Welcome to the world of network packet sniffing and analysis! In this blog post, we will take a look at one of the most popular and powerful tools available for this purpose: tcpdump. Tcpdump is a command-line packet analyzer used to capture and analyze packets traveling over a network.
In order to understand what tcpdump does, it helps to first understand what a packet is. A packet is a unit of data sent from one computer to another via the Internet or other networks. Each packet contains information about its sender, destination, size, and contents. The contents may be anything from text messages to images and video streams.
Tcpdump can be used to capture the packets traveling over a network in order for us to analyze them. It works by listening on an interface and dumping any packets that pass through that interface. This makes it possible for us to gain insight into the traffic going through our nodes. We can then use this information to better understand what kind of data is being transferred over our networks as well as identify any potential security threats or malicious activities.
In addition, tcpdump can decode data payloads if encryption keys are known and can recognize data payloads coming from file transfers such as SMTP, HTTP, etc. It also offers some limited filtering capabilities so that it can focus on specific types of traffic or particular sources and destinations.
Overall, tcpdump is an incredibly useful tool when it comes to monitoring and analyzing traffic on your networks. It’s open source and easy to use yet still extremely powerful – making it ideal for both beginners and experienced network engineers alike!
Uses of Tcpdump
Tcpdump is a powerful packet analyzer used to capture and examine network traffic for troubleshooting and security purposes. It captures data packets transmitted over a network and displays vital information such as source and destination IP addresses, port numbers, packet size, protocol type, and the contents of the packet itself. Tcpdump can be used to detect malicious activity on a network, analyze network performance issues, or troubleshoot application problems. It can also be used to monitor bandwidth usage or capture data for forensic analysis.
Understanding TCPdump and Wireshark
Tcpdump is a command line-based packet-capturing tool that can be used to capture, analyze, and decode network traffic. It is capable of capturing packets from a wide range of protocols such as Ethernet, IP, TCP, UDP, and more. Tcpdump can also be used to debug network problems or monitor network activity.
Wireshark is a graphical user interface-based packet analyzing tool that allows users to capture, view and analyze data packets on a network. It provides detailed information about the packet including source and destination addresses, protocol type, and headers. Wireshark can also decode data payloads if the encryption keys are identified, and it can recognize data payloads from file transfers such as smtp, http, etc. Additionally, it comes with powerful filters that allow users to quickly filter out specific traffic patterns or events.
Understanding TCP Dump in Cyber Security
TCPdump is a powerful and widely used command-line utility for packet capture and analysis in Cyber Security. It allows administrators to capture traffic on a network interface, filter it according to various criteria and display it in a human-readable format. The captured data can then be used for further analysis or troubleshooting. TCPdump is an open-source tool, so it can be freely used, modified, and redistributed by anyone. It provides a great deal of flexibility when capturing data, as the user can specify the specific type of packets they want to capture (e.g., only ICMP packets), or limit the amount of data that is captured. Additionally, tcpdump can be used to monitor large networks with hundreds of hosts, as it permits the user to capture all traffic on a given subnet or even just traffic between two specified IP addresses. This makes it ideal for monitoring malicious activity on a network, such as port scans and denial-of-service attacks.
The Use of Tcpdump as a Network Sniffer
Yes, tcpdump is a network sniffer. It is a packet analyzer tool that is used to capture and analyze network traffic passing through an interface. It captures the packets, displays them in a readable format, and allows us to take a deeper look at the data within the packets. It can be used to troubleshoot network-related issues, analyze traffic patterns, detect malicious activity, and more. Additionally, tcpdump can be used with custom filters to capture specific types of data and exclude others from being captured.
Running a TCP Dump
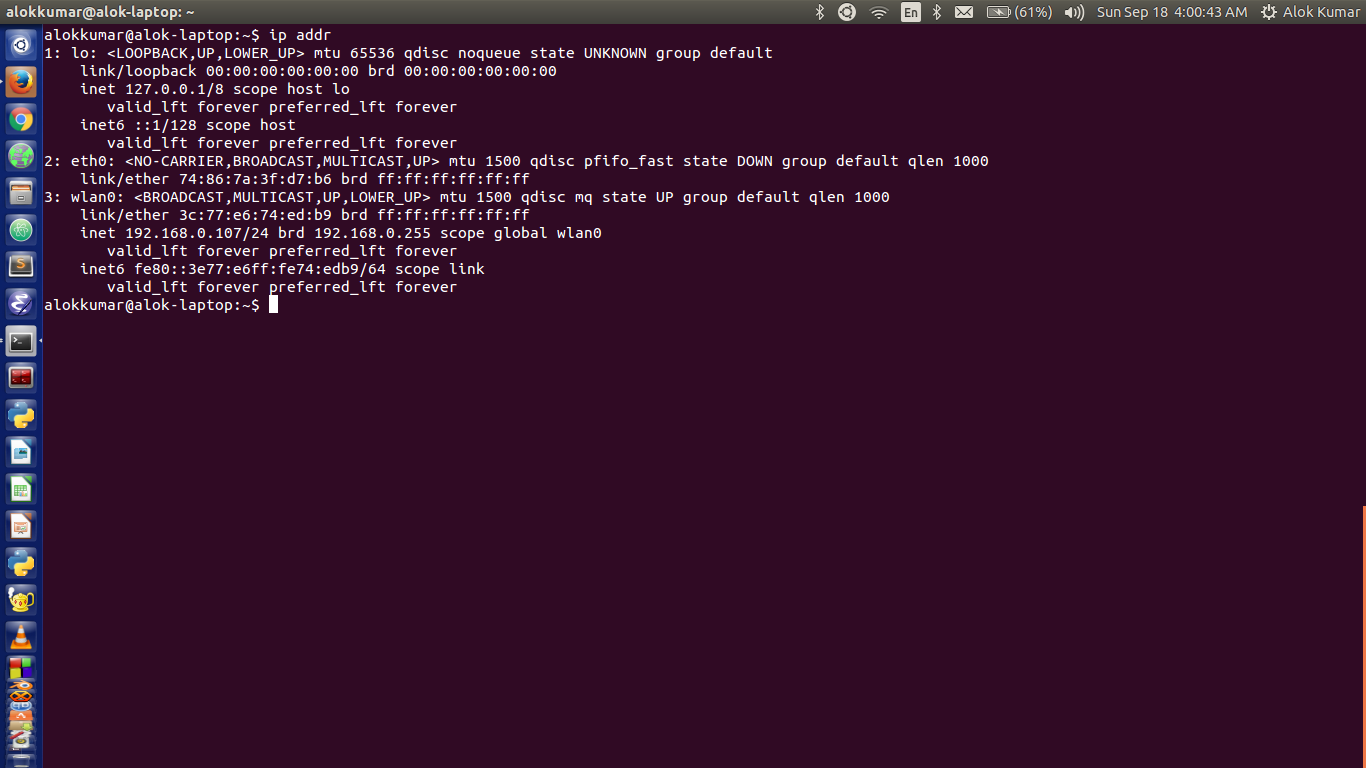
To run a TCP dump, you will need to use the tcpdump command in your terminal. First, specify the network interface that you wish to read packets from (e.g. eth0 or wlan0). You can then provide an expression to filter out specific packets (e.g. src port 80 or dst port 443). Finally, you can use the -w flag to save the packet data into a file for further analysis or use the -r flag to read data from a saved packet file instead of reading it from a network interface. You can also use additional flags such as -i and -n if necessary.
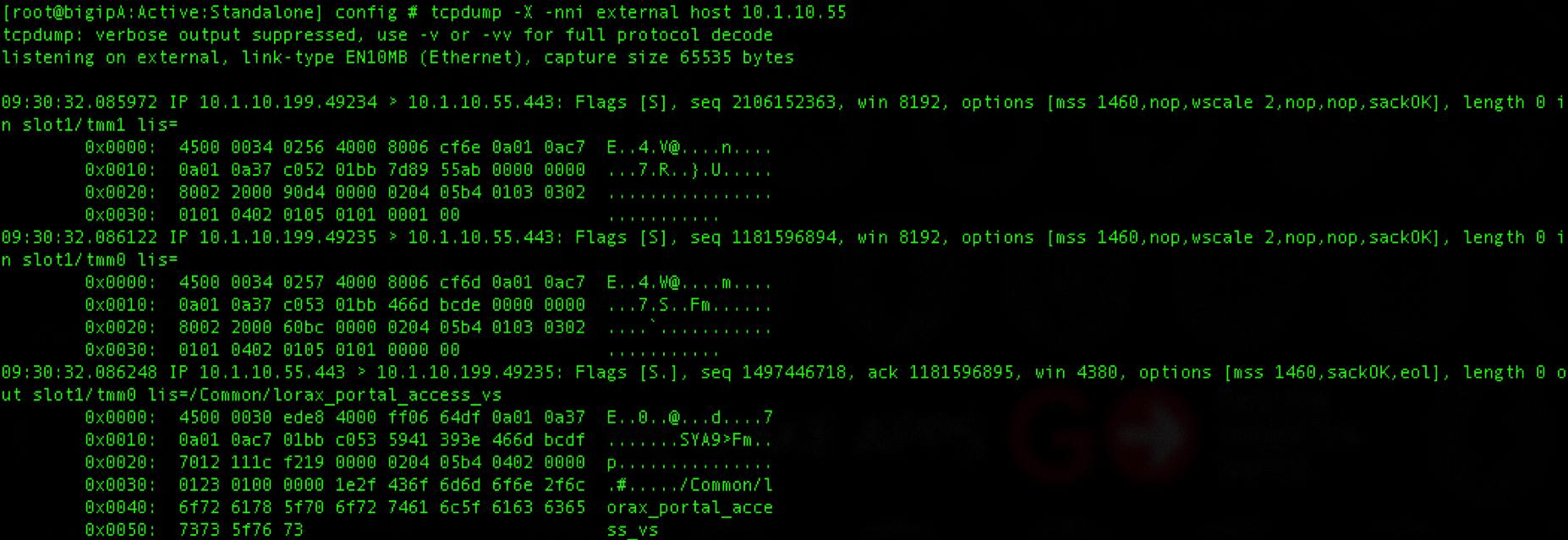
Source: clouddocs.f5.com
Setting Up a TCP Dump
Setting up a TCP dump involves several steps. First, you will need to download the tcpdump tool, which is available as an RPM package. After downloading the package, log in to your DSVA (Digital State VA) server via SSH as a DSVA user. The default password is “dsva”. Switch to the root user by typing in “sudo -s” into the command prompt. Upload the package to your DSVA under path:/home/dsva. Unpack the tar package and install the rpm packages using the following command: $rpm –ivh tcpdump-*.*.*-#.*x86_64.rpm.
Once installed, you can use tcpdump to sniff traffic going through a network interface on your DSVA server by typing in “tcpdump –i ” into the command prompt. For example, if you want to sniff traffic going through the eth0 interface, then you would type in “tcpdump –i eth0”. You can also capture packet data by adding additional flags like –w (write output to file), -X (print packets in ASCII), or -v (verbose mode).
After running tcpdump with flags of your choosing, you should be able to see packets being captured and displayed on your terminal window or saved in a file depending on what flags you used when running tcpdump.
Benefits of Using TCP Dump Over Wireshark
TCPDump is a powerful command line packet analyzer that allows users to capture and analyze network traffic. It is often used in place of Wireshark, the popular graphical packet sniffer, because of its ability to capture large amounts of data quickly and efficiently in real time. Furthermore, it can be used for remote captures over the network and does not require any additional software or hardware to operate.
One of the biggest advantages of using TCPDump over Wireshark is its lightweight nature. Since it operates from the command line, it does not require as much computing power and memory as Wireshark does, so there is less strain on your system resources when capturing packets. Additionally, since there is no graphical interface involved, TCPDump can be run without generating extra overhead traffic on the network, making it ideal for remote captures where you don’t want to bog down your network with unnecessary traffic.
Another advantage of using TCPDump over Wireshark is that it allows you to create custom filters that allow you to capture only the packets you are interested in. This makes it easier to narrow down your results and get more precise information about what’s happening on your network. Furthermore, since TCPDump operates from the command line, its output can be easily parsed into other programs or scripts for further analysis.
TCPDump is an invaluable tool for anyone who needs to capture and analyze network traffic quickly and efficiently without putting too much strain on their system resources or bogging down their networks with extra overhead traffic. Its ability to create custom filters makes it easy to narrow down results, while its lightweight nature and command line interface makes it ideal for remote captures or parsing into other programs or scripts for further analysis.
The Impact of Tcpdump on Firewall Security
Yes, tcpdump operates at the highest level of networking, meaning that it can detect traffic before it would hit firewalls. This is because tcpdump captures data directly from the network interface card, which is above the firewall. As a result, tcpdump can capture any packet that arrives on the network interface card – before it hits the firewall. So even though there may be firewalls in place, tcpdump will still be able to see all incoming and outgoing traffic.
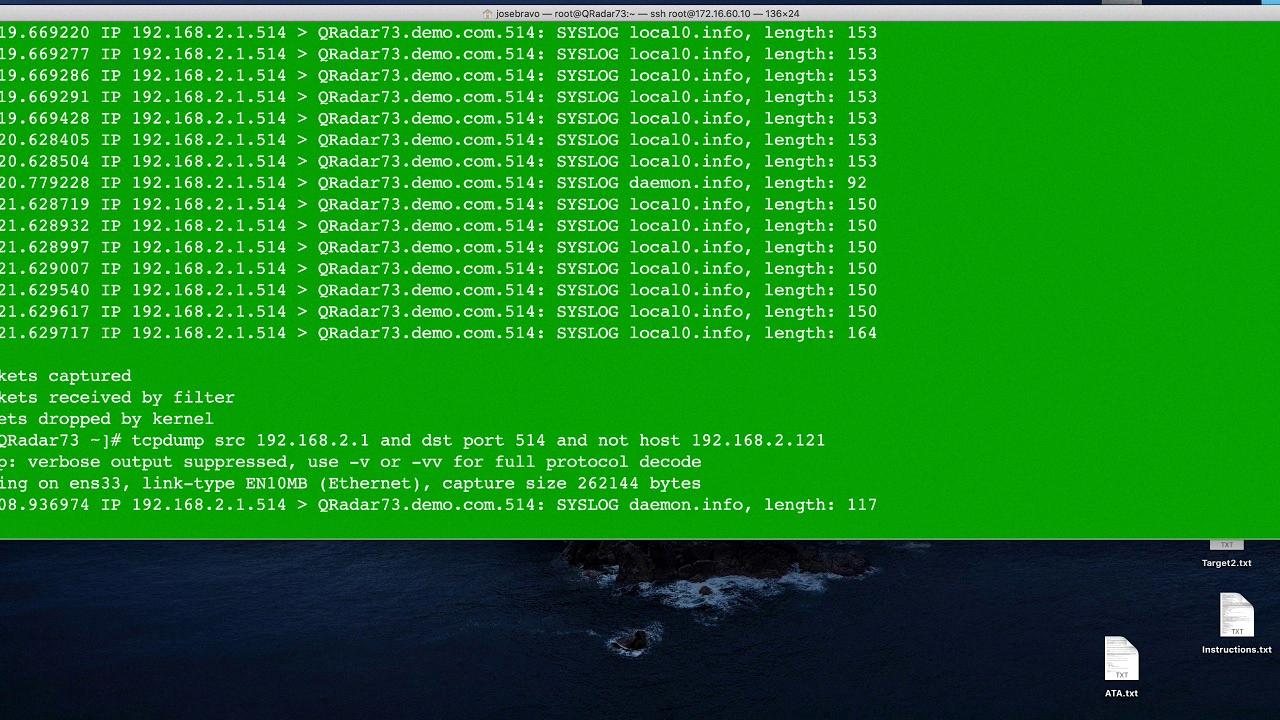
Source: youtube.com
Is TCPdump a Security Risk?
Tcpdump is a powerful packet-capturing tool that can be used to inspect and capture network traffic. It is a useful tool in many different scenarios but there are security risks associated with its use. The primary risk is that packet contents can be inspected, meaning that sensitive information may be visible to anyone with permission to run tcpdump. This could potentially lead to a data breach if the proper precautions are not taken. It is important to note that when working with payment card information, such as when meeting PCI-DSS audit requirements, appropriate security measures must be implemented when using tcpdump. In general, it is best practice to limit access to tcpdump and ensure that only authorized personnel have access to view captured packets.
Where Are Tcpdump Files Stored?
Tcpdump files are stored in the /shared/support directory on the BIG-IP system. It is important to ensure that the system has enough CPU and memory resources available before creating these files, as they require a substantial amount of system resources. The Configuration utility will create both a tcpdump file and a TAR file containing the tcpdump data. These files should both be stored in the /shared/support directory for easy access.
Disadvantages of Using Tcpdump
One of the major disadvantages of tcpdump is that it produces a large flat file containing text output, which can be difficult to manage and analyze. Additionally, tcpdump runs under the command line, meaning that users must be familiar with these commands in order to use them effectively. Furthermore, even though tcpdump allows for some filtering of data, it lacks the more advanced filtering and analysis capabilities available in other network monitoring tools. Finally, tcpdump can only capture traffic on a single interface at a time, making it difficult to capture traffic from multiple interfaces simultaneously.
Conclusion
In conclusion, tcpdump is an invaluable network packet analysis tool that enables users to analyze and capture data packets on Linux and most UNIX-type operating systems. This open-source command line interface tool does not require a graphical user interface, making it the ideal solution for capturing and analyzing packets passing through the node. tcpdump can decode data payloads if encryption keys are identified, as well as recognize data payloads from file transfers such as smtp, http, etc. With its powerful packet sniffing capabilities and easy-to-use command line interface, tcpdump is an invaluable tool for any network administrator looking to gain insight into their network traffic.