Are you looking for a quick and easy way to get up to speed on the basics of Nmap? If so, then this Nmap cheat sheet is just what you need! This cheat sheet will walk you through the basics of Nmap, from port scanning to service fingerprinting. With this knowledge in hand, you’ll be able to perform basic network reconnaissance tasks in no time.
Nmap (short for “Network Mapper”) is an open-source security scanner used by systems and network administrators around the world. It is used to detect live hosts on a network and find open ports. It can also be used to scan for specific services running on those open ports.
To begin using Nmap, you must first understand the command line options available. The most common command line options are as follows:
-sT: Scans all TCP ports
-sU: Scans all UDP ports
-p: Specifies the port or range of ports to scan
-O: Detects the operating system type and version
–script: Runs a script against a target machine
–version-*: Checks for specific services running on targets
These are just some of the more common command line options available with Nmap; there are several more that can be used for various tasks. Once you become comfortable with these commands, you can use them together in order to achieve your desired results. For example, if you want to scan all TCP ports on a target machine, then use -sT followed by -p followed by the IP address of the target machine. Or if you want to find out which versions of Apache web server a target machine is running, then use –version-Apache in combination with other commands such as -p and -sT.
Now that we’ve gone over some of the basic command line options available with Nmap, let’s look at how it can be used in practice. Here are some examples of how Nmap can be used:
• Detecting live hosts on a network – Use -sn option followed by either an IP address or subnet mask
• Finding open ports – Use -p option followed by either an IP address or subnet mask
• Service fingerprinting – Use –version-* option followed by either an IP address or subnet mask
• Running scripts against targets – Use –script option followed by either an IP address or subnet mask
By understanding and utilizing these command line options correctly, you can quickly achieve your desired results when performing tasks such as host discovery, port scanning, service detection, and vulnerability assessment using Nmap. Keep in mind that there are several other options available that may help make your job easier depending on what task(s) you’re trying to accomplish. So if these examples don’t cover what you need to do, be sure to check out the official documentation on the Nmap website!
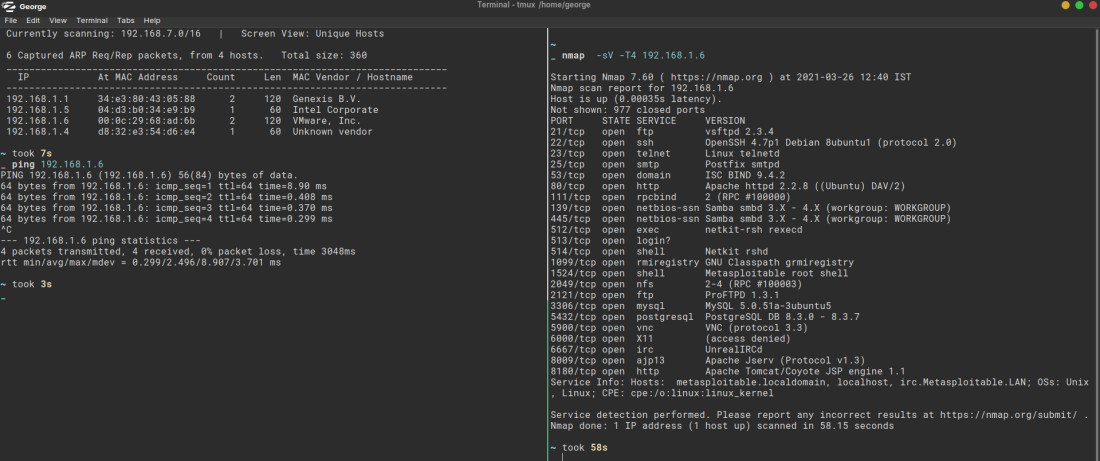
Understanding Nmap Cheat Sheet
A Nmap cheat sheet is a quick reference guide for the various features and options available in the Nmap network utility. It provides users with a concise overview of the basic commands, flags, and syntax for using Nmap to perform network discovery, port scanning, OS detection, version detection, and more. Additionally, it can be used as a resource to quickly look up specific information related to Nmap’s functionality. The cheat sheet also includes useful tips and tricks to help users get the most out of their Nmap experience.
Hacking with Nmap
Nmap can be used by hackers to gain access to unauthorized ports on a system, allowing them to probe and exploit vulnerabilities. With Nmap, hackers can identify open ports, services running on those ports, the operating systems of target machines, and even specific applications running on them. This allows hackers to easily identify potential weak points in a system’s security that they can use to gain access. Additionally, Nmap can be used to scan networks for hosts and check if they are vulnerable to certain exploits or malware. By using Nmap, hackers can quickly locate and target available weaknesses in the system they are targeting.
Consequences of Using Nmap
Yes, you can get caught using Nmap. It’s important to understand the laws of your country and the ISP or network that you are using before performing any type of network scanning. If you use Nmap without the proper authorization or in a way that violates local laws, the consequences can be severe. In some cases, it can even lead to civil or criminal penalties. To reduce your risk, make sure to read up on local laws and network policies before launching a scan. Additionally, always obtain permission from any organization whose systems you are scanning and ensure that all scans are conducted in an ethical manner.
Scanning an IP with Nmap
To scan an IP with Nmap, you need to open a terminal window and enter the command “nmap [IP address]”, replacing the IP address with the one you want to scan. This will produce a list of open ports and services associated with that IP address. You can add additional parameters to the command line in order to customize the scan – for example adding “-Pn” will skip host discovery, while “-sV” will perform service detection. Refer to the Nmap manual for more information on all of the available options.
Using Nmap Commands
Nmap is a powerful tool used in network exploration and security auditing. It allows you to scan your network for hosts, ports, and services. To use Nmap commands, you first need to open a terminal window and type the command “nmap” followed by the desired options.
Ping scanning can be done using the command “nmap -sP ”. This will return information on every active IP on your network. For port scanning, you can use the command “nmap -sT ” which will scan all ports on the target host by default, or “nmap -p ” to specify individual ports to scan. Host scanning can be done using the command “nmap -sL ” which will list all available hosts on your network. OS scanning can be done using the command “nmap -O ” which will attempt to detect the operating system of the target host.
Scanning popular ports can be done using the command “nmap –top-ports 20 ” which will scan for the top 20 most commonly used ports on that host. You can also output the results of Nmap scans to a file with various formats including XML, HTML, and TXT by adding “-oX, -oH, or -oN ” after your Nmap command respectively. Finally, you can disable DNS requests from being made during scans by adding “–DNS-servers 0” after your Nmap command.
What Limitations Does Nmap Have?
Nmap is a powerful tool for network administrators and security auditors, but there are some things it cannot do. It cannot determine whether a port is open if packet filtering prevents its probes from reaching the port. It also cannot penetrate firewalls, decrypt encrypted traffic, or identify the operating system or version of software running on a machine without additional information. Finally, since Nmap scans port one at a time, it is unable to detect vulnerabilities in applications that span multiple ports.
Identifying DNS Using Nmap
Yes, Nmap can identify DNS. By default, Nmap performs DNS resolution to identify the names of any systems that are scanned by IP address. This helps to make the results easier to read by providing more informative names instead of just IP addresses. However, doing this can also add time to the scanning process.
Can You Nmap Any IP Addresses?
Yes, you can Nmap any IP address. Nmap (Network Mapper) is a free and open-source tool for network exploration and security auditing that allows you to map out networks and scan them for vulnerabilities. It can be used to scan a single host or an entire range of IP addresses. To scan an individual host, simply provide the target IP address as an argument when running Nmap. To scan a range of IP addresses, you can use CIDR notation (e.g., 192.168.0.0/24) to specify the range of addresses to be scanned. You can also use wildcards (e.g., 192.168.*.*) to specify more specific ranges of IP addresses to be included in a scan.
Conclusion
In conclusion, Nmap is a powerful and versatile security tool that can be used to help protect your network from potential threats. It is important to use it responsibly and understand its legal implications before launching a scan. Knowing the subnet you are connected to is essential in order to use Nmap effectively, and understanding the IP address of your connection will help you in this process. With the right knowledge and caution, Nmap can be a great resource for keeping your network safe and secure.