Today, organizations of all sizes are challenged to remain secure from cyber threats. To ensure that their security posture is up-to-date and effective, it’s important for organizations to assess their systems regularly. Breach and Attack Simulation (BAS) Tools offer a powerful way to do just that.
BAS tools enable organizations to gain a deeper understanding of their security posture vulnerabilities by automating the testing of various threat vectors such as external and insider attacks, lateral movement, and data exfiltration. This type of testing measures and improves cyber resilience by continuously and automatically testing the efficacy of your defenses.
As one of the most effective solutions for security control assessment, BAS has become an essential tool in many organizations’ cyber security toolset. Unlike red teaming which is human-led or manual attacks, BAS employs automation which can be more cost-effective and efficient in finding vulnerabilities in the hardware, software, and human aspects of a security system. Security experts can then review these findings in order to understand the risks facing an organization more thoroughly.
Organizations should take into account when considering acquiring a BAS solution including scalability (number of attack vectors) as well as company size when determining the cost associated with such implementations. Pricing for BAS tools generally ranges from $40,000-$500,000 depending on these factors.
Breach & Attack Simulation Tools are becoming increasingly popular as organizations strive to stay ahead of cyber threats by regularly assessing their systems with automated testing of various threat vectors. With this powerful tool at your disposal, you can gain a better understanding of your organization’s risk profile while simultaneously improving your overall cyber resilience.

The Benefits of Using a BAS Tool
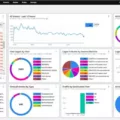
A Breach and Attack Simulation (BAS) tool is a powerful security solution that helps organizations identify potential security vulnerabilities. By running automated tests against threat vectors such as external and insider, lateral movement, and data exfiltration, BAS tools can provide an in-depth assessment of an organization’s security posture. These tools are often used to identify gaps in existing security controls, as well as to validate the effectiveness of new security protocols. By providing actionable insights into potential weaknesses, BAS tools can help organizations reduce the risk of a successful cyber attack.

Source: itsecurityguru.org
The Role of BAS in Security
Breach and Attack Simulation (BAS) is an automated security testing solution that helps organizations identify and improve the effectiveness of their cyber security controls. It is designed to continuously test the organization’s cyber resilience by simulating real-world attacks and breaches, providing organizations with meaningful insights into the efficacy of their security defenses. BAS helps organizations identify areas of weakness in their systems, giving them the opportunity to strengthen those areas before they are exploited by malicious actors. By helping organizations assess and improve their cyber defenses, BAS provides a crucial layer of protection against potential threats and helps ensure that organizations are better prepared for any future attack.
The Cost of Breach and Attack Simulation
The cost of breach and attack simulation varies greatly based on the size of the company and the number of attack vectors. A smaller company may spend from $40,000 to $150,000 for a complete solution, while a larger company with more attack vectors could pay anywhere from $150,000 to $500,000.
Breach and attack simulation is an important investment for any organization as it helps provide security assurance against malicious actors. It can simulate multiple types of attacks against an organization’s networks and applications to assess vulnerabilities before they are exploited by adversaries. The cost includes the initial setup and implementation of the simulated attack environment as well as ongoing maintenance and support. This can include training personnel on how to use the system, deploying new attack scenarios, performing an analysis of results, and providing recommendations on how to remediate any detected weaknesses. With these costs in mind, organizations should carefully consider their needs when choosing a breach and attack simulation platform.
Understanding the Benefits and Functionality of BAS
BAS stands for Business Activity Statement and is used by businesses registered for GST (Goods and Services Tax) to report their income and expenses. A BAS statement must be lodged on a monthly, quarterly, or annual basis, depending on the size of the business.
The statement is made up of several sections which include sales, purchases, GST collected and paid out, capital purchases, and other information. Sales need to be reported in the same period as when they were invoiced. Purchases are reported in the same period that payment was made.
GST collected includes all money collected from customers that include GST and needs to be reported on the BAS statement. GST paid includes all money paid to suppliers that include GST and needs to be reported on the BAS statement. Capital purchases are assets or items that cost more than $1000 (excluding GST) and should also be included in the BAS statement.
Once all of these components are calculated, you can use the available data to calculate your net amount due or refundable from your account with the ATO (Australian Tax Office). Business owners must ensure that their BAS statements are accurate and up-to-date in order to avoid any penalties or interest charges from being incurred.
The Three Main BAS Protocols
The three main Building Automation System (BAS) protocols are BACnet, LonWorks, and Modbus. BACnet is a data communication protocol designed specifically for building automation and control networks. LonWorks is a platform-independent network protocol designed for distributed intelligence in building automation systems. Modbus is an open communication protocol commonly used in industrial automation applications. Additionally, OPC (OLE for Process Control) is also becoming increasingly popular as a BAS communication protocol due to its ability to support different types of hardware and software applications over all major networks.

Source: csoonline.com
Conclusion
In conclusion, Breach and Attack Simulation (BAS) Tools are essential tools for organizations to improve their cyber resilience. BAS provides automated testing of threat vectors, such as external and insider threats, lateral movement, and data exfiltration. This allows organizations to identify vulnerabilities in their security systems, enabling them to take proactive measures to protect their assets from potential threats. With prices ranging between $40,000 and $500,000 based on company size and a number of attack vectors, BAS is an effective solution for security control assessment that can provide long-term protection for any organization.