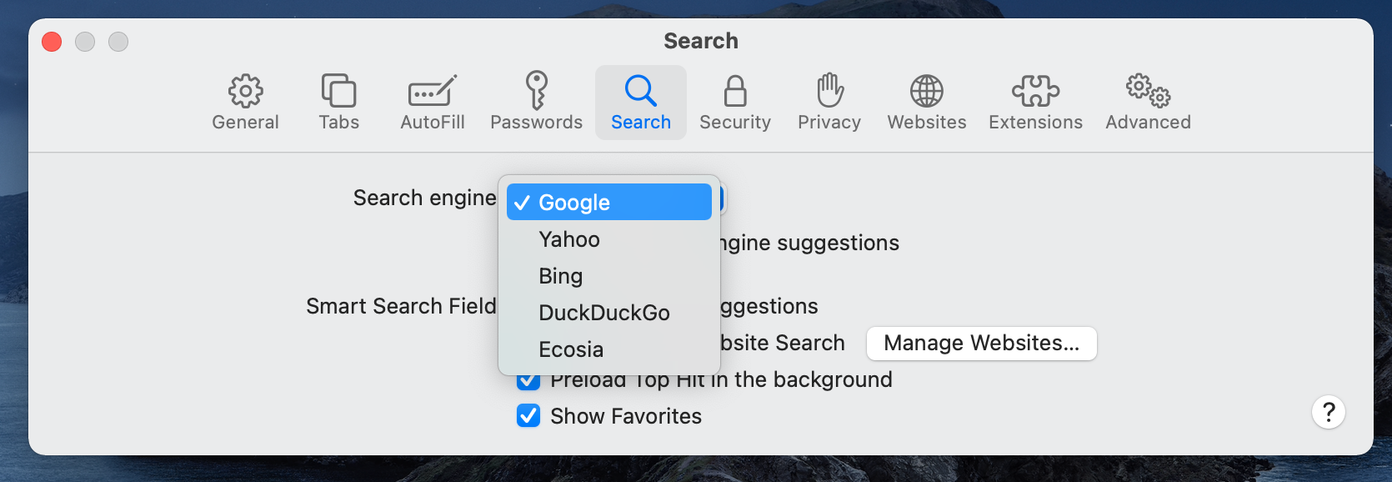
How To Change Safari From Yahoo To Google
Safari is a web browser created by Apple that runs on Mac, iPhone, iPad, and iPod. It’s designed to make surfing the web easy and secure. It uses Apple’s WebKit engine which means you get the same experience across all devices you own. The browser also uses iCloud so all your bookmarks, history, and passwords … Read more