Containers are becoming increasingly popular as a way to package and deploy applications. However, with the rise of container usage comes an increase in potential security risks. To ensure that your container-based infrastructure is secure, it’s essential to deploy the right security tools and guidelines. In this blog post, we’ll delve into some of the best container security tools available and provide a few tips on how to safeguard your containers.
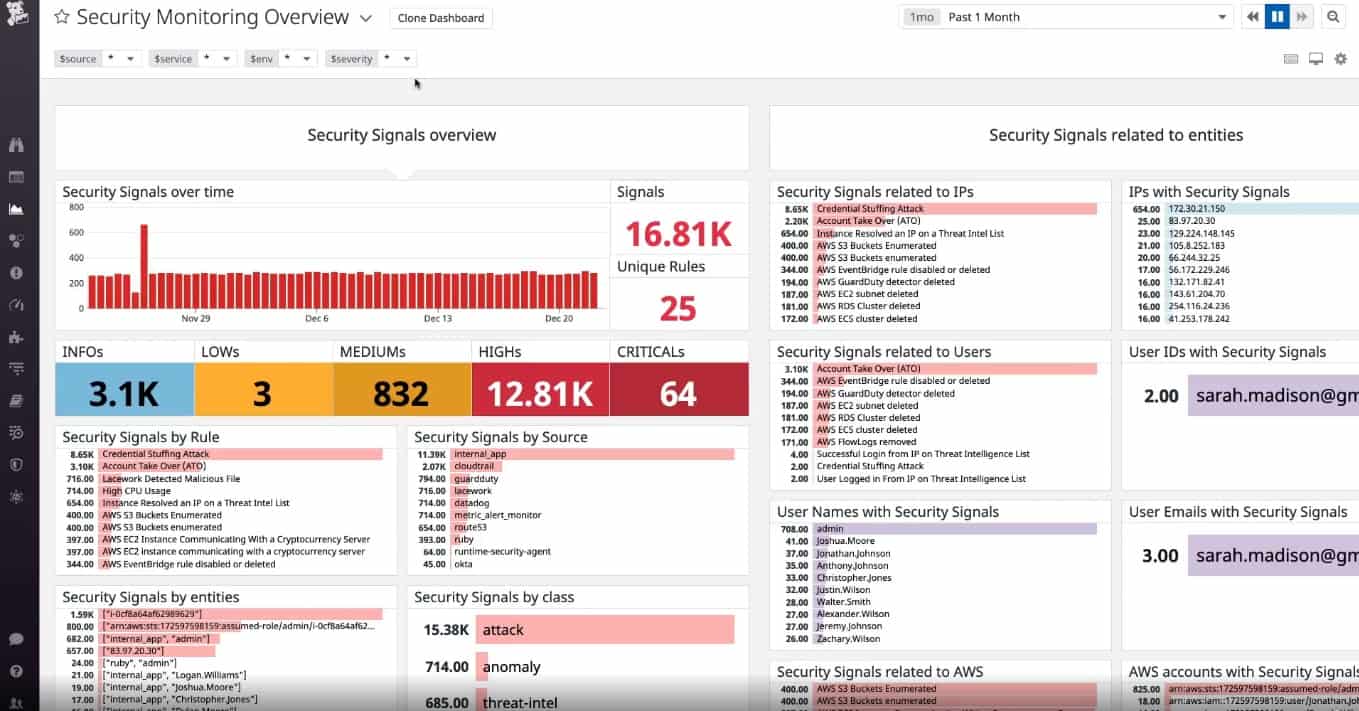
When it comes to container security, there are a number of tools available to help you protect your containers from malicious actors. One of the most popular container security tools is Datadog Cloud SIEM. This tool uses machine learning algorithms to detect suspicious activity in your environment and provides real-time alerts if something suspicious is detected. It also provides detailed forensics so you can quickly identify the source of any threats.
Anchore is another popular choice for container security. This tool analyzes images before they’re deployed and ensures that any images used to meet your organization’s security standards before being allowed into production environments. It also scans for issues such as known vulnerabilities and unapproved packages, helping you ensure that only approved images are used in production systems.
Sophos Cloud Native Security is another excellent choice when it comes to protecting containers from malicious actors. This tool is designed specifically for cloud-native environments and can detect a range of malicious activities including unapproved images, misconfigured settings, malware, and more. It also provides deep visibility into all activities within your container environment so you can quickly identify potential threats and take action accordingly.
Bitdefender GravityZone is yet another great option when it comes to securing containers in cloud environments. This tool provides comprehensive protection against malware, unauthorized access attempts, and other malicious activities with its advanced threat detection capabilities. It also allows you to monitor all activities within your environment so you can quickly detect any suspicious behavior or attacks targeted at your system.
Sysdig Secure is yet another great option for securing containers in cloud environments. This tool offers comprehensive behavioral analytics capabilities which allow you to monitor all activities within your environment in real-time and detect any suspicious or malicious behavior quickly before it has time to cause any damage or disruption to operations. It also integrates seamlessly with existing Kubernetes clusters so you can easily deploy it without having to worry about compatibility issues or additional setup steps.
RedHat Advanced Cluster Security for Kubernetes (RACS) is an open-source cluster security framework developed by RedHat specifically for Kubernetes clusters running on Red Hat OpenShift Container Platforms (OCP) or Red Hat Enterprise Linux (RHEL). RACS helps organizations maintain secure Kubernetes deployments by providing advanced monitoring capabilities which alert administrators if anything suspicious or potentially dangerous activity takes place within their cluster environment. Additionally, RACS helps organizations ensure their deployments remain compliant with industry standards by providing automated compliance checks which ensure that all deployed applications comply with established policies and guidelines set forth by organizations’ internal teams or regulatory authorities such as HIPAA or PCI DSS.
Aqua Container Security is yet another great choice when it comes to securing containers in cloud environments. Aqua combines static code analysis with runtime protection capabilities which allow organizations to analyze code for potential vulnerabilities prior to deployment as well as monitor their deployed applications for anomalies during runtime. This allows organizations using Aqua Container Security not only to detect potential threats but also to gain valuable insight into their application’s behavior during runtime, helping them uncover underlying issues behind certain behaviors.
In addition to these tools, there are many other best practices one should follow when deploying containers. Some key best practices include: thinning out images, ensuring short-lived containers, using secure registries, deploying securely, securing runtime, securing Kubernetes clusters, monitoring activity, etc. By following these best practices along with deploying the right tools one can ensure their container infrastructure remains secure against malicious actors.
Tools Used for Container Security
Container security is a critical component of any cloud-native environment. To ensure secure and reliable deployments, organizations must use a set of tools designed to protect their containerized applications. Some popular tools for container security include Datadog Cloud SIEM, Anchor, Sophos Cloud-Native Security, Bitdefender GravityZone, Sysdig Secure, RedHat Advanced Cluster Security for Kubernetes, and Aqua Container Security.
Datadog Cloud SIEM provides comprehensive security visibility across all hosts and containers in the cloud. It can detect suspicious behavior such as anomalous access attempts and malicious code execution. Anchore enables organizations to securely deploy container images by providing policy-based automated vulnerability scanning and image analysis capabilities. Sophos Cloud Native Security specializes in protecting workloads running on Kubernetes clusters with advanced threat detection capabilities. Bitdefender GravityZone is a comprehensive security platform that provides real-time protection against known and unknown threats, including those targeting containers.
Sysdig Secure is an open-source container security platform that offers vulnerability scanning, runtime protection, and forensics capabilities for cloud-native environments. RedHat Advanced Cluster Security for Kubernetes (RACS) provides continuous monitoring of the cluster to detect suspicious activity as well as automatic mitigation of detected issues. Finally, Aqua Container Security is a platform for securing containerized environments by providing runtime visibility into application behavior and ensuring compliance with organizational policies.
Securing Containers
Securing containers is essential to ensuring the overall security of a system, and there are several best practices that can help.
First, it is important to secure the images used to create containers. These images should be scanned for vulnerabilities regularly and kept up-to-date with the latest security patches. Additionally, users should ensure that only trusted images are used by setting up whitelisting policies.
Second, it is important to secure the registries where container images are stored. Access to these repositories should be limited and all image downloads should be authenticated and encrypted.
Third, when deploying containers, users should take steps to limit their surface area attack by using thin, short-lived containers whenever possible. This will help reduce the amount of time an attacker has access to a vulnerable container instance.
Fourth, users should secure the container runtime environment by implementing the least privilege access policies and ensuring that all system components are properly configured and up-to-date with the latest security patches.
Fifth, for Kubernetes clusters, users should only grant minimum necessary privileges for every component and use role-based access controls (RBAC) when creating new resources.
Finally, users should consider using container security tools such as vulnerability scanners or firewalls to detect potentially malicious activity in real-time. Additionally, monitoring tools can be used to track container activity in order to detect any suspicious activity or unauthorized changes quickly and efficiently.
The Importance of Container Cyber Security
Container cyber security is the practice of implementing tools, processes, and policies to protect container-based systems and applications from cyber threats. This includes securing the underlying infrastructure that supports the containers, such as virtual machines, networks, storage solutions, and the Kubernetes platform. It also includes protecting the container images themselves and any related configurations or data that may be stored within them. Additionally, it involves monitoring the running containers for malicious activity or unauthorized access attempts. Examples of such security measures include vulnerability scanning of container images before they are deployed; encryption of data at rest; network segmentation; enforcement of least privilege access principles; and robust logging and monitoring capabilities. In short, container cyber security is about taking a comprehensive approach to securing your entire container stack from end to end.
Conclusion
In conclusion, container security tools are essential for protecting container infrastructure, applications, and other components in order to reduce attack surfaces. Tools such as Datadog Cloud SIEM, Anchor, Sophos Cloud-Native Security, Bitdefender GravityZone, Sysdig Secure, and RedHat Advanced Cluster Security for Kubernetes can help monitor container activity and ensure that images and registries are secure. Additionally, using thin, short-lived containers can also help reduce attack surfaces. It is important to note that Sysdig is the preferred tool over Aqua Security due to its deep visibility and rich context capabilities. With the right tools in place and best practices implemented, organizations can ensure their container environment is safe and secure.