Cloud security is an important consideration for any business that uses cloud-based services or applications. With the rise of cybercrime, businesses must be vigilant about protecting their data and systems from potential threats. Fortunately, there are many cloud security tools out there that can help you do just that.
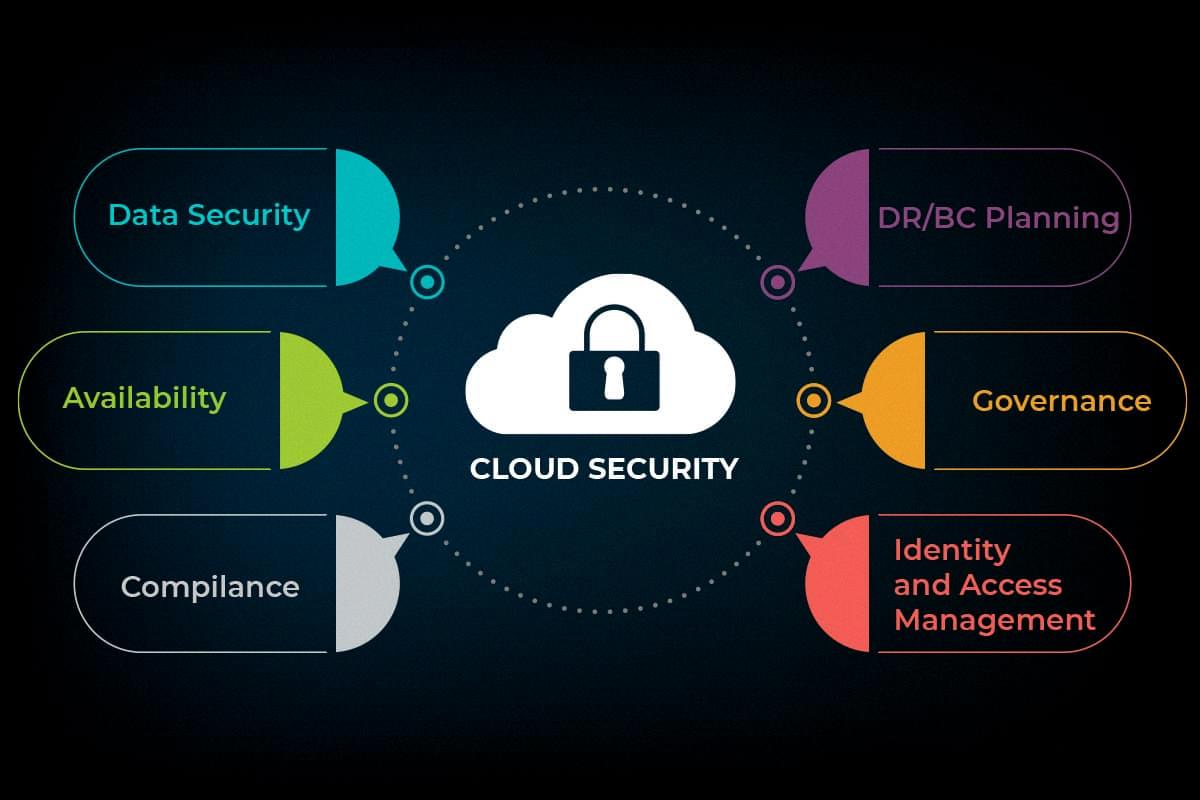
Cloud security tools can be broadly divided into three categories: identity and access management (IAM), governance (policies on threat prevention, detection, and mitigation), and data retention and business continuity planning.
Identity and access management (IAM) tools are designed to ensure that only authorized users have access to sensitive data or systems. They typically allow administrators to create user accounts with specific privileges and restrictions, as well as monitor user activity for suspicious activities. Examples of IAM tools include Azure AD B2C (Business-to-Consumer) and Auth0.
Governance tools provide a framework for organizations to set policies around threat prevention, detection, and mitigation. These tools often include automated monitoring capabilities that can alert administrators of potential threats in real-time. Examples of governance tools include CloudCheckr Security Manager and Cloud Custodian.
Data retention (DR) and business continuity (BC) planning tools help ensure that companies can keep functioning even in the event of a disaster or other disruption to their operations. These solutions typically include features such as backup plans, data replication strategies, disaster recovery plans, etc., which enable organizations to quickly resume operations after a disruption without significant loss of data or customer service levels. Examples of DR/BC planning solutions include AWS Backup & Recovery Solutions and Microsoft Azure Site Recovery Solutions.
Finally, legal compliance tools help businesses stay compliant with applicable laws related to data privacy and security such as HIPAA or GDPR regulations. These solutions typically provide features such as automated assessments for compliance with various regulations, automated reporting for audit purposes, remediation guidance when non-compliance is identified, etc. Examples of legal compliance solutions include TrustArc Privacy Compliance Suite and OneTrust Privacy Management Software Solutions.
Overall, there are numerous cloud security solutions available today that can help businesses protect their systems from potential threats while ensuring compliance with applicable laws related to data privacy & security. Whether you choose a comprehensive solution such as CloudCheckr Security Manager or opt for individual components such as AWS Backup & Recovery Solutions, these cloud security tools will help keep your business’s systems safe from potential threats while helping you meet all applicable regulatory requirements in terms of data privacy & security.

The Benefits of Cloud Security Tools
Cloud security tools are a set of software solutions that provide organizations with the ability to monitor and protect cloud-based infrastructure, networks, and applications. These solutions detect threats in real time, including malicious traffic, suspicious user activity, and malware. They can also track changes to configurations over time to ensure compliance with security policies. In addition, they offer data privacy and encryption capabilities, helping organizations meet regulatory requirements. With cloud security tools, organizations can proactively monitor their infrastructure for potential risks while also responding quickly and efficiently to any incidents that may arise.
Source: eescorporation.com
Top 5 Security Measures for Cloud Computing
1. Identity and Access Management: Identity and Access Management (IAM) is a critical security measure for cloud computing, as it helps ensure that only authorized users have access to sensitive data and systems. IAM solutions provide authentication, authorization, and auditing capabilities that help organizations manage user access to resources in the cloud.
2. Data Encryption: Encryption is an effective method of securing data stored in the cloud by scrambling the content so that it can only be accessed by users with the right encryption key. By encrypting data at rest and in transit, organizations can protect their data from unauthorized access or theft even if an attacker were to gain access to their cloud environment.
3. Firewalls: Firewalls are essential for protecting cloud environments against malicious attacks from external sources. These solutions create a virtual barrier between trusted internal networks and untrusted external networks, blocking any suspicious traffic from entering an organization’s systems.
4. Security Monitoring & Logging: Security monitoring solutions allow organizations to detect malicious activity or suspicious behavior on their cloud environment by collecting log information about system activities and sending alerts when certain events occur. Logging solutions also help organizations maintain visibility into user activities within their environment, which allows them to quickly identify any misuse of resources or attempts at unauthorized access.
5. Multi-Factor Authentication: Multi-factor authentication (MFA) adds an extra layer of protection when accessing sensitive data or applications stored in the cloud by requiring users to provide more than one form of identification such as a password, biometric scan, or authorization code sent via text message before they can gain access to the resource they are attempting to access. MFA helps reduce the risk of unauthorized access due to stolen credentials or other methods of attack.
Examples of Cloud Security
Cloud security is the process of protecting data, applications, and infrastructure that are located in the cloud. It includes a wide range of measures, such as identity and access management (IAM), data encryption, data retention and business continuity planning, governance policies on threat prevention, detection, and mitigation, and legal compliance.
Examples of security measures for the cloud include:
1. Identity and Access Management (IAM): IAM systems provide secure authentication and authorization for users to access cloud-based services. It also enables administrators to control user access rights based on their roles and responsibilities.
2. Data Encryption: Data encryption is a key component of any cloud security strategy. Encryption helps protect valuable data from unauthorized access or alteration by transforming it into an unreadable form that can only be decrypted by authorized personnel with the right credentials.
3. Data Retention & Business Continuity Planning: Cloud-based businesses must have reliable backup plans in place to ensure their long-term operations in case of a disaster or other emergency scenario. Data retention policies help establish procedures for regularly backing up data stored in the cloud so that it can quickly be recovered after an incident or outage occurs. Business continuity plans should also include steps for assessing risks associated with disaster scenarios as well as strategies for restoring operations quickly after an emergency event happens.
4. Governance Policies on Threat Prevention, Detection & Mitigation: Cloud service providers must have comprehensive security policies in place to protect their customers from malicious attacks such as phishing attempts, malware infections, and data breaches. These policies should cover everything from employee training to network monitoring systems to ensure threats are identified quickly and neutralized effectively before any serious damage occurs.
5. Legal Compliance: Compliance with applicable laws and regulations is a must for companies operating in the cloud environment due to increasingly stringent privacy requirements imposed on many industries by governments around the world. Companies must take the necessary steps to ensure their operations comply with relevant laws such as GDPR or HIPAA before storing sensitive customer information in the cloud or sharing it with third parties.
Security Testing of Cloud Using Tools
Nessus and Wireshark are two of the most popular tools that can help with the security testing of cloud systems. Nessus provides vulnerability scanning, malware detection, and configuration auditing while Wireshark is a powerful packet analyzer used to capture and analyze network traffic. Additionally, CloudTest, AppPerfect, and LoadStorm are great options for load and performance testing of cloud-based web applications. CloudTest offers a comprehensive solution for automated stress, load, scalability, and performance simulation of web applications. AppPerfect helps users assess the impact of changes in the web application environments before launching them into production. LoadStorm can be used to generate realistic user loads on web applications to identify performance bottlenecks and other issues. Ultimately, these tools can help ensure that cloud-based systems remain secure.
Categories of Cloud Security
The three categories of cloud security are Confidentiality, Integrity, and Availability (also known as the CIA triad). Confidentiality ensures that data is only accessed by authorized personnel. Integrity ensures that information is accurate and reliable; this includes preventing unauthorized modifications or deletions. Availability ensures that data is accessible when needed. This includes making sure systems are running optimally and securely, providing redundancy and backup solutions, and ensuring minimal downtime.

Source: whoa.com
Conclusion
In conclusion, cloud security tools are essential for ensuring the security of data stored in the cloud. These tools can help to protect against threats such as denial of service attacks, data loss and leakage, data privacy and confidentiality, accidental exposure of credentials, and legal compliance. Cloud security testing solutions like Nessus and Wireshark can be used to identify potential vulnerabilities in the system. Additionally, performance testing solutions like CloudTest, AppPerfect, and LoadStorm can be used to ensure that systems are running optimally. By utilizing these powerful tools, organizations can ensure that their cloud infrastructure is secure and compliant with regulations.