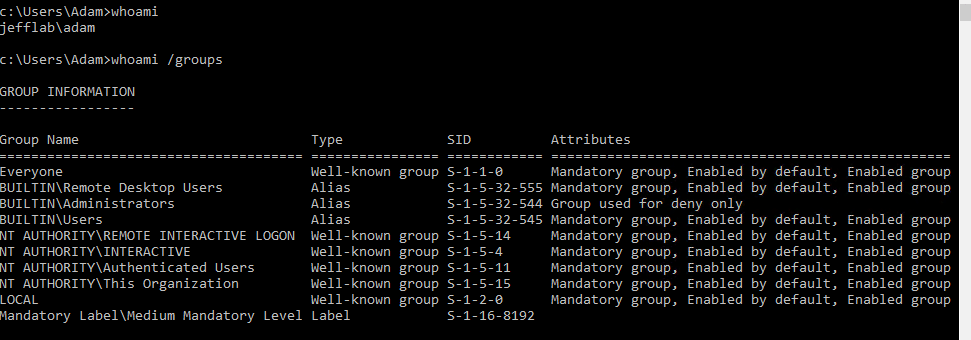
Passing the hash is a technique used by malicious actors to gain unauthorized access to computer systems and networks. In this attack, an adversary steals a “hashed” user credential and uses it to create a new session on the same network. By stealing the hash, they can gain access to systems without knowing the cleartext password—the actual string of characters that the user types to log in.
Passing the hash is only viable in networks using NTLM authentication as a protocol. The primary difference between pass-the-hash and pass-the-ticket is that Kerberos TGT tickets expire (10 hours by default), whereas NTLM hashes change only when the user changes their password. So a TGT ticket must be used within its lifetime, or it can be renewed for a longer period of time (7 days).
The main purpose of passing the hash is to facilitate lateral movement within a network, allowing an attacker to access other machines on the same network with credentials they have already obtained. To carry out this attack, attackers need various types of software tools such as Mimikatz or Metasploit Framework. These tools allow them to extract passwords from memory or generate NTLM hashes which can then be used to authenticate with other computers on the network.
It’s important for organizations to protect against pass-the-hash attacks by implementing best practices such as regularly changing passwords and enabling two-factor authentication. Additionally, organizations should consider deploying solutions such as privileged access management (PAM) solutions that provide additional layers of security beyond traditional passwords. These solutions can help mitigate pass-the-hash attacks by ensuring that even if an attacker is able to obtain credentials, they are unable to use them without additional authentication steps from privileged users.
Overall, passing the hash is an effective method for malicious actors looking for quick and easy ways into systems and networks. Organizations should take steps now in order to protect themselves from these types of attacks in order to ensure their data remains secure and their systems remain uncompromised.
Understanding the Concept of ‘Pass the Hash’
Pass the hash (PtH) is a technique used by hackers to gain access to a computer system without having the actual password. It works by stealing a “hashed” version of a user’s authentication credentials, usually their username and password, from one system and using it on another. This allows the hacker to authenticate with the second system as if they had the correct credentials, bypassing any login prompts. PtH attacks are often used to gain access to sensitive information or launch further malicious activities on a network.
Tools for Performing Pass the Hash
The most common tools used to perform a pass-the-hash attack are:
1. Mimikatz – a tool for extracting credentials from LSASS process memory, including password hashes, Kerberos tickets, and more. It can also be used to perform pass-the-hash attacks and inject forged credentials into processes and services.
2. PWDump – a command line utility for dumping Windows user account passwords from the registry in their hashed form. It can be used to perform pass-the-hash attacks by injecting the obtained hashes into authentication requests.
3. Fgdump – a graphical tool for dumping Windows user accounts passwords in their hashed form and can also be used to perform pass-the-hash attacks by injecting the obtained hashes into authentication requests.
4. LaZagne – an open-source tool for recovering various credentials from Windows systems, including password hashes that can be used in pass-the-hash attacks as well as other forms of credential theft such as Kerberos ticket injection and token manipulation.
5. Metasploit – an open-source exploitation framework that includes modules for performing various types of attacks, including pass-the-hash attacks using the obtained credentials.
Comparing Golden Ticket and Pass the Hash
The difference between a golden ticket and pass the hash lies in the method of credential dumping used to gain access. Pass the hash is a technique that involves using stolen credentials to authenticate with a system without cracking the original password. The stolen credentials are represented as a cryptographic hash value, which can then be used to authenticate. Golden tickets, on the other hand, involve using maliciously created tickets that bypass authentication altogether and grant access to any resource within an organization’s domain. While both methods allow for privilege escalation, golden tickets are considered more dangerous because they allow for complete control of a system or domain without requiring any additional authentication.
Preventing Pass The Hash Attacks
The most effective technique for preventing pass-the-hash attacks is to ensure that all systems are properly patched and updated with the latest security patches. Additionally, implementing strong authentication methods such as two-factor authentication or multi-factor authentication can help prevent attackers from successfully stealing credentials and using them in a pass-the-hash attack. Additionally, network segmentation and restricting server access to only those who need it can help limit the spread of an attack. Finally, using firewalls to block workstation-to-workstation traffic can help reduce an attacker’s ability to make lateral movements that are necessary for a successful pass-the-hash attack.
Conclusion
In conclusion, Pass the Hash (PtH) is a powerful attack vector that can be used to compromise an Active Directory account without ever knowing the account’s cleartext password. This type of attack is only viable in networks using NTLM authentication and should be prevented by implementing additional security measures such as enforcing strong password policies and implementing two-factor authentication. By taking these steps, organizations can reduce their risk of falling victim to a pass-the-hash attack.