Are you looking for a comprehensive checklist to ensure FISMA compliance? Look no further! FISMA (Federal Information Security Management Act) mandates organizations to implement the necessary security measures to protect government information, operations, and assets from malicious threats. To help organizations meet FISMA requirements, here is a detailed checklist of best practices:
1. Create an inventory of information systems and categorize them according to their risk level. This will help identify higher-risk areas that need more attention.
2. Develop a System Security Plan (SSP) outlining the security measures and policies in place to protect the system and its data.
3. Implement security controls based on the National Institute of Standards and Technology (NIST) 800-53 standards. These controls are essential for protecting sensitive information from unauthorized access, modification, or destruction.
4. Conduct risk assessments to understand potential risks and their impact on the organization’s operations, reputation, or financial losses.
5. Perform Certification & Accreditation (C&A) of all systems and services related to safeguarding government information resources against threats or attacks.
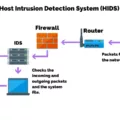
6. Monitor systems continuously for any anomalies that could indicate a security breach or attack. Use automated tools like Intrusion Detection Systems (IDS), Anti-Virus software, etc., to detect malicious activities in real-time and take appropriate measures to mitigate them quickly.
7 . Adopt NIST Cybersecurity Framework (CSF) functions such as ‘Identity’, ‘Protect’, ‘Detect’, ‘Respond’ & ‘Recover’ as part of your FISMA compliance strategy – this will help ensure your organization takes a proactive approach towards cybersecurity by mitigating risks before they occur rather than simply reacting after an incident has occurred.
8 . Keep evidence of how your organization is complying with FISMA requirements – this includes records of all risk assessments carried out, security policies implemented, etc., which can be used in an audit if required by federal agencies or other stakeholders.
9 . Ensure that all security controls are routinely tested so you know how effective they are at protecting your systems from potential attacks or vulnerabilities.
10 . Regularly update your SSP with new technologies or changes in regulations so that it remains up-to-date with the latest best practices.
Follow these steps diligently to ensure you have taken every measure necessary for achieving full FISMA compliance!

FISMA Compliance Requirements
FISMA compliance requires organizations to establish a comprehensive risk management program consisting of several components. First, organizations must maintain an inventory of all information systems and categorize them according to risk level. This will help organizations identify which systems are most vulnerable and require the most attention.
Second, organizations must develop and maintain a system security plan (SSP) that outlines the security controls and procedures used to protect their networks and information assets. The SSP should be based on the National Institute of Standards and Technology (NIST) Special Publication 800-53, which provides guidelines for selecting and implementing appropriate security controls.
Third, organizations must conduct periodic risk assessments in order to identify any potential threats or vulnerabilities associated with their systems. These assessments should be conducted on a regular basis and should be updated as new technologies or threats emerge.
Fourth, organizations must complete certification and accreditation (C&A) for each system in order to ensure that it meets all applicable security requirements. During C&A, an independent third party evaluates the system against a set of standards in order to verify its compliance with applicable regulations and policies.
Finally, organizations must conduct continuous monitoring of their systems in order to detect any changes or anomalous activity that could indicate a security breach or other malicious activity occurring on the network. This includes regularly scanning for vulnerabilities, monitoring user activities, logging access attempts, etc., as well as responding swiftly to any alerts generated by these activities.
Understanding FISMA Compliance
FISMA compliance is the process of following the Federal Information Security Management Act (FISMA) guidelines for protecting government information, operations, and assets from potential threats. It requires federal agencies to develop, document, and implement an information security program that includes security policies, procedures, standards, and controls. The Federal Information Security Modernization Act of 2014 (FISMA) provides a comprehensive framework for protecting government information systems from unauthorized access, use, disclosure, disruption, modification, or destruction. Compliance with FISMA requirements is mandatory for all federal agencies with no exceptions.
The framework requires agencies to conduct annual risk assessments to identify vulnerabilities in their IT systems and develop plans of action to correct these issues. Agencies must also ensure that their IT systems are regularly monitored and updated to maintain a high level of security. Additionally, FISMA requires agencies to provide training on cybersecurity measures and regularly report any security incidents to the Department of Homeland Security’s US-CERT.
Overall, FISMA compliance is a critical tool for strengthening the security posture of government networks and protecting citizens’ personal data from malicious actors. By adhering to FISMA guidelines, federal agencies can better safeguard their assets from potential cyber threats and ensure compliance with applicable laws and regulations.
Best Practices for FISMA Compliance
FISMA compliance best practices involve implementing a comprehensive security program to protect your organization’s information systems. This includes performing periodic risk assessments to identify, prioritize and remediate any security gaps; maintaining evidence of FISMA compliance; and regularly testing the effectiveness of your security controls and policies. A few additional best practices include developing a written security policy, training staff on security protocols, establishing an incident response plan, monitoring user access levels and activities, encrypting sensitive data, implementing multi-factor authentication for remote access, and monitoring systems for anomalous behavior. By following these best practices, you can ensure that your organization’s information systems are securely protected in accordance with FISMA guidelines.
Understanding FISMA Metrics
The FISMA metrics are a set of measures used to assess an organization’s compliance with the Federal Information Security Modernization Act (FISMA). The metrics measure an organization’s progress in implementing the five functions of the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF): Identity, Protect, Detect, Respond, and Recover.
In order to fulfill their FISMA reporting requirements, organizations must measure their performance on each of these five functions using specific metrics. For example, for the Identify function, organizations must measure their ability to identify and document components of their information systems and assets. For the Protect function, organizations must assess the effectiveness of their security controls used to protect against data breaches and other cyber threats. And for the Detect function, organizations must measure their ability to detect malicious activities within their systems. Each function has its own set of specific metrics that organizations must report on in order to demonstrate compliance with FISMA requirements.
The General Services Administration (GSA) collects FISMA data from federal agencies in order to report and monitor progress on FISMA compliance across government-wide initiatives. This helps ensure that all federal agencies are meeting standards for protecting digital assets from cyber threats and other malicious activities.
Understanding the FISMA Scorecard
The Federal Information Security Modernization Act (FISMA) scorecard is a tool used to evaluate the effectiveness of an agency’s information security program. It provides a comprehensive assessment of an agency’s cybersecurity posture across different areas of concern, including system security planning, risk assessment, identity and access management, incident response management, and security monitoring. The scorecard measures the agency’s performance in each of these areas of concern and identifies any weaknesses that could be exploited by cybercriminals. It also provides agencies with recommendations for improvement in order to ensure the overall security of their networks and systems. By regularly collecting and evaluating data from FISMA scorecards, federal agencies can ensure they are meeting their security objectives and defending their networks against potential threats.
Preparing for a FISMA Audit
Preparing for a FISMA audit requires proactive planning and effective implementation of security measures. Here are the steps to take in order to ensure you are ready for the audit:
1. Access Control: This is the first step in preparing for a FISMA audit. Make sure that all access controls are set up correctly and that any external or internal access requests are appropriately tracked and monitored.
2. Awareness and Training: Ensure that all users understand their roles and responsibilities surrounding information security, as well as how to protect sensitive data from unauthorized access or manipulation. Regularly evaluate your training program and adjust it if necessary.
3. Audit and Accountability: Establish a system for ongoing security auditing and monitoring, including reviews of network logs, system configurations, user activities, etc., to identify any potential risks or threats. Additionally, keep detailed records of all security-related incidents to ensure full accountability in case of an audit.
4. Configuration Management: Establish policies and procedures for configuring systems securely with regular reviews to verify compliance with regulations. Document any changes made to your systems so you can demonstrate that they remain compliant with FISMA requirements during the audit period.
5. Contingency Planning: Develop a comprehensive disaster recovery plan that outlines how your organization will respond in the event of a security breach or other unforeseen incident involving sensitive data or systems. The plan should include procedures for responding quickly, minimizing disruption, preserving evidence, restoring services, etc.
6. Identification and Authentication: Put in place strong authentication mechanisms for verifying user identities before providing access to sensitive data or systems (e.g., multi-factor authentication). All user credentials should also be regularly reviewed and updated based on established policies/standards (e.g., password complexity requirements).
7. Incident Response: Establish an effective incident response process with clear roles/responsibilities so that you can respond quickly and effectively when a security incident occurs (e.g., malware infections, or network intrusions). Ensure you have procedures in place for identifying the root cause of an incident, taking appropriate corrective actions, notifying relevant stakeholders (e.g., customers), etc.)
8 Maintenance: Develop a maintenance program that includes regular patching/updates of software/firmware as well as security assessments/audits to identify potential vulnerabilities before they can be exploited by malicious actors
Does the Federal Information Security Management Act Require the National Institute of Standards and Technology?
Yes, FISMA requires organizations to comply with the NIST guidelines and standards outlined in NIST Special Publication 800-53. This document provides a set of security controls that must be implemented in order to meet the requirements of the Federal Information Security Management Act (FISMA). These security controls are regularly updated and published by NIST, meaning that federal agencies must comply with any updates within one year of their publication. The NIST security controls form the basis for other government regulations such as FedRAMP, DFARS, CJIS, HIPAA, and FedRAMP +.
Understanding FISMA Audits
FISMA audits are conducted by the federal government to evaluate an organization’s adherence to the Federal Information Security Management Act (FISMA). FISMA is a law that outlines standards for protecting government information, operations, and assets from potential security threats. The goal of a FISMA audit is to ensure that an agency follows these standards and has implemented appropriate controls to protect its sensitive information. During a FISMA audit, an auditor will review an agency’s policies and procedures related to data security, access control, system management, and incident response. They will also assess the organization’s implementation of technical safeguards such as firewalls, intrusion detection systems, and encryption. The results of the audit are used by agencies to identify any weaknesses in their security posture so they can be addressed before they become a problem.
Conclusion
In conclusion, FISMA compliance is a critical requirement for all government agencies. A comprehensive FISMA compliance checklist should include inventory management, categorization of information and systems according to risk levels, system security plans, implementation of applicable security controls, risk assessments, certifications and accreditations, and continuous monitoring. Following best practices such as conducting periodic risk assessments and evaluating the effectiveness of security controls regularly can help ensure that your agency remains compliant with FISMA requirements. Additionally, aligning your FISMA metrics to the five functions outlined in the NIST Cybersecurity Framework will ensure that your agency is meeting all reporting requirements.