Network traffic analysis (NTA) is an important tool for monitoring and analyzing network activity to identify anomalies and security issues. In this blog post, we’ll introduce the main concepts of NTA, discuss its use cases, and explain how to analyze network traffic step-by-step.
NTA is a method of monitoring network availability and activity to identify anomalies, including security and operational issues. It involves collecting a real-time and historical record of what’s happening on your network, detecting malware such as ransomware activity, and more. NTA helps you understand how users interact with your network so you can identify potential problems before they become bigger issues.
NTA can be used in a variety of scenarios. For example, it can help detect malicious activities such as data exfiltration or DoS attacks. It can also be used to optimize performance by identifying areas where bandwidth utilization is inefficient or excessive. Additionally, NTA can provide insight into user behavior by revealing which applications are being used the most on a given network. This information can be used to improve the user experience or uncover malicious activities that aren’t immediately visible in other logs.
How to Analyze Network Traffic Step-by-Step
If you’re interested in using NTA to monitor your network activity, here are the steps you should take:
• Identify Your Data Sources – First, you need to determine which sources will provide the most useful data for your analysis. This could include firewalls, routers, switches, servers, endpoints, etc., depending on what type of data you need to collect.
• Determine the Best Way to Collect from Data Sources – Next, decide on the best way to collect data from each source (e.g., SNMP traps or Syslog). This will depend largely on what type of data you need and how much storage capacity is available for storing it all.
• Determine Any Collection Restrictions – Some data sources may have restrictions on how often they can be accessed or collected from; if this is the case with any of your sources then make sure you’re aware of them before beginning your analysis process.
• Start a Small and Diverse Data Collection – Start out by collecting a small subset of data from different sources so that you can test out your systems before diving into larger collections later on down the road.
• Determine Your Data Collection Destination – Finally, determine where all collected data will be stored (e.g., cloud storage or an internal server). Make sure that it has adequate space for storing all of your collected records over time as well as any additional resources needed for further analysis later on down the road such as analytics tools or visualization software like Tableau or Power BI.
Once all these steps have been completed successfully then you’re ready to start analyzing your network traffic! SolarWinds NetFlow Traffic Analyzer is one popular tool designed specifically for this purpose; however there are many others available depending on your needs and preferences (see our list here). Additionally, there are three broad types of network traffic that operators often distinguish between Sensitive (traffic containing confidential information), Best-Effort (traffic that does not require guarantees about delivery), and Undesired (traffic deemed harmful or unnecessary). Depending on which type(s) of traffic you’re looking at there may be additional considerations when performing NTA; however, these should become more apparent as you continue analyzing your networks over time!
Understanding Network Traffic Analysis
Network Traffic Analysis (NTA) is a process of monitoring and analyzing network traffic to identify security threats, operational issues, or anomalies. It involves gathering information from the network packets, including source and destination addresses, packet size, and type, as well as analyzing this data for patterns that can reveal malicious activity or other potential issues. NTA can also be used to provide an understanding of how the network is being used in order to optimize its performance. By collecting real-time and historical data on network activity, NTA can help ensure that your network remains secure and efficient.
Analyzing Network Traffic Data
Analyzing network traffic data is an important task for organizations to monitor and protect their networks. To analyze network traffic data effectively, organizations should follow a step-by-step process.
Step 1: Identify the Data Sources – Organizations should identify all the sources that are potentially providing network traffic data. This could include internal sources such as web servers, databases, and applications as well as external sources such as cloud services, third-party APIs, and internet traffic.
Step 2: Determine the Best Way to Collect from Data Sources – Organizations can use different methods to collect network traffic data such as packet sniffers, protocol analyzers, hardware probes, and port mirroring. The best collection method will depend on the type of data being collected and the available resources.
Step 3: Determine Any Collection Restrictions – Organizations need to be aware of any legal or regulatory restrictions that may apply when collecting network traffic data. Depending on the location or region of operation, there may be different laws or rules governing what type of data can be collected and how it can be used or stored.
Step 4: Start a Small and Diverse Data Collection – Organizations should start by collecting small amounts of diverse network traffic data in order to get an understanding of what types of connections are present in their network environment. This will help them determine which types of connections require more detailed monitoring in the future.
Step 5: Determine the Data Collection Destination – Organizations need to decide where they want to store their collected network traffic data. This could include cloud storage solutions such as Amazon S3 or even local storage solutions such as hard drives or servers. It’s important for organizations to ensure that their storage solution is secure so that only authorized personnel to have access to the collected network traffic data.
Step 6: Analyze Network Traffic Data – Once the organization has collected enough network traffic data, it can begin analyzing it using tools such as packet analyzers, flow analyzers, and security analysis tools. These tools can help identify trends in the collected data that could indicate malicious activity or potential security threats within the organization’s networks.
Following these steps will help organizations properly analyze their network traffic data in order to identify potential threats and keep their networks secure.
Analyzing Network Traffic with Tools
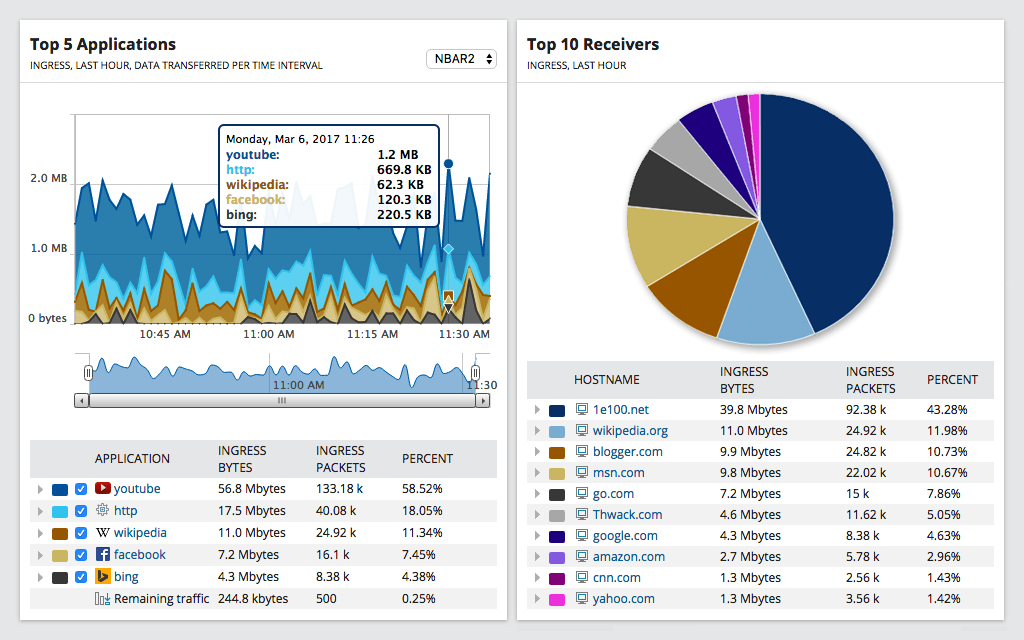
NetFlow Traffic Analyzer is a powerful tool used to analyze network traffic. It provides a comprehensive view of network traffic, allowing users to identify performance issues related to bandwidth usage, troubleshoot applications and services, and develop strategies for optimizing network performance. NetFlow Traffic Analyzer also offers advanced features such as deep packet inspection, advanced analytics, and reporting capabilities, enabling users to gain an in-depth understanding of their network’s behavior. Additionally, it is highly scalable and can be easily integrated with existing infrastructure for maximum efficiency.
Traffic Analysis Methods
The two main traffic analysis methods are passive and active. Passive traffic analysis involves analyzing the characteristics of the traffic on one side of a network to identify patterns that may indicate malicious activity. Examples of characteristics that can be examined include packet size, packet timing, and packet delivery rate. Active traffic analysis involves actively attempting to penetrate a network by sending specially crafted packets in order to detect a response from the target system or application. This type of analysis can be used to determine if a system is vulnerable and what security measures might be in place.
Most Commonly Used Network Analysis
The most commonly used network analysis tool is SolarWinds Network Performance Monitor (NPM). This tool provides comprehensive monitoring and analysis of on-premises, cloud, and hybrid networks, allowing IT professionals to quickly detect and diagnose performance issues. NPM allows users to monitor the performance of their entire infrastructure with a single dashboard. It also offers real-time visibility into the health and performance of applications running on different nodes in the network. Additionally, NPM can be used to detect problems before they become serious issues that disrupt service or cause data loss. With its intuitive user interface, comprehensive reporting capabilities, and powerful diagnostic tools, SolarWinds Network Performance Monitor is an essential tool for any network administrator.
Monitoring Network Traffic
Network managers use two main methods to monitor traffic: packet sniffing and NetFlow monitoring. Packet sniffing is a technique that captures, analyzes, and monitors data packets that flow across a network. This allows the network manager to see what type of traffic is occurring, how it is flowing, and who is sending and receiving it. NetFlow monitoring, on the other hand, collects statistical information about data flows in a network for analysis. It looks at the source IP address, destination IP address, port numbers, and protocol types to provide information about bandwidth usage, application performance, and user activity. Both techniques are invaluable tools in helping network managers identify security threats and optimize network performance.
Conclusion
In conclusion, Network Traffic Analysis (NTA) is a powerful tool that can be used to monitor network availability and activity for anomalies and issues. NTA can be used to detect malware, collect data in real-time and historically, and analyze bandwidth usage. SolarWinds NetFlow Traffic Analyzer is an example of a sophisticated NTA tool that provides users with the ability to take control of their network performance. By distinguishing three types of traffic – Sensitive, Best-Effort, and Undesired – NTA can help ensure that networks remain secure and optimized for their intended purposes.