Web Cache Poisoning is a type of cyber attack that can be used to harm users by inserting fake information into a domain name system (DNS) cache or web cache. This attack works by diverting the traffic from a legitimate server to a malicious/dangerous server, which can lead to serious security issues.
The goal of web cache poisoning is to gain access to sensitive data, such as passwords and financial information, or to hijack web applications. Unfortunately, this type of attack can be difficult to detect because the malicious content is stored in the cache instead of on the server. As a result, it can remain undetected for long periods of time and cause significant damage.
In order to protect against web cache poisoning attacks, there are some important steps that should be taken. First and foremost, it’s important not to trust any data in HTTP headers. Additionally, never return HTTP headers to users in cached content and always sanitize user-supplied data when necessary. It’s also important to only cache static files and static content as dynamic content may contain malicious code that could be used for an attack.
In addition to these steps, using web application firewalls (WAFs) is essential when it comes to preventing attacks like web cache poisoning. WAFs are designed specifically to monitor incoming traffic and detect suspicious activity before it can do any damage. By deploying one of these solutions at your organization’s perimeter, you can dramatically reduce the risk posed by this type of attack.
Finally, it’s important that organizations stay up-to-date with the latest security news regarding cyber threats such as web cache poisoning so they can take proactive steps against them before they become an issue. By staying informed and implementing effective security measures, organizations can better protect themselves against this type of attack and help ensure their data remains secure from malicious actors.
Understanding Web Cache Poisoning
Web cache poisoning is a form of attack performed by malicious actors to inject specially crafted data into a web server’s cache memory. This data can be used to manipulate the server into sending malicious HTTP responses back to the user. It is an effective way of exploiting website vulnerabilities and can lead to the exposure of sensitive information such as usernames, passwords, and other personal details. Web cache poisoning can also cause websites to crash or become unavailable, leading to the disruption of services and financial losses for businesses. It is important for website owners and administrators to be aware of this threat and take appropriate measures to protect their sites from being attacked in this way.
Mitigating Web Cache Poisoning
To mitigate web cache poisoning, it is important to take the following steps:
1. Do not trust data in HTTP headers. Always validate user-supplied data and sanitize it before returning it in HTTP headers.
2. Cache only static files and static content, as dynamic content can be more easily tampered with by malicious actors.
3. Use encryption protocols such as HTTPS or TLS to protect data transmitted over the network, as plain text information can be vulnerable to interception and manipulation.
4. Implement a web application firewall (WAF) to monitor for malicious requests and filter out suspicious activity.
5. Monitor your web traffic for any unusual activity or requests, and investigate any suspicious behavior immediately.
6. Ensure that all software components used on the web server are up-to-date with the latest security patches and updates to reduce the risk of exploitation of known vulnerabilities.
The Effects of Cache Poisoning
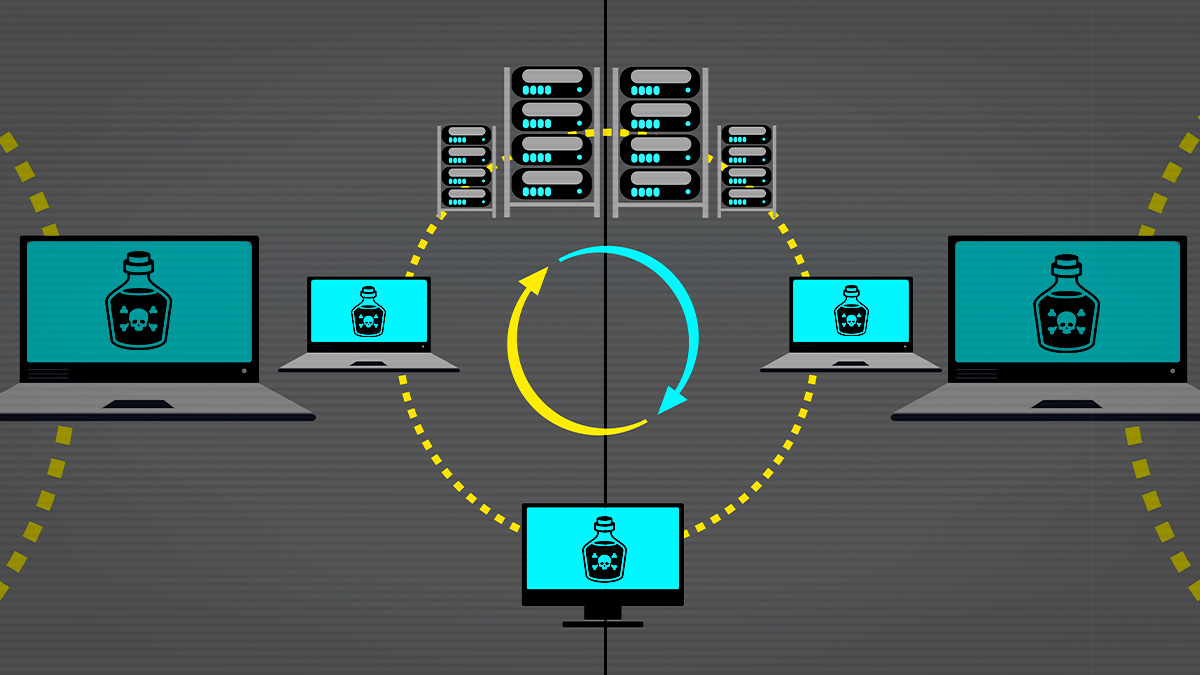
Cache poisoning is a technique used by malicious actors to hijack and redirect users to malicious or dangerous servers. It works by corrupting the DNS cache (domain name system) or web cache with false information. The attacker inserts fake data into the DNS or web cache, which then points the user to a malicious server instead of the legitimate one.
This type of attack is most commonly seen in DNS cache poisoning, where an attacker manipulates records in the DNS system to point users to malicious sites. The attacker can also manipulate records in the web cache, which can lead to users being redirected to malicious websites, even if they type in a legitimate URL. In either case, attackers are able to redirect users away from legitimate sites and onto their own malicious ones.
Cache poisoning attacks can have devastating consequences for victims, as they can be tricked into visiting fraudulent websites and downloading malware or giving up personal information. To prevent these attacks from occurring, it’s important for companies and organizations to secure their networks by using strong authentication methods and using technologies such as DNSSEC (Domain Name System Security Extensions). Additionally, it’s important for users to be aware of how caching works so that they are not tricked into visiting malicious websites or downloading malware.
Example of Cache Poisoning
An example of DNS cache poisoning is when an attacker sends a forged response to a caching DNS server, telling it that the IP address of bank.example.com is 198.18.8.17 instead of its actual IP address, 192.0.2.193. This allows the attacker to redirect legitimate traffic intended for bank.example.com to evil.example.com, which is hosted on 198.18.8.17 instead, allowing them access to confidential information or the ability to perform malicious actions on the user’s behalf without their knowledge or consent.
Conclusion
In conclusion, web cache poisoning is a type of cyber attack that can be used to harm users by inserting malicious or fake information into the DNS or web cache. It can be performed by hacking Wi-Fi connections or through a VPN or proxy connection. To protect against this type of attack, it is important to ensure that HTTP headers are not trusted and that user-supplied data is sanitized before it is cached. Additionally, only static files and content should be cached in order to avoid any malicious scripts being executed in the victim’s browser. By taking these precautions, organizations can effectively reduce their risk of falling victim to web cache poisoning.