Active Directory Security Groups are an essential part of a secure IT environment. They provide an easy way to manage user rights and permissions across a network, giving IT administrators the ability to grant access with a single object instead of having to manage separate user permissions. This makes it much easier to keep track of who has access to what resources, and helps ensure that only authorized personnel can access sensitive information.
When creating new security groups in Active Directory, Administrators should first start by naming the group and choosing a group scope – either Universal, Global, or Domain Local. The type should also be set as Security instead of Distribution if the purpose is for managing user rights and permissions. Once the group has been created, members can be added by clicking on the Members tab within Properties, then Add.
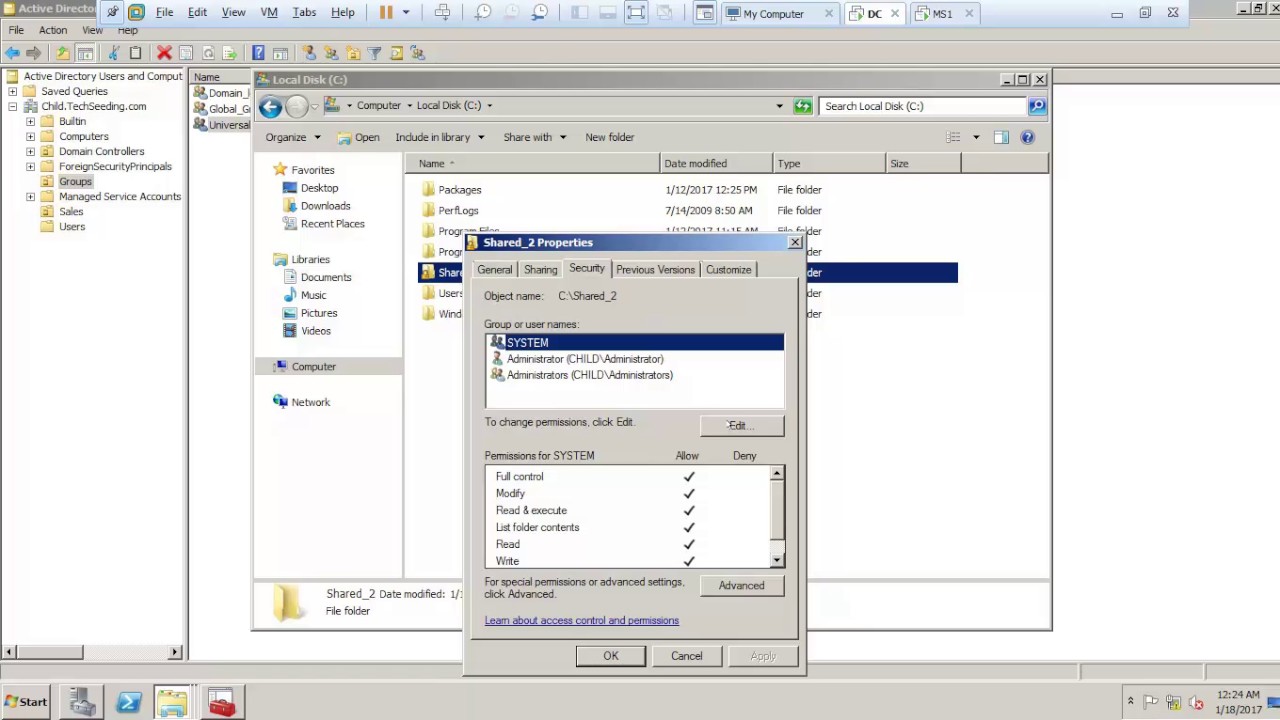
Security groups can be used to assign specific rights and privileges to resources within Active Directory such as shared folders or printers. For example, you may want certain users to have full control over a shared folder while others only have read-only access; this is where security groups come in handy. By assigning appropriate permissions to the relevant security group and then adding users to that group, IT Administrators can easily control who has access to each resource.
It’s important for Administrators to regularly review security groups and any associated permissions in order to ensure that appropriate levels of access are being maintained at all times. This is especially important when adding new members or removing existing members from security groups since any changes made could potentially affect the entire system if not done properly.
Active Directory Security Groups provide an efficient way for IT Administrators to manage user rights and permissions with minimal effort. With careful planning and regular reviews, these powerful tools can help maintain a secure environment that ensures only authorized personnel have access to sensitive information on the network.
Types of Active Directory Security Groups
Active Directory security groups are used to manage access to resources across a network. They allow an administrator to assign permissions to a large number of users at once, rather than individually. There are three types of Active Directory security groups: Universal, Global, and Domain Local.
Universal groups are used when access needs to be granted to users in multiple domains within the same forest. These groups can contain members from any domain within the forest and can be granted access permissions on any resource in any domain within the forest.
Global groups are used when access needs to be granted to users in a single domain. These groups can contain members from only one domain and cannot be granted access permissions on resources in other domains.
Domain Local groups are used when access needs to be granted to specific resources within a single domain. These groups can contain members from any domain in the forest but can only be assigned permissions on resources within the same domain as the group itself.
The Purpose of Security Groups in Active Directory
The primary purpose of a security group in Active Directory (AD) is to simplify the process of granting and managing permissions for multiple users. Instead of assigning rights to every individual user, IT administrators can assign them to a single object — the security group — and all members of that group will automatically inherit those rights. This helps to save time and effort when managing permissions for large numbers of users. Security groups are also used to ensure better control over access, as any changes made to the group’s permissions will be reflected immediately across all associated users. Furthermore, security groups provide an additional layer of security by allowing administrators to restrict access at a much finer level than would otherwise be possible with individual user accounts.
Difference Between Ad Group and Security Group
The key difference between an Active Directory (AD) Group and a Security Group is that AD Groups are used to manage user access to resources within an enterprise, while Security Groups are used to control access to specific resources. AD Groups are typically used to organize users into logical collections and provide a common set of permissions across the group, while Security Groups are used to grant or deny access on an individual resource basis.
An AD Group can contain any combination of users, computers, and other groups within an Active Directory domain, while a Security Group only contains users. This means that when applying permissions to resources, an administrator can create a single hierarchical structure in AD Groups that apply the same permissions across all members of the group.
For example, if you wanted to assign read-only access for all members of a certain department in your organization, you could create an AD Group for that department and assign it read-only permissions on the shared resource. All members of the group would then be granted read-only access with no additional effort from the administrator.
In contrast, with Security Groups, each user must be explicitly added or removed from the group in order for them to gain or lose access to a resource. This makes it more difficult for administrators to manage who has access to which resources as changes must be manually made as users join or leave the organization or change departments.
Overall, AD Groups are best suited for managing user permissions across large numbers of people and resources within an enterprise network while Security Groups provide granular control over who has access to specific resources.
Accessing Active Directory Security Groups
Accessing Active Directory security groups is simple and straightforward. To begin, open the Active Directory Users and Computers management console. From there, you can right-click on any organizational unit or container to create a new group, or select an existing group to manage its members. When creating a new group, make sure to select ‘Security’ for the Group Type and ‘Universal’ for the Group Scope.
Once the group is created, you can access its properties by double-clicking it in the left pane of the console window. In the properties window, click on the Members tab to add existing users from your directory or other domains in your forest as members of this security group. You can also use this tab to quickly view which users are already members of this security group.
Finally, when done adding users or making changes to this group’s membership list, click OK to save your changes and exit out of the Properties window.
The Three Main Components of Active Directory
The three main components of an Active Directory are domains, trees, and forests.
A domain is a collection of network objects such as users, computers, printers, and other devices that share common security policies and settings. All objects within a domain have the same set of permissions and access rights, allowing for efficient management of resources. Domains also provide authentication to ensure that only authorized users have access to sensitive data.
Trees are collections of domains that share a common name structure. Trees can span multiple domains and can be linked together by trust relationships. All objects within the tree have the same user name format and share a common schema, meaning they can be managed from one central location.
Forests are collections of trees that form an administrative boundary for all Active Directory objects. Forests allow administrators to create trust relationships between different trees so that resources can be shared across organizational boundaries. Forests also provide additional security features such as fine-grained password policies and object-level permissions.
The Four Components of Active Directory
Active Directory is an essential part of the Windows operating system, and it’s responsible for organizing, managing, and maintaining the data in a network. It consists of four main components: forests, trees, domains, and organizational units (OUs).
Forests are the highest level of organization in Active Directory and are used to control access to resources across multiple domains. Trees are collections of one or more domains that share a common namespace. Domains contain user accounts and computer objects that can be managed together as one unit. Finally, OUs are used to organize objects within a domain such as users, computers, printers, and other resources.
By using these four components, Active Directory simplifies the management of networks by providing administrators with an organized way to manage their users, computers, and other network objects.
The Need for Security Groups
Security groups are essential for ensuring the security and integrity of your networks and applications. They allow you to control the access to and from your resources, such as EC2 instances, by specifying which network traffic is allowed or denied. Security groups act as virtual firewalls that protect your resources from malicious traffic, unauthorized access, and other threats.
Security groups can help protect against malicious activity by providing an additional layer of security to control which traffic can reach your resources. By setting up rules within a security group that specifies who can access what resources, you can ensure that only authorized people or systems have access to those resources. You can also restrict the types of traffic allowed into and out of a resource to further secure it.
Additionally, security groups can help you optimize network performance by allowing you to specify which services are accessible from outside of your network. This way, traffic from unwanted sources won’t be able to reach your resources, freeing up bandwidth for more important tasks.
In summary, security groups are an essential tool for protecting your networks and applications from malicious activity and unauthorized access while also optimizing network performance.
Difference Between Security Groups and Distribution Lists in Active Directory
Security groups and distribution lists in Active Directory both serve the purpose of organizing users and resources. The main difference between them is that security groups are used to assign permissions to resources, while distribution lists are used for sending email notifications to a group of people.
Security groups provide centralized user management by allowing an administrator to assign access rights for specific network resources. This includes granting read and write permissions to files, folders, applications, and websites. The members of a security group can also be granted or denied access to use certain network services such as printing and remote desktop access.
Distribution lists are used for sending email notifications to multiple people at once. They are a convenient way of keeping track of a large number of contacts in one place, as well as streamlining email communication by eliminating the need to type in multiple addresses each time an email needs to be sent. Distribution lists can also be used with other services such as calendar sharing and task delegation.
Mail-enabled security groups combine the features of both security groups and distribution lists by allowing administrators to assign access rights while also having the ability to send emails out to the members of the group. This makes it easier for administrators to keep track of who has access to what resources, while still being able to communicate with them quickly via email notifications.
Managing Security Groups as a User
As a user, you can manage security groups in the Microsoft 365 admin center. To do this, first, go to the Groups > Groups page in the admin center. Then select Add a group, and choose Security for the group type. Finally, follow the steps to complete the creation of the group.
The security group you create will allow you to define which users have access to specific resources or services within your organization. You can also use security groups to control who can access certain areas of your organization’s data and systems. Additionally, you can use security groups to give different levels of access to users based on their roles or job functions within your organization.
Types of Groups in Active Directory
The two types of groups in Active Directory (AD) Domain Services (DS) are Distribution Groups and Security Groups.
Distribution Groups are used for sending emails or other messages to a group of users. When a message is sent to a Distribution Group, it is delivered to all members of the group. This type of group does not have any security privileges associated with it, making it ideal for communicating with large numbers of users at once.
Security Groups are used to manage access to resources such as files, folders, and printers. Members can be added and removed from Security Groups, which grants them permission to use the associated resources. These groups can also be used to create nested groups where membership in one group grants access to another group’s resources. Security Groups can also be set up with specific user rights that allow or deny certain actions on the network within AD DS.
Understanding the Difference Between Security and 365 Group
A security group is a collection of users, devices, groups, and service principals that are granted permission to access resources or services in an organization. Security groups provide an easy way to manage access to resources such as shared folders, network shares, printers, and websites. They can also be used to simplify user administration tasks such as adding users to multiple groups at once or assigning permissions for a single resource to multiple users.
Microsoft 365 Groups (formerly Office 365 Groups) are different from security groups and provide collaboration features as well as access control for shared resources. A 365 Group provides a shared workspace for team conversations, files, notes, and more. Unlike security groups, only users can be members of a Microsoft 365 Group—there are no device or service principal memberships. Microsoft 365 Groups also contain membership controls that allow the owners of the group to define who can join the group and who can view its content.
Conclusion
In conclusion, Active Directory Security Groups are a powerful and useful tool for managing user rights and permissions in an enterprise environment. By creating a single object and assigning specific rights to it, IT admins can easily manage user access to resources without having to assign individual rights to each user. Furthermore, Active Directory Security Groups provide an efficient way to manage large numbers of users by allowing for the quick addition or removal of users from the group. Ultimately, Active Directory Security Groups are an invaluable tool to help ensure security within an organization.