you can get an idea of how much traffic is flowing through each host and identify areas where performance could be improved upon. This helps ensure that your applications and services are running optimally without unnecessary delays due to heavy traffic loads or other issues.
As you can see, ping sweeps provide valuable insight into both security threats and performance issues on your network. Whether you’re responsible for tracking down malicious actors or simply want to make sure your applications are running smoothly – knowing how to use a ping sweep is an essential skill for any IT professional!
What is a Ping Sweep?
A ping sweep is a network scanning technique used to identify active hosts on a network. It works by sending out ICMP ECHO requests to multiple hosts simultaneously and listening for replies. If a host responds, it indicates that the host is alive and available on the network. This is useful for discovering new devices or checking which devices are still present on the network. Additionally, this process can also be used to map out which IP addresses are associated with each host.
Source: youtube.com
Example of a Ping Sweep
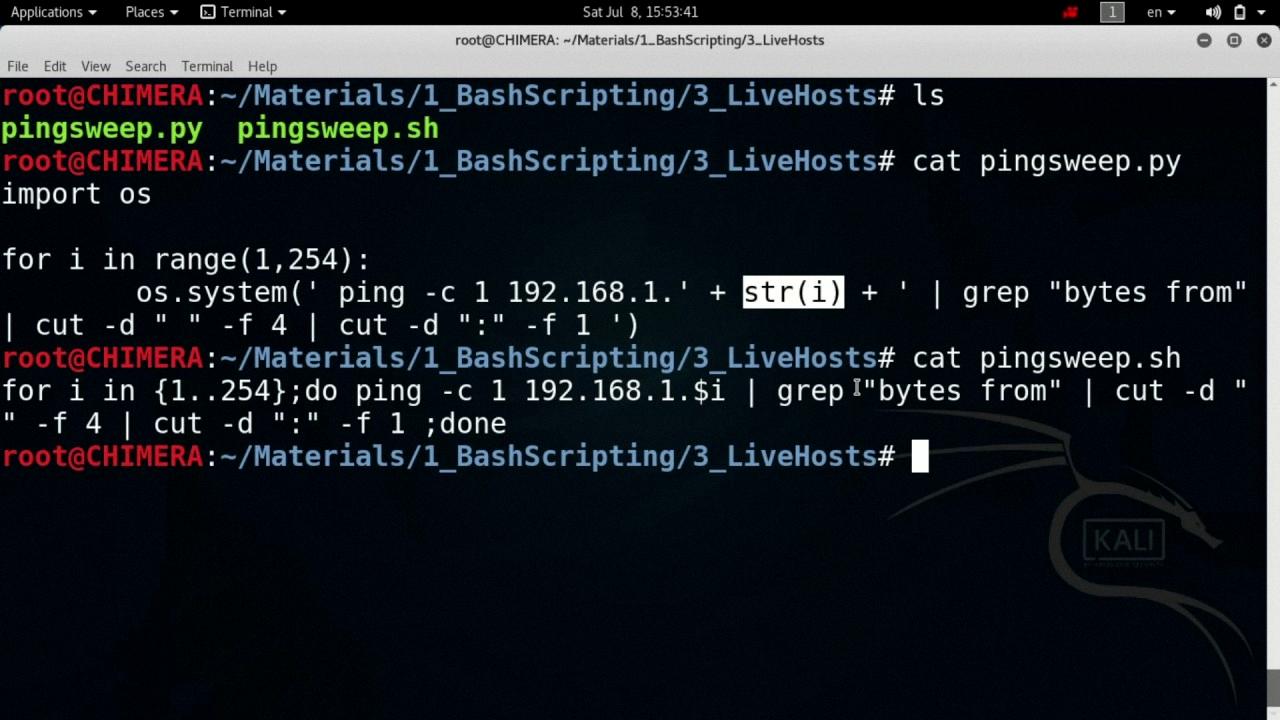
A ping sweep example is when you use a tool, such as a command line utility ping, to send ICMP Echo Request packets to multiple hosts in a network. This can be used to quickly identify all the active hosts within a given network range. For example, if you wanted to scan the entire 192.10.0.0/24 network, you could use a ping sweep to identify all active hosts within that network range.
Understanding Ping Sweep with Nmap
A ping sweep in nmap is a network reconnaissance technique used to identify active hosts on a given network. It works by sending ICMP Echo Request packets, commonly known as “pings”, to each IP address in the specified range. If an active host responds to the request, it indicates that the host is alive and reachable on the network. Nmap can be used to perform a ping sweep of an entire subnet in order to quickly identify live hosts before performing more detailed scans.
Using Ping Sweeps for Attack Purposes
An attacker can use ping sweeps to identify active hosts on a network. By sending ICMP echo requests (pings) to multiple destination addresses, the attacker can determine which IP addresses are associated with active Internet Protocol (IP) endpoints. If a target host responds to the ping, its IP address is revealed to the attacker. Such an attack can be used to gather information about a network before launching more sophisticated attacks. Additionally, attackers may use ping sweeps in conjunction with port scans or other techniques in order to map out an entire network for further exploitation.
How Long Does a Ping Sweep Take?
A ping sweep typically takes a minute or two to complete, depending on the size of the range of IPs being scanned. In the case of a small range of IPs, it can be completed in a matter of seconds. During a ping sweep, each IP address in the range is sent an ICMP request, and any IP address that responds is considered ‘alive’. This process is repeated until all IP addresses in the range have been pinged.
The Benefits of Using Nmap for Hackers
Hackers use Nmap to gain access to otherwise restricted ports on a system. By running Nmap scans, they can identify services and vulnerabilities that could potentially be exploited. Knowing where an open port is located, the hacker can then use various techniques to gain access to the system. They may also be able to monitor network traffic, launch denial-of-service attacks, or even steal confidential data. Nmap is a powerful tool for hackers because it allows them to quickly and easily find potential points of entry into a system.
Conclusion
To conclude, a Ping Sweep is an effective network scanning technique that can be used to identify which IP addresses map to live hosts. It is a useful tool for attackers to locate target hosts, and for security professionals to monitor the network for malicious activity. By sending ICMP echo requests (pings) to multiple destinations, a Ping Sweep can help determine which IP addresses are live and active. It should be noted, however, that while the Ping Sweep is an effective tool, it can be blocked or filtered by firewalls or other security measures. Ultimately, a Ping Sweep is an important network scanning technique that should be part of any comprehensive security strategy.