Cisco TACACS+ is an authentication protocol used by network administrators to manage access to network devices. It is a proprietary protocol developed by Cisco Systems and is the successor to the TACACS protocol. The main difference between TACACS and TACACS+ is that the former was mainly used for user authentication, while the latter is predominantly used for administrating network devices.
TACACS+ provides a secure remote access solution that allows an administrator to authenticate, authorize, and audit user access to network resources. It works by sending a query from an access server (e.g. switch or router) to a TACACS+ authentication server, which then authenticates the user credentials against its database of valid users.
One of the key benefits of using TACACS+ over other authentication protocols is its ability to provide granular control over user access rights on each device in the network. With this level of control, administrators can restrict access based on user roles or individual users and configure different authorization levels for each device in the network.
In addition, TACACS+ also supports encryption for secure communications between clients and servers. This helps protect data from being intercepted or modified during transmission across the network, ensuring that only authorized users have access to restricted resources.
Overall, Cisco’s TACACS+ protocol provides an effective way for administrators to manage user access across their networks while maintaining a secure environment. By leveraging its features such as granular control over user permissions and encryption capabilities, organizations can ensure that only authenticated users have access to their critical resources – reducing risk and increasing security in their networks.
What is TACACS and How Does it Work?
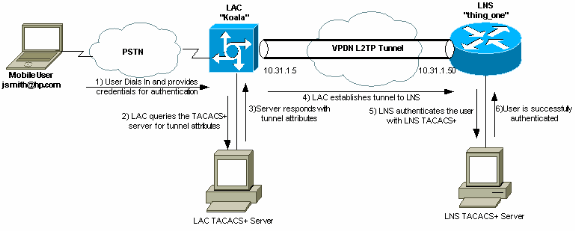
TACACS (Terminal Access Controller Access Control System) is an authentication protocol used by network administrators to manage access to network devices such as routers, switches, firewalls, and other network appliances. TACACS is a remote authentication protocol that allows a remote access server to communicate with an authentication server to validate user access to the network.
The TACACS protocol works by providing a secure communication channel between the client and server. When a user attempts to log in to the network, their credentials are sent securely over the channel to the TACACS server. The server then verifies the user’s credentials against its database of valid users. If they match, the user is granted access; if not, they are denied access. Once authenticated, the server can also provide additional information about the user such as their current privileges or capabilities on the system.
In addition to providing authentication services, TACACS can also be used for logging and auditing purposes. It can keep track of all user activities on the system so that administrators can review logs for suspicious behavior or trends in usage patterns. This helps ensure that networks remain secure and compliant with industry regulations and standards.
Source: youtube.com
What is TACACS in Cisco Switches?
TACACS (Terminal Access Controller Access-Control System) is an authentication protocol developed by Cisco for providing centralized access control for networking equipment. It is an application layer protocol designed to provide secure authentication of remote access users and the authorization of certain services on a network. TACACS+ is an extension of the original TACACS protocol which adds support for encryption, ensuring that all transmitted data is secure and not subject to tampering. With Cisco switches, TACACS+ can be used to authenticate users when they attempt to access the switch and authorize their access privileges. For example, it can be used to specify which commands or protocols are allowed or denied on the switch and provide different levels of access control based on user roles and/or individual user accounts.
Is TACACS Limited to Cisco Systems?
TACACS+ is a Cisco proprietary authentication protocol, developed by Cisco Systems. It stands for “Terminal Access Controller Access Control System Plus”, and is used to authenticate users who are attempting to access network resources. Unlike its main competitor, Remote Authentication Dial-In User Service (RADIUS), TACACS+ is a closed standard and can only be implemented on Cisco networks. Despite this limitation, the protocol is still widely used for authentication in both public and private networks due to its strong security features.
Differences Between TACACS+ and RADIUS
TACACS+ (Terminal Access Controller Access Control System Plus) and RADIUS (Remote Authentication Dial-In User Service) are two protocols used to manage access control and authentication of network users.
When it comes to user authentication, RADIUS is the protocol of choice as it allows users to gain access to the network with a username and password. Additionally, RADIUS can be used for other functions such as providing authorization, accounting, and dynamic address assignment.
TACACS+ on the other hand is mainly used for administrating network devices like routers and switches. It provides a comprehensive mechanism for performing authentication, authorization, and accounting services for network administrators. It also provides an additional layer of security by encrypting each packet of data sent between the client and server.
Overall, RADIUS is mainly used for user authentication while TACACS+ is predominantly used for administrating network devices like routers and switches.
Disadvantages of TACACS+
The main disadvantage of TACACS+ is that it was developed by Cisco and has in the past been primarily supported on Cisco equipment. As a result, it can be difficult to integrate TACACS+ with non-Cisco systems, making it less than ideal for heterogeneous environments. Additionally, TACACS+ is an older protocol and does not offer the same level of security as more modern authentication protocols such as LDAP or RADIUS. It also requires dedicated hardware for authentication, which can increase costs for larger deployments. Finally, there are limited client libraries available for use with TACACS+, which can make the development of custom applications more difficult.
The Purpose of TACACS
The purpose of TACACS (Terminal Access Controller Access Control System) is to provide a centralized authentication system for users attempting to gain access to a router, network access server, or another network device. It is mainly used in enterprise networks and provides separate authentication, authorization, and accounting services. By enabling secure access to network devices, TACACS helps ensure that only authorized users are allowed access. It also provides detailed audit logs which can be used to track user activity on the network. In addition, TACACS+ offers additional encryption capabilities which provide an extra layer of security by encrypting data transmitted between the user and the device they’re trying to access. This ensures that all data is kept secure and confidential.
Deploying TACACS
Deploying TACACS+ involves several steps:
1. Set up the TACACS+ server: This involves configuring the server address, as well as any key that may be used for authentication. This can be done by accessing Tool -> System Administration, expanding User Management, selecting Authentication Servers, and selecting TACACS+.
2. Configure the TACACS+ authentication protocol on your device: This involves setting up the proper authentication protocols to use TACACS+, such as RADIUS or LDAP.
3. Assign users to the TACACS+ server: This involves assigning users to the server, including their usernames and passwords.
4. Install a client application on each user’s device: This will allow them to access the resources they need with their assigned credentials.
5. Test your deployment: After all of these steps are complete, you should test your deployment to ensure it is working properly and that users can access the resources they need with their credentials.
Connecting to TACACS
To connect to a TACACS server, you need to first configure the TACACS server on your device. To do this, go to System & Monitor > System Settings > System > Authentication Server and select ‘Add’. Select ‘Server Type’ as TACACS+ Server and enter the relevant details. Click the ‘Test Connection’ button to check the connectivity between TACACS+ and the device, then click ‘Save’. After saving these settings, you can then use an application such as a Telnet client or SSH client to connect directly to the TACACS server.
Understanding How Cisco TACACS Works
Cisco TACACS+ is an authentication protocol that provides secure communication between network access servers and a TACACS+ daemon. This protocol allows the server to authenticate, authorize, and control user access to network resources. The protocol uses challenge-response authentication between the network access server and the TACACS+ daemon, where the daemon sends a challenge to the server and the server responds with an encrypted response. This ensures that all data exchanged between them is kept confidential. Once authentication is successful, authorization and accounting information can be sent from the TACACS+ daemon to the network access server in order to control user access to resources. The accounting information sent from the TACACS+ daemon includes session start/stop times as well as any other data relating to user activity on the network. By allowing for secure communication and comprehensive user tracking, Cisco TACACS+ provides a secure way for organizations to manage and monitor user access on their networks.
Does TACACS+ Use TCP or UDP?
TACACS+ uses the Transmission Control Protocol (TCP) to communicate between the TACACS+ client and the TACACS+ server. TCP is a connection-oriented protocol that provides end-to-end reliability guarantees that UDP does not provide. TACACS+ uses port 49 for its communication, which is the well-known port specified for it in the IANA registry.
Conclusion
In conclusion, Cisco TACACS+ is an essential tool for managing multiple network access points from a single management service. It is a proprietary protocol that provides a secure and reliable way to authenticate users and authorize their access to the network. TACACS+ is different from RADIUS as it is mainly used for administrating network devices, while RADIUS focuses on user authentication. With Cisco TACACS+, administrators can maintain control over user privileges, granting or denying access based on specific criteria. Overall, Cisco TACACS+ is a powerful tool that allows organizations to keep their networks secure and well-managed.