In today’s digital world, privileged accounts are essential for organizations to access important data and systems. Unfortunately, these accounts are often targeted by malicious actors who could use them to gain unauthorized access and cause significant damage. This is why privileged password management is so important.
Privileged password management is a system that helps organizations protect their sensitive data by controlling access to privileged accounts. It can be used to manage all the passwords used to access administrative systems, databases, and applications. It also keeps track of when privileged passwords are changed and who has access to them. With proper implementation, this kind of system can greatly reduce the risk of unauthorized access and data breaches.
The key components of a successful privileged password management system include:
• Strong password policies – These ensure that users create strong passwords that are difficult for attackers to guess or crack. Password policies should also require regular changes in order to reduce the risk of compromised credentials.
• Access control – Privileged access should be restricted based on user roles and responsibilities. This ensures that only authorized users have access to sensitive accounts and data.
• Auditing – A good privileged password management system should monitor user activity in order to detect any suspicious or unauthorized behavior.
• Authentication – Organizations should implement two-factor authentication or multi-factor authentication as an added layer of security for privileged accounts.
• Encryption – All sensitive data should be encrypted in order to protect it from theft or misuse.
By implementing these components, organizations can ensure that their sensitive data is protected from potential attackers while still allowing authorized users easily access what they need when they need it.
With the right controls in place, organizations can keep their systems secure while still allowing users easy access to the resources they need to do their jobs effectively and efficiently.
The Benefits of Privileged Account Management
Privileged Account Management (PAM) is a security discipline that ensures that only authorized personnel have access to privileged accounts, which are accounts with elevated permissions or access rights. PAM solutions control, monitor, and audit privileged account activities in order to protect organizational systems from unauthorized access and misuse.
In a typical corporate environment, privileged accounts are used by system administrators, IT support staff, and other personnel who require special privileges for their job roles. These accounts usually have unrestricted access to sensitive data and resources, such as databases, applications, and configuration files. As such, it’s essential that these accounts are managed securely and monitored closely.
The main goals of Privileged Account Management are to limit the number of users with privileged access to critical systems; ensure that all privileged user activity is tracked and logged; enforce the use of strong authentication measures; implement role-based access control (RBAC); detect suspicious activity; protect against malicious actors gaining entry into the network; and provide an audit trail for compliance purposes.
PAM solutions typically employ several key technologies: privilege elevation, password vaulting/credential management, session monitoring/recording, single sign-on (SSO), multi-factor authentication (MFA), application control/whitelisting, and vulnerability scanning. These technologies help organizations secure their systems by controlling who has access to what resources at any given time.
By implementing a comprehensive Privileged Account Management solution, organizations can ensure that only authorized personnel have access to sensitive information or data while also providing an audit trail of all activities associated with those credentials. In doing so, they can significantly reduce the risk of data breaches or other malicious attacks on their networks.

Source: n-o-v-a.com
Uses of PAM Tool
A privileged access management (PAM) tool is used to enhance security and protect against unauthorized access to sensitive data, systems, and applications. PAM tools provide an additional layer of protection by managing the credentials and privileges associated with privileged user accounts. These tools help organizations restrict access to only authorized personnel while tracking and auditing user activity.
PAM tools also allow organizations to enforce least privilege principles, by granting users the minimum privileges required to perform their tasks in the most secure manner possible. This helps ensure that only those who need privileged access are granted it, reducing the risk of malicious actors exploiting vulnerable accounts or activities that could put an organization’s data at risk.
In addition, PAM tools can automate security operations and processes, such as password rotations and key management, which can help streamline administrative tasks while ensuring that all operations are securely conducted. Ultimately, PAM tools offer organizations a more efficient way of managing privileged user accounts, reducing the potential for breaches or misuse of credentials.
The Benefits of Privilege Management in Cyber Security
Privileged access management (PAM) is an important component of cyber security that seeks to control and protect privileged accounts, users, processes, and systems. This is done by regulating who has access to privileged accounts and what they can do with them. PAM helps organizations ensure that only authorized personnel have the necessary permissions to perform certain tasks, preventing unauthorized access and misuse of data by malicious actors. It also helps organizations detect any suspicious activity related to these privileged accounts. This can include monitoring for abnormal user behavior or changes in the system’s configuration or settings. By providing a single point of control for all privileged accounts and activities, PAM can help organizations reduce the risk of a data breach or other security incident.
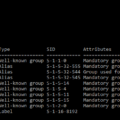
Examples of Privileged Accounts
Privileged accounts are accounts with elevated access privileges on a system. These accounts allow the user to perform administrative functions that regular users cannot. Examples of privileged accounts include Local Windows Admin accounts, Domain Admin accounts, Unix root accounts, Cisco enable, and many others.
Local Windows Admin accounts are used to manage local Windows systems. These accounts have full access to the system, including the ability to install software, manage users and groups, and modify system settings.
Domain Admin accounts are used to manage a domain in Active Directory. They can be used to create and delete users, reset passwords, manage permissions, and more.
Unix root accounts provide administrative access to Unix-based systems such as Linux and macOS. With root access, users can install software packages, manage user privileges, create files or folders, and configure network settings.
Cisco enables is the default account for many Cisco devices such as routers or switches. This account allows users to configure settings for these devices such as routing tables or firewall rules.
Privileged accounts are essential for managing computer systems but also pose a security risk if not managed properly. It is important to ensure that these accounts have strong passwords and limited access rights so that only authorized personnel can use them.

Source: dsm.net
Types of Privileged Accounts
Privileged accounts are accounts that have the highest level of access to a computer system, network, or application. They are used to manage and maintain a system or network, and typically provide unrestricted access to confidential information. There are two main types of privileged accounts: Root/Administrator Accounts and Domain Administrator Accounts.
Root/Administrator Accounts are the most powerful type of privileged account and grant unrestricted access to the system, allowing users to install and remove software, modify configurations, create new users or delete existing ones, etc.
Domain Administrator Accounts provide full control over an Active Directory (AD) domain. This type of account allows users to modify the domain’s security policies, create user accounts, deploy applications across the domain, as well as other tasks related to managing a Windows domain environment.
Comparing the Best PAM Tools
The best Privileged Access Management (PAM) tool is highly dependent on the individual needs of an organization. Therefore, there is no one-size-fits-all solution. Some of the top PAM tools are StrongDM, BeyondTrust Privileged Remote Access, Devolutions Remote Desktop Manager, AWS Secrets Manager, Ermetic, CyberArk Privileged Access Manager, BeyondTrust Password Safe, and Ping Identity.
StrongDM is an enterprise-grade system that provides access control for servers and applications. It uses machine learning to detect suspicious user activity and enforce security policies. BeyondTrust Privileged Remote Access allows secure remote access to privileged accounts and resources from anywhere in the world. Devolutions Remote Desktop Manager provides secure access to multiple systems from a single console. AWS Secrets Manager enables organizations to store and manage their secrets securely in the cloud. Ermetic helps organizations automate processes for managing privileged access requests and access revocations. CyberArk Privileged Access Manager provides centralized policy management for controlling privileged access to critical systems across an organization’s infrastructure. BeyondTrust Password Safe automates password management tasks by providing a secure vault for storing privileged account credentials. Finally, Ping Identity offers a comprehensive suite of identity and access management solutions that enable organizations to quickly deploy authentication services in hybrid IT environments.
Ultimately, the best PAM tool will depend on your organization’s specific requirements and needs. It is important to evaluate each tool carefully before making a decision so that you can ensure it meets your organization’s needs and provides a secure environment for managing privileged accounts and resources.
Understanding Privileged Access Management for Dummies
Privileged access management (PAM) is a system designed to help organizations protect their critical data and systems by controlling the access privileges of users. PAM helps organizations keep track of who has access to what, control user privileges, and detect unauthorized activities or privilege abuse.
At its core, PAM is about ensuring that only the right people have access to the right resources – such as systems, applications, networks, and databases – at any given time. This requires organizations to know who has access to what and when. To do this effectively, organizations need a comprehensive strategy for managing privileged accounts and credentials.
PAM solutions use advanced authentication mechanisms such as multi-factor authentication or biometrics for the secure authentication of privileged users. Additionally, PAM solutions can monitor user activity in real-time to detect suspicious activities or privilege abuse. This enables security teams to respond quickly to potential threats and safeguard critical data and systems from malicious actors.
Implementing Privileged Access Management
Privileged Access Management (PAM) is a security strategy that helps organizations protect and monitor privileged accounts, credentials, and access to sensitive information. To implement PAM, organizations should first identify all privileged accounts, users, and systems that need to be monitored. Next, organizations should create policies and procedures around access control for those users and systems. Some of the steps that can help secure these accounts include:
1. Establishing strong authentication for privileged users by utilizing two-factor authentication or other advanced authentication methods.
2. Enforcing least privilege principles to limit access to only what is necessary
3. Monitoring user activities to ensure they are not abusing their privileges
4. Providing training to privileged users on proper usage of their privileges
5. Establishing rules for password management such as length, complexity, expiration time, etc
6. Implementing session management controls such as controlling the duration of a user’s session or limiting concurrent sessions
7. Logging all activities performed by the privileged users
8. Auditing system logs regularly
9. Implementing separation of duties between different roles within the organization
10. Imposing restrictions on who can access what resources at what times

Source: aisllp.com
Conclusion
In conclusion, Privileged Account Management is a critical component of any organization’s cybersecurity strategy. It is used to protect privileged accounts, credentials, and operations that grant elevated levels of access to systems and networks. PAM tools are used to store and manage credentials, while also providing audit trails for tracking changes made to accounts. With the right strategies and technologies in place, organizations can reduce their privileged access risks and maintain secure IT environments.